You’re running a justice organization that’s grown fast. Your mission is clear, your team is dedicated, and the stakes for the communities you serve couldn’t be higher. But behind the scenes, things feel… fragile. Case data is scattered across tools that don’t talk to each other. Grant reporting is a recurring fire drill. And the security of sensitive client information feels like a constant, low-grade hum of anxiety.
You have vendors for everything—IT support, case management software, translation services, fundraising platforms. Each one was hired to solve a problem, but together they’ve created a new one: a sprawling web of dependencies you don’t fully control. A single vendor failure, a data breach, or a sudden price hike could derail mission-critical work. You can delegate the tasks, but you can’t delegate the responsibility.
This isn’t a technology problem; it’s a leadership challenge. The good news is there’s a calm, practical path forward. This guide will walk you through a simple, believable plan for getting a handle on your vendors, reducing risk, and turning that quiet source of stress into a reliable backbone that supports your team and your mission.
Key Takeaways for Busy Leaders
- You Can’t Manage What You Don’t Map: Your first, most critical step is to create a complete inventory of every vendor. Follow the money trail in your accounting records to build a master list.
- Not All Vendors Are Equal: Classify your vendors into tiers based on how critical they are to your mission and the sensitivity of the data they handle. Focus your energy on the highest-risk (Tier 1) partners first.
- Contracts Are Your First Line of Defense: Move beyond boilerplate agreements. Insist on clear, plain-language terms for data ownership, breach notification, and service level agreements (SLAs).
- Shift from “Set-It-and-Forget-It” to Active Oversight: Establish a regular rhythm of performance reviews and proactive communication, especially with your most critical vendors.
- This Is a Journey, Not a Project: Start with small, practical wins. A focused 90-day plan can dramatically reduce risk and build the momentum needed for long-term resilience.
Your Vendors Are Your Lifeline—and Your Biggest Risk
Think about the partners you rely on every day. Your IT provider has the keys to your entire digital kingdom. The cloud service hosting your case files holds the stories of vulnerable people. The translation service handling asylum seeker interviews is privy to incredibly sensitive personal information. A single misstep by any one of them can become your crisis.
Imagine your case management software going down for two days right before a major grant deadline. Or discovering your fundraising platform had a security breach, exposing donor information. These aren’t just hypotheticals. I’ve sat with leaders in the justice sector who are grappling with these exact stressors.
The very tools that make your work possible are in the hands of third parties. This creates a hidden web of risk that, more often than not, is never fully mapped or actively managed.
The Hidden Costs of Unmanaged Vendor Relationships
Most justice-focused organizations grow on top of operational foundations that were never designed for their current scale. You add vendors one by one to solve immediate problems. But over time, this creates a sprawling, unmanaged ecosystem.
When a key vendor fails, your mission-critical work can grind to a halt. A data breach at a partner firm suddenly becomes your data breach, eroding the trust you’ve built with your community and creating a reporting nightmare for your board and funders.
This isn’t about adding bureaucracy. It’s about accepting a simple truth: your organization’s resilience is only as strong as your weakest vendor link.
From Anxiety to a Strategic Advantage
This is where a solid vendor management for justice organizations program comes in. It’s about transforming those relationships from a source of constant, low-level anxiety into a reliable backbone for your work. It’s a deliberate, structured approach to how you select, onboard, monitor, and offboard the partners who touch your systems and data.
A well-built system accomplishes a few key things:
- Protects your people and data by ensuring vendors meet clear security and privacy standards.
- Reduces operational chaos by setting clear expectations from the start.
- Provides defensible proof of diligence to your board, funders, and regulators.
- Frees up your staff from chasing vendor issues so they can focus on supporting advocates.
You can delegate the work, but you can never delegate your responsibility to protect sensitive information. A strong vendor management program is the only way to ensure your partners are treating your community’s data with the same care you do.
Think of it this way: a solid vendor management plan isn’t about creating more red tape. It’s about building a stable foundation so your team can do its most important work without the constant, quiet stress of wondering if a critical system or partner will let them down.
Mapping Your Vendor Ecosystem: From Chaos to Clarity
You can’t manage what you can’t see. For most justice organizations, the full picture of their vendor relationships is scattered across old spreadsheets, inbox archives, and the memory of a few key staff members. The first step is getting everything in one place.
This isn’t just about making a list. It’s about building an operational map—one that shows you exactly where your dependencies are, highlights hidden risks, and gives you a solid foundation for a real vendor management program.
Start With the Money Trail
The quickest way to find every vendor is to follow the money. Pull a report from your accounting system of every payment made to an outside company over the last 12 to 18 months. This gives you a raw, unfiltered list of everyone you do business with. You’ll see the obvious ones, but you’ll also uncover forgotten relationships, like the one-off contractor who still has access to your cloud drive.
Once you have this list, sit down with your program managers and your de-facto “tech person.” For each vendor, ask simple questions:
- What exactly do they do for us?
- What systems or data do they touch?
- Who is our day-to-day contact?
This simple exercise transforms a boring payment ledger into a living inventory of your operational partners.
Not All Vendors Are Created Equal
With a complete list, the real work begins. The biggest mistake organizations make is treating all vendors the same. The company that services your office printer is not in the same risk category as the vendor that hosts your client database. This is where classification becomes essential.
You need to evaluate each vendor on two key factors: their criticality to your mission and the sensitivity of the data they handle.
Think about a translation service. On the surface, it might seem like a low-risk vendor. But if you’re a refugee support organization using that service for asylum-seeker interviews, that vendor is handling incredibly sensitive personal stories and personally identifiable information (PII). They are a Tier 1 strategic vendor, and you have to manage them that way.
The question isn’t “How much do we pay them?” It’s “What would break if they failed?” This shift in perspective is the key to seeing your vendor ecosystem clearly and managing risk effectively.
Visualizing the “why” behind this effort can help get your team on board.
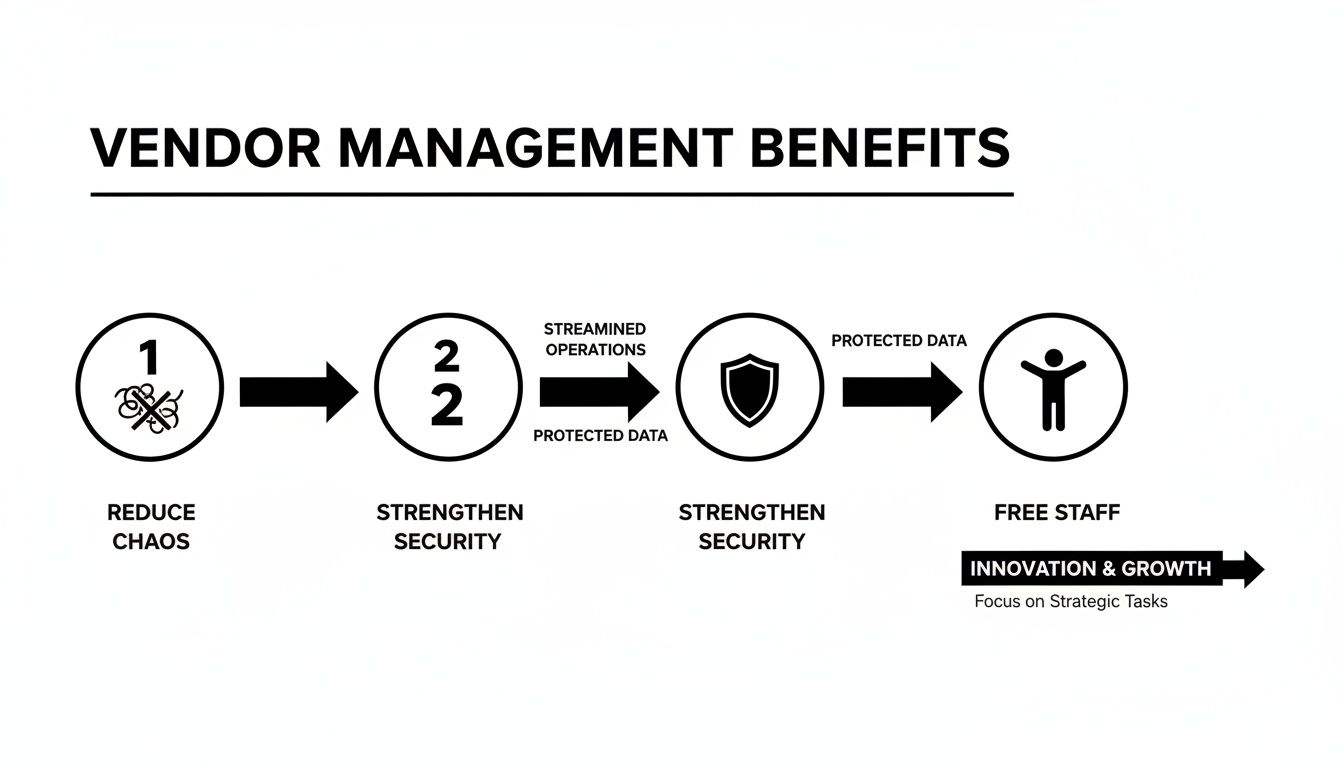
Moving from tangled dependencies to clear oversight isn’t just a bureaucratic exercise. It directly strengthens your security and frees up your team’s capacity to focus on the mission.
A Simple Framework for Vendor Tiers
To make this practical, here’s a simple framework you can use to classify vendors. This helps you prioritize where to focus your limited time and energy.
Vendor Risk Classification Matrix
| Tier | Operational Criticality | Data Sensitivity | Management Focus |
|---|---|---|---|
| Tier 1 | Mission-Critical: Operations would halt or be severely impacted without them. | High: Handles PII, client case files, financial data, or other restricted information. | Intensive: Full risk assessments, strict contract terms, continuous monitoring. |
| Tier 2 | Important: Disruption would cause significant inconvenience but not stop core work. | Medium: Handles internal operational data, employee information, or public-facing content. | Moderate: Standardized due diligence, regular check-ins, contract review. |
| Tier 3 | Low: Non-essential services or easily replaceable providers. | Low: No access to sensitive data; handles only public information or physical assets. | Light: Basic procurement process, verification of business legitimacy. |
Using a simple tiering system like this makes it immediately obvious where you need to spend your time.
Turning Your Inventory into an Actionable Map
Once you’ve classified your vendors, you have more than just a list—you have an actionable map. This map allows you to:
- Prioritize your efforts: Focus on the Tier 1 vendors who pose the greatest risk.
- Identify concentration risk: Are you relying too heavily on one single provider for multiple critical functions?
- Spot security gaps: Which vendors are handling sensitive data but have never gone through a proper security review?
- Communicate with clarity: Walk into a board meeting with a clear, data-informed picture of your organization’s third-party risk.
This initial mapping process turns that vague anxiety about “vendor risk” into a concrete, manageable plan. You’re moving from a reactive stance—only thinking about a vendor when something breaks—to a proactive one.
Building Your Vendor Risk Assessment Framework
You’ve mapped your vendors. That’s a huge first step. But knowing who they are is different from knowing what risk they bring to your organization. Now, we build a simple framework to assess that risk. This isn’t about creating monstrous spreadsheets; it’s about asking the right questions, methodically.
A solid assessment boils down to three areas: their security posture, their approach to privacy, and their operational resilience. Can they show you a SOC 2 report? How do they handle sensitive data? What’s their plan if their service goes down? A major outage on their end directly impacts your ability to serve your community.
I once worked with a legal aid clinic using a popular cloud service for case files. A quick look at the vendor’s terms revealed weak data residency clauses. This meant sensitive client information could have ended up stored in a country with poor privacy laws. A simple assessment caught that, preventing a potential crisis.
Developing a Simple Scoring System
To make smart decisions, you need objective data. A simple scoring system gives each vendor a risk score, which helps you prioritize where to focus your attention. You can build a straightforward system that scores vendors on a 1-5 scale across a few critical factors:
- Security Certifications: Do they have a SOC 2 Type II or something comparable? A vendor with audited controls is a much safer bet.
- Data Handling Policies: Are their terms of service crystal clear about data ownership, retention, and deletion? Vague language is a red flag.
- Incident Response Plan: How will they notify you if there’s a breach? A slow or unclear process is a dealbreaker.
- Operational Resilience: What are their uptime guarantees (Service Level Agreements)? A vendor promising 99.99% uptime is far less risky than one offering no guarantee.
This exercise gives you a tangible risk score for every Tier 1 and Tier 2 vendor. Suddenly, that vague sense of unease turns into a clear, prioritized list of risks you can actually manage.
Why This Is No Longer Optional
The regulatory world is catching up. Mandates like the DOJ’s Data Security Program require vendor screening for restricted data. This has shifted risk assessment from a “nice-to-have” best practice to a compliance must-do. The days of a vendor saying “trust us, we’re secure” are over. That answer won’t fly with your board, your funders, or regulators.
A formal risk assessment framework isn’t about being cynical; it’s about being responsible. It’s the proof that you are exercising due diligence to protect the sensitive information entrusted to you by vulnerable communities.
Recent trends hammer this point home. Vendor management is a top priority for U.S. regulators, as nearly half of all organizations reported a third-party data breach last year. This has pushed the focus toward continuous monitoring instead of one-time checks. The DOJ’s Data Security Program is forcing organizations to adopt risk-based procedures for how data flows to partners.
Putting the Framework into Action
With risk scores in hand, you’re ready to make informed decisions. A high-risk score doesn’t automatically mean you fire a vendor. It means you need to have a serious conversation and put a plan in place to lower that risk. This might look like:
- Asking for stronger data protection language in your contract.
- Requiring them to complete a standardized security questionnaire.
- Requesting a copy of their latest penetration test results or SOC 2 report.
This structured approach gives you both leverage and clarity. Instead of making a vague request for “better security,” you can point to specific issues your assessment uncovered. You can adapt our cybersecurity risk assessment template to fit your vendor management process. It’s a calm, methodical way to reduce your risk and build more resilient partnerships.
Strengthening Your Contracts and Onboarding Process
Your vendor contracts are your first and best line of defense. Too often, agreements are based on generic templates that do little to protect a justice organization or the sensitive data it handles. It’s time to move beyond that boilerplate language.
This isn’t about adding confusing legal jargon. It’s about insisting on plain-language terms that clearly define expectations, spell out responsibilities, and give you real options when things go wrong.
From Handshake Agreements to Ironclad Terms
The most effective contracts are built on a foundation of clarity. Start by focusing on a few essential clauses that directly address the biggest risks. When you do this, procurement stops being a transaction and becomes a core part of your risk management strategy.
Here are the key clauses to insist on:
- Service Level Agreements (SLAs): These are non-negotiable. An SLA defines performance in concrete terms. Instead of a vague promise of “good service,” it specifies uptime guarantees (like 99.9%), response times for support tickets, and what happens—usually service credits—if the vendor falls short.
- Clear Data Ownership: The contract must state, unequivocally, that you own your data. Full stop. It should also grant you the right to retrieve all of it in a standard format at any time.
- Breach Notification Requirements: Define exactly how and when a vendor must notify you of a security incident. Specify a tight timeline, like within 24 hours of discovery, and detail the information required in that initial report.
- Right-to-Audit Clauses: This is your “trust but verify” clause. It gives you the right to review a vendor’s security practices, either by conducting your own review or requesting their third-party audit reports, like a SOC 2.
A strong contract is your playbook for the relationship. It sets the rules of engagement before there’s a problem, ensuring both you and your vendor are aligned on what success and security look like.
Building a Bulletproof Onboarding Process
A solid contract is only half the battle. How you bring a new vendor into your ecosystem is just as important. A rushed or informal onboarding process creates security gaps and misaligned expectations that can fester for years.
Create a structured onboarding checklist that must be completed before a vendor gets access to any of your systems or data. This isn’t about creating bureaucracy; it’s about being deliberate.
Your checklist should confirm:
- Security Review is Complete: Have you reviewed their SOC 2 report? Did they complete your security questionnaire?
- Access Controls are Defined: Who from the vendor team needs access? What level, to what systems, and for how long? Enforce the principle of least privilege from day one.
- Key Contacts are Established: Who is your day-to-day contact? And who is the after-hours escalation point for a security incident?
- Data Handling Protocols are Understood: Does the vendor team understand your data classification rules, especially for sensitive client information?
This process ensures that security is baked in from day one and sets the tone for a responsible relationship. For a deeper dive, explore our guide on crafting justice data sharing agreements.
Vigilant contract monitoring goes beyond security. A client of mine discovered that their outside law firms were trying to hike rates by over 20% in a single year. By putting regular performance surveys in place, they not only controlled costs but also saw service delivery improve. You can find out more about this balanced approach to vendor management.
Moving From “Set-It-And-Forget-It” to Continuous Oversight
Signing the contract isn’t the finish line; it’s the starting gun. Many organizations treat vendor management as a one-time event, but that’s a huge risk. Real oversight is a discipline. Shifting from a “set-it-and-forget-it” attitude to one of continuous monitoring is what separates a resilient organization from one that’s just crossing its fingers.
This doesn’t mean you need a giant vendor management office. It’s about finding a sustainable rhythm of check-ins and performance reviews that keeps everyone accountable. The goal is a true partnership where your vendors feel invested in your mission.
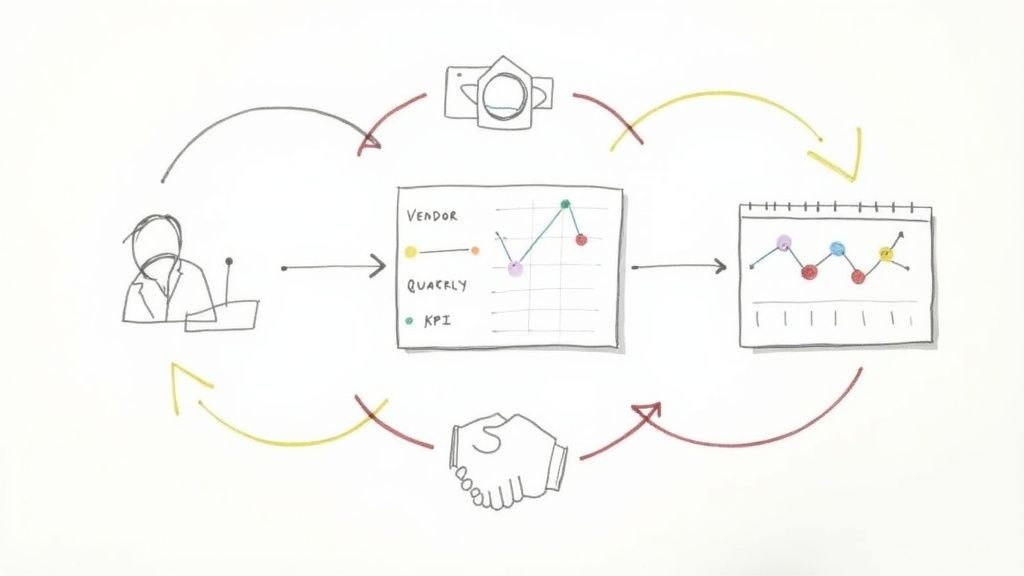
Establish a Rhythm of Review
Match your monitoring cadence to the vendor’s risk profile. Your Tier 1 vendors—the ones handling sensitive case data or running your core systems—need more attention. A practical approach looks like this:
- Tier 1 Vendors: Formal performance reviews quarterly.
- Tier 2 Vendors: A scheduled check-in every six months.
- Tier 3 Vendors: An annual contract review before renewal.
These reviews aren’t confrontational. They are structured conversations focused on the Key Performance Indicators (KPIs) in your contract. Did they meet the 99.9% uptime guarantee? This data-driven approach removes emotion and grounds the conversation in reality.
Foster Proactive Communication
The point of continuous oversight is to catch small issues before they snowball. The U.S. Department of Justice provides a good model for this with its Scorecard program, which evaluates vendor performance against clear goals. When you share performance data and maintain open lines of communication, you signal a commitment to a real partnership.
A healthy vendor relationship isn’t defined by a lack of problems. It’s defined by how you solve them together. Regular communication builds the trust needed to navigate tough situations with honesty and speed.
Plan for When Things Go Wrong
Even the best vendors have bad days. A service will go down. A security vulnerability will be discovered. Your ability to respond effectively depends on having a plan before you need it.
Your incident response plan must explicitly loop in your critical vendors. This means defining communication channels and escalation paths in advance. When your cloud provider reports a potential breach, you need to know exactly who to call and what your team’s first five steps are, without hesitation.
Your plan needs to answer:
- Who is our designated point of contact at the vendor for security incidents?
- What’s the agreed-upon timeframe for them to notify us (e.g., within 24 hours)?
- What information must their initial report contain?
- How will we coordinate communications to stakeholders?
Having these answers documented turns a potential crisis into a structured process. An IT security assessment checklist can help you cover all the bases. This is what proactive vendor management looks like.
Your 90-Day Quick Wins Action Plan
Getting started can feel overwhelming, but you can make a significant impact in just 90 days. Focus on high-value activities that immediately reduce risk and build momentum.
| Timeline | Action Item | Key Outcome |
|---|---|---|
| Days 1-30 | Create a complete inventory of all current vendors. | A single source of truth for all vendor relationships, identifying who has access to what data. |
| Days 1-30 | Identify your top 5-10 most critical (Tier 1) vendors. | Prioritized focus on the vendors that pose the highest risk to your operations and data. |
| Days 31-60 | Review contracts for your Tier 1 vendors. | Clear understanding of existing SLAs, data protection terms, and renewal dates. |
| Days 31-60 | Schedule introductory “partnership” meetings with Tier 1 vendor contacts. | Establishes a proactive communication rhythm and reinforces shared accountability. |
| Days 61-90 | Draft a basic incident response communication plan for a top vendor. | A documented process for a high-risk scenario, reducing confusion during a real event. |
| Days 61-90 | Present your initial vendor risk overview to leadership. | Secures buy-in and demonstrates immediate progress and control over third-party risk. |
By tackling these focused tasks, you build the foundational habits of a mature vendor management program that can protect your organization for years to come.
Common Questions About Vendor Management
Leaders in justice organizations often wonder how to get a real vendor management program off the ground, especially when time and money are stretched thin. These are the right questions to be asking.
“Where Do We Even Start with a Small Team and a Tight Budget?”
This is the question I hear most often. The answer is simpler than you think: start small and aim for immediate impact. You don’t need expensive software or a dedicated vendor manager from day one.
The most practical, low-cost first step is to build your vendor inventory. Pull your accounts payable records for the last 12 months. This costs nothing but a few hours of time and instantly gives you a full picture of who you’re doing business with.
Once you have that list, pick your top five most critical vendors. For the next 90 days, they are your entire focus. Just review those five contracts and schedule a proactive check-in. This focused approach builds momentum without burning out your team.
“How Do We Handle Pushback from Long-Time Vendors?”
It’s natural to get some resistance when you introduce new requirements, especially from vendors you’ve worked with for years. A partner accustomed to a casual relationship might balk at a formal security questionnaire.
The key is to frame the conversation around partnership and shared responsibility, not mistrust. Explain that these updated standards aren’t about them, but about your evolving obligations to funders, regulators, and the communities you serve. You’re not pointing fingers; you’re shoring up your shared defenses.
A great way to open that conversation is with something like, “As our work and the risks we all face have evolved, we’re formalizing our processes with key partners to better protect the sensitive data we handle together. We see you as a critical part of that effort.”
This approach preserves goodwill while making it clear that these new standards are non-negotiable. If a vendor is unwilling to meet reasonable security requirements, that’s a major red flag—and a sign they may no longer be the right partner.
“What’s the Single Most Important Thing to Track?”
While uptime and service level agreements (SLAs) are important, the single most telling metric is a vendor’s incident response time and transparency. This cuts through the contractual jargon and gets to the heart of their reliability and integrity.
When something goes wrong—and it will—what you really need to know is:
- How quickly does the vendor notify you of a security incident or service outage?
- How clear and actionable is their communication while the issue is ongoing?
A vendor who meets their 99.9% uptime SLA but takes 72 hours to admit to a minor data breach is a far greater risk than one who proactively reports a major outage within an hour.
Tracking this requires having clear breach notification timelines in your contracts and a simple internal process for logging every incident. A vendor’s commitment to transparent communication during a crisis is the ultimate test of the partnership.
Building a mature vendor management for justice organizations program is a journey, not a sprint. It’s about taking calm, deliberate steps to reduce risk and build a more resilient foundation for your mission. If you feel stuck or just need an experienced guide to help you build a clear, defensible roadmap, CTO Input is here to help.

