Imagine a world where digital threats evolve faster than most defenses can keep up. For many organizations, the risk is no longer if a cyber incident will occur, but when. This guide is designed to help leaders and teams confidently face these challenges by leveraging a cyber advisor. You’ll discover practical steps to secure your business, reduce risk, and build resilience.
Inside, we’ll break down the essential stages: understanding the cyber advisor role, assessing your needs, building a security roadmap, implementing solutions, and optimizing for the future. Let’s bring clarity to cybersecurity and empower you to act.
Understanding the Role of a Cyber Advisor
In today’s rapidly evolving threat landscape, organizations face challenges that go far beyond traditional IT management. A cyber advisor serves as a specialized expert, guiding businesses through the complexities of digital risk, compliance, and resilience. Understanding this role is fundamental to building an effective security strategy that adapts to new threats and regulations.

What is a Cyber Advisor?
A cyber advisor is a strategic partner who helps organizations identify, assess, and mitigate cybersecurity risks while aligning security initiatives with business objectives. Unlike IT support or managed service providers, the cyber advisor operates at a higher level, shaping policy, influencing culture, and guiding executive decisions.
They offer expertise in threat analysis, compliance, risk management, and incident response. For example, when a new data privacy law is enacted, a cyber advisor ensures your response is timely and effective. Common misconceptions include confusing this role with day-to-day IT troubleshooting or believing a cyber advisor is only needed after a breach. For a comprehensive description of this role’s responsibilities and qualifications, see the Cybersecurity Advisor Role Overview.
Why Every Organization Needs a Cyber Advisor
The surge in data breaches, ransomware, and sophisticated attack vectors makes cybersecurity a board-level concern. A single incident can lead to significant financial loss, tarnished reputation, and business disruption. According to IBM, the average cost of a data breach exceeded $4 million globally, highlighting the high stakes involved.
Regulatory requirements such as GDPR and HIPAA add further pressure. Noncompliance can result in penalties and legal challenges. A cyber advisor brings clarity to these demands, translating complex requirements into actionable plans.
Consider a mid-sized business that faced persistent phishing attempts. With the guidance of a cyber advisor, the company implemented advanced detection tools, employee training, and a clear incident response plan. As a result, a major attack was thwarted, saving the organization from costly downtime and reputational harm. Engaging a cyber advisor is not just about protection, but about enabling confident, compliant growth.
Key Qualities to Look For
Selecting the right cyber advisor is critical. Look for the following qualities:
- Deep technical expertise and current cybersecurity certifications
- Strategic understanding of business operations and risk
- Strong communication and leadership abilities
- Demonstrated success with relevant references
- Cultural alignment and commitment to your organizational goals
A qualified cyber advisor not only secures your infrastructure but also empowers your team to anticipate and counter future threats.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Assessing Your Organization’s Cybersecurity Needs
Understanding your organization’s cybersecurity needs is the first step toward effective protection. A clear-eyed assessment helps you identify gaps, align security with business goals, and determine when to engage a cyber advisor for lasting resilience.
Conducting a Comprehensive Cyber Risk Assessment
Begin by evaluating your current security posture. This process involves mapping critical assets, such as customer data, intellectual property, and financial records. Document all data flows and understand where sensitive information is stored and transmitted.
Next, identify common vulnerabilities. These may include outdated software, weak passwords, or unsecured endpoints. Leverage established frameworks like the NIST Cybersecurity Framework to guide your assessment and ensure nothing is overlooked.
A cyber advisor helps you interpret findings, prioritize remediation, and benchmark against industry standards. This external perspective is crucial for uncovering blind spots and building a robust foundation.
Aligning Cybersecurity with Business Objectives
Cybersecurity should never exist in a vacuum. Start by understanding your organization’s strategic goals and growth plans. Are you preparing for a digital transformation, entering new markets, or adopting cloud technologies?
Map cybersecurity priorities to these objectives. For example, if customer trust is critical, focus on securing personal data and maintaining compliance. Engage stakeholders such as leadership, finance, and operations teams to ensure security investments support broader business outcomes.
A cyber advisor bridges technical and business perspectives, ensuring security initiatives drive value and support long-term growth. This alignment is vital for making informed decisions and justifying cybersecurity spend.
Engaging a Cyber Advisor: When and How
Many organizations wonder when to seek outside expertise. Warning signs include frequent security incidents, regulatory pressure, or lack of internal resources. Compare internal versus external advisory models to determine the best fit.
Ask potential advisors about their experience, approach, and references. Typical engagement involves an initial assessment, roadmap creation, and ongoing support. A skilled cyber advisor brings structure, accountability, and strategic insight to your security journey.
Timelines vary, but most organizations see measurable improvements within a few months. Clear deliverables—such as risk reports and prioritized action plans—help track progress and demonstrate value.
CTO Input: Strategic Cybersecurity Partnership
CTO Input delivers fractional executive leadership, combining deep cybersecurity expertise with business strategy. Their advisors work closely with your team to translate risk findings into actionable plans and measurable results.
With a focus on mid-sized organizations, CTO Input offers flexible, tailored engagements. Their approach bridges the gap between strategy and operational execution, delivering real impact in risk reduction and cost savings.
Ready to take the next step? Schedule a discovery call with CTO Input for personalized guidance from an experienced cyber advisor.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Building a Cybersecurity Roadmap: Step-by-Step
Creating a robust cybersecurity roadmap is essential for protecting your organization in today’s evolving threat landscape. A cyber advisor plays a pivotal role in guiding each stage of this process. By breaking down the journey into clear, actionable steps, you can ensure your business remains secure and resilient.
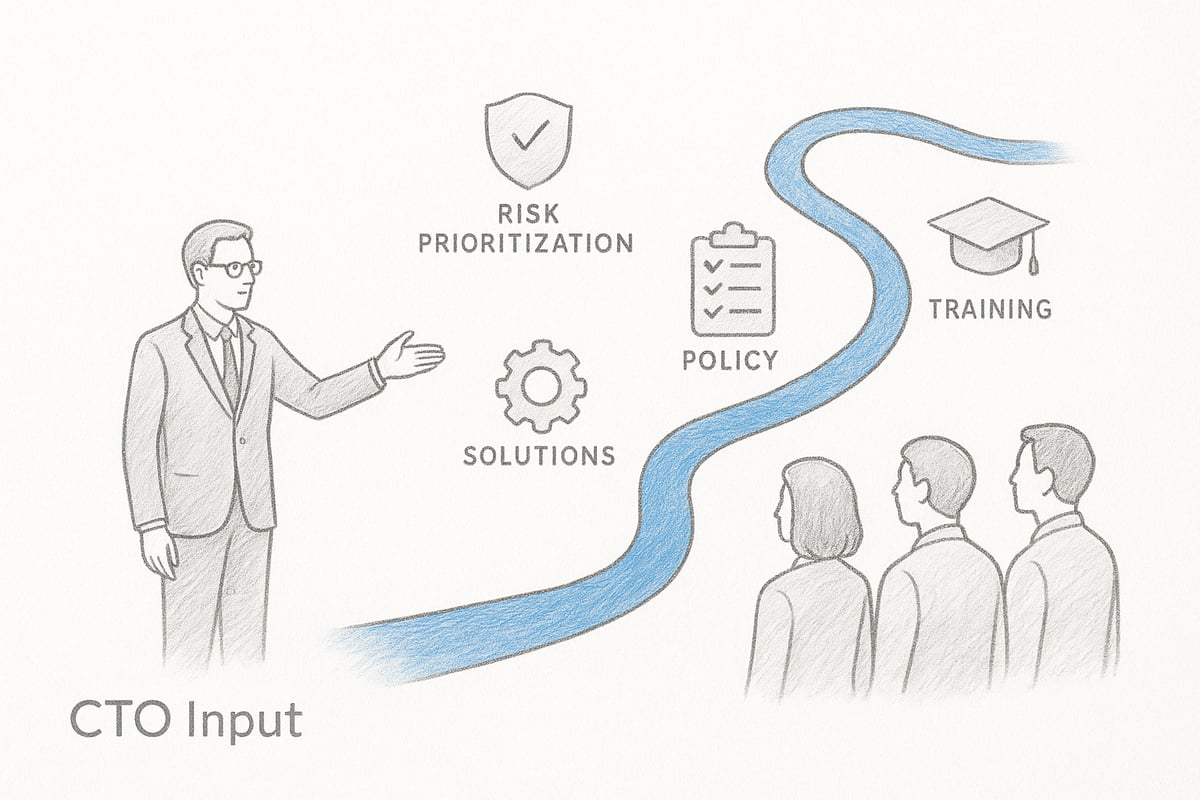
Step 1: Prioritizing Risks and Assets
Every effective cybersecurity roadmap begins with identifying what matters most. A cyber advisor collaborates with your team to pinpoint mission-critical systems, sensitive customer data, and essential business processes.
The process includes:
- Inventorying digital and physical assets
- Mapping data flows and dependencies
- Assigning risk scores based on potential business impact
For example, in retail, protecting customer payment data often takes top priority. By focusing on high-value targets, your cyber advisor ensures resources are allocated where they have the greatest effect. This targeted approach reduces exposure and strengthens your overall security posture.
Step 2: Defining Security Policies and Controls
Once risks are ranked, the next step is to establish clear, actionable security policies. Your cyber advisor helps develop and document guidelines that reflect both regulatory requirements and your unique business context.
Key elements include:
- Role-based access controls and the principle of least privilege
- Policy templates tailored to your industry
- Alignment with frameworks like ISO/IEC 27001 Standard for best practices
Effective policies clarify expectations and ensure consistent security behaviors across the organization. With a cyber advisor’s expertise, your policies remain current and enforceable as your business evolves.
Step 3: Selecting and Implementing Security Solutions
With policies in place, attention turns to choosing and deploying the right technology. A cyber advisor evaluates security tools that fit your needs, whether it’s firewalls, endpoint protection, SIEM, or EDR platforms.
Considerations include:
- Deciding between cloud-based and on-premises solutions
- Ensuring compatibility with existing infrastructure
- Applying rigorous vendor selection criteria
For a deeper dive into strategic planning, explore this Cybersecurity strategy for 2026 resource. Your cyber advisor ensures technology investments align with long-term business goals and adapt to emerging threats.
Step 4: Training and Empowering Employees
Technology is only as strong as the people using it. A cyber advisor leads the rollout of security awareness programs, helping staff recognize phishing attempts and risky behaviors.
Best practices involve:
- Running regular phishing simulations
- Promoting a culture of security mindfulness
- Measuring training effectiveness through ongoing assessments
Remember, human error is responsible for over 80% of breaches. By equipping your workforce, your cyber advisor addresses the most common vulnerability—people.
To learn more about building a resilient cybersecurity roadmap or to connect with a cyber advisor, visit https://www.ctoinput.com. For further insights, spend a few minutes exploring the CTO Input blog at https://blog.ctoinput.com.
Implementation: Turning Strategy into Action
Turning your cybersecurity strategy into reality requires disciplined execution, clear leadership, and a proactive mindset. A cyber advisor is instrumental in guiding organizations through this critical phase, ensuring that plans are not just documented but brought to life across teams.
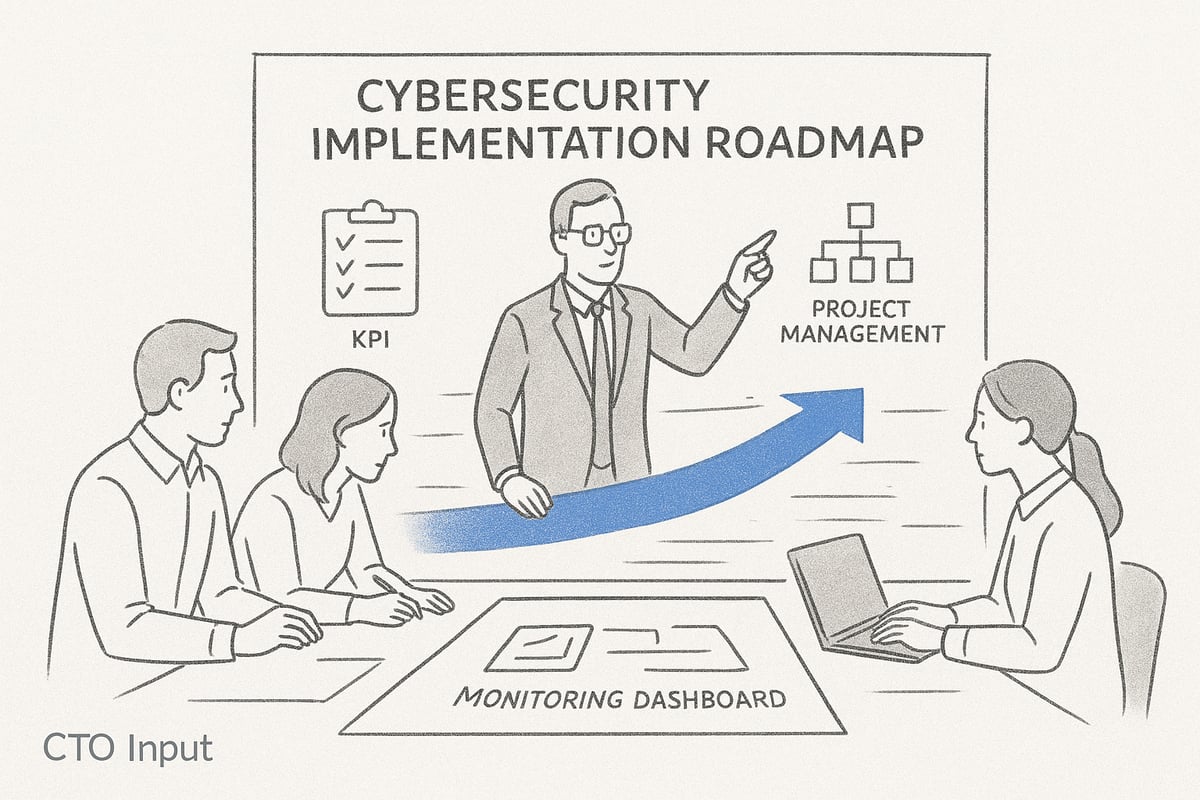
Project Management and Change Leadership
Effective implementation begins with structured project management. Assign clear roles and responsibilities across technical and non-technical teams. A cyber advisor often acts as the connective tissue, bridging gaps between IT, executive leadership, and frontline staff.
Adopt proven change management frameworks, such as ADKAR or Kotter’s 8-Step Process, to navigate resistance and foster buy-in. Strong communication is essential. Regular updates, transparent progress tracking, and celebrating quick wins all contribute to smoother transitions.
For example, when rolling out multi-factor authentication (MFA) across a distributed workforce, a cyber advisor ensures the project stays on track. They anticipate roadblocks, adjust timelines, and keep everyone aligned with the organization’s strategic objectives.
Monitoring, Detection, and Response
Once new controls and processes are in place, ongoing vigilance is key. Set up continuous monitoring with real-time alerts for unusual activity. A cyber advisor helps select and configure security tools that match your risk profile and operational needs.
Develop and rehearse an incident response plan. Conduct tabletop exercises to prepare teams for real-world events. Track key metrics such as mean time to detect (MTTD) and mean time to respond (MTTR) to measure readiness.
Real-world scenarios—like detecting and containing a phishing attack before it spreads—showcase the value of having a cyber advisor guiding your detection and response program.
Measuring Success and Adjusting Course
Implementation does not end with deployment. Establish clear key performance indicators (KPIs) for cybersecurity, such as reduction in incident rates, improved compliance scores, and faster response times.
Conduct regular audits and compliance checks to validate controls. Feedback loops, like post-incident reviews, help refine your strategy. Benchmark your program against industry standards and peer organizations.
For organizations with board-level oversight, effective communication is vital. Learn more about board reporting on cybersecurity to ensure your leadership understands progress and risk in plain language.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Future-Proofing Your Cybersecurity Strategy
Adapting to the digital landscape is not a one-time project. To truly future-proof your organization, you need a cyber advisor who can guide you through ongoing change, innovation, and risk. This section explores how to anticipate new threats, foster a culture of improvement, and build lasting partnerships for resilience.
Staying Ahead of Emerging Threats
Cyber threats are evolving rapidly. Attackers now use artificial intelligence to automate phishing, exploit supply chain vulnerabilities, and target the expanding Internet of Things. A cyber advisor tracks these trends, helping you anticipate what’s next instead of reacting after the fact.
Scenario planning is crucial. By mapping out potential attack vectors—like compromised vendors or malicious firmware—you can build layers of defense. Ongoing threat intelligence feeds provide real-time updates, allowing your team to stay alert and adapt quickly.
Regular reviews of your security posture, combined with industry frameworks, keep you aligned with best practices. With a cyber advisor guiding this process, your business is prepared for whatever the future brings.
Continuous Improvement and Innovation
Future-proofing is not just about defense, but also about continuous learning and innovation. A strong cyber advisor encourages a culture where employees learn from incidents and share insights. This approach ensures your defenses improve over time.
Automation and advanced analytics are key. Automated response systems can reduce detection and remediation times, while machine learning helps spot unusual behaviors before they escalate. For example, using anomaly detection tools, a cyber advisor can identify subtle threats that traditional monitoring might miss.
Embedding this mindset into your operations means security becomes a driver of business innovation, not a barrier. Staying current with compliance and cybersecurity essentials further supports your ability to innovate while managing regulatory risk.
Partnering with Trusted Advisors for Long-Term Success
Long-term resilience requires more than tools—it demands strategic partnerships. A dedicated cyber advisor delivers executive-level guidance, ensuring your security strategy aligns with business goals and adapts as you grow.
Collaborating with external experts brings fresh perspectives and access to specialized skills. Strategic relationships help you benchmark against industry peers, identify blind spots, and strengthen your overall posture. For organizations seeking board-level insight, the Board technology advisor role can be a game changer, bridging the gap between leadership and technical execution.
Investing in these partnerships ensures your organization can withstand threats and seize new opportunities with confidence.
To learn more and connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
You’ve seen how the right cyber advisor can transform uncertainty into a strategic advantage, guiding you step by step through risk assessment, security alignment, and future-proofing your business. If you’re ready to turn technology from a source of frustration into a foundation for growth and resilience, why not take the next step? Let’s talk about your unique challenges and opportunities, and explore how expert guidance can fast track your progress.
Schedule A Strategy Call
to start building your roadmap to confidence and security for 2026 and beyond.

