You feel the pressure from customers, lenders, and your board. Security questionnaires keep getting longer, regulators are more demanding, and every new breach in the news makes you wonder, “Are we next?”
But a full-time CISO is a six-figure hire you cannot justify yet. That is where a fractional CISO fits: an experienced security leader who joins part time, sits at your leadership table, and builds a real security program without blowing up your budget.
This article walks through How Fractional CISOs Build Security Programs from Zero in 6 Months in clear business terms. You will see what happens month by month, what changes on the surface for you and your team, and what outcomes you should expect at the six-month mark.
What A Fractional CISO Really Does For A Mid-Market Company

Close-up of Scrabble tiles spelling “SECURITY”, a simple reminder that security is built one clear step at a time.
Photo by Markus Winkler
A fractional CISO is not “just another IT vendor.” Think of this role as your part-time security executive, similar to a fractional CFO for finance.
Their job is to:
- Turn vague cyber fear into a clear risk picture.
- Decide what must be protected first and why.
- Lead a focused plan that your teams can actually execute.
In business terms, the outcomes look like this: lower risk, fewer surprises in board meetings, better answers to customer security questions, and less chaos for your IT and engineering teams.
Instead of buying more tools, your fractional CISO sets priorities. They review contracts, data flows, and incident history, then pick a simple framework in the background, like NIST or SOC 2, to organize the work. For a deeper look at how seasoned leaders structure the role, this fractional Chief Information Security Officer playbook offers a helpful overview.
This is the foundation for How Fractional CISOs Build Security Programs from Zero in 6 Months, even in mid-market companies with messy legacy systems and fast growth.
Why growing companies feel stuck on cybersecurity
Most CEOs in the 2 to 250 million range share the same complaints.
- Customer and partner questionnaires that no one can answer with confidence.
- Vendors pushing tools that all claim to “solve security.”
- A board that keeps asking, “Are we covered if something bad happens?”
- A quiet fear that one public breach could undo years of brand building.
You might lean on your IT director or head of engineering to handle all of this. They are already juggling downtime, projects, vendors, and user issues. They are not paid or staffed to be your security executive.
The result is a pattern: scattered tools, partial policies, and no single person who owns the overall security story.
How a fractional CISO fills the leadership gap without a full-time hire
A good fractional CISO steps into that gap as a senior leader, not a ticket-taker.
They work part time, often one to three days a week, but operate as your C-level owner for security. They join leadership meetings, talk with sales about customer needs, align with finance on budgets, and coach IT and engineering instead of overruling them.
Their focus is simple:
- Protect revenue and contracts.
- Support compliance goals.
- Guard brand and trust with practical controls, not theory.
Instead of reacting to every new tool pitch or scary headline, you get one plan, one voice, and clear choices.
How Fractional CISOs Build Security Programs From Zero In 6 Months
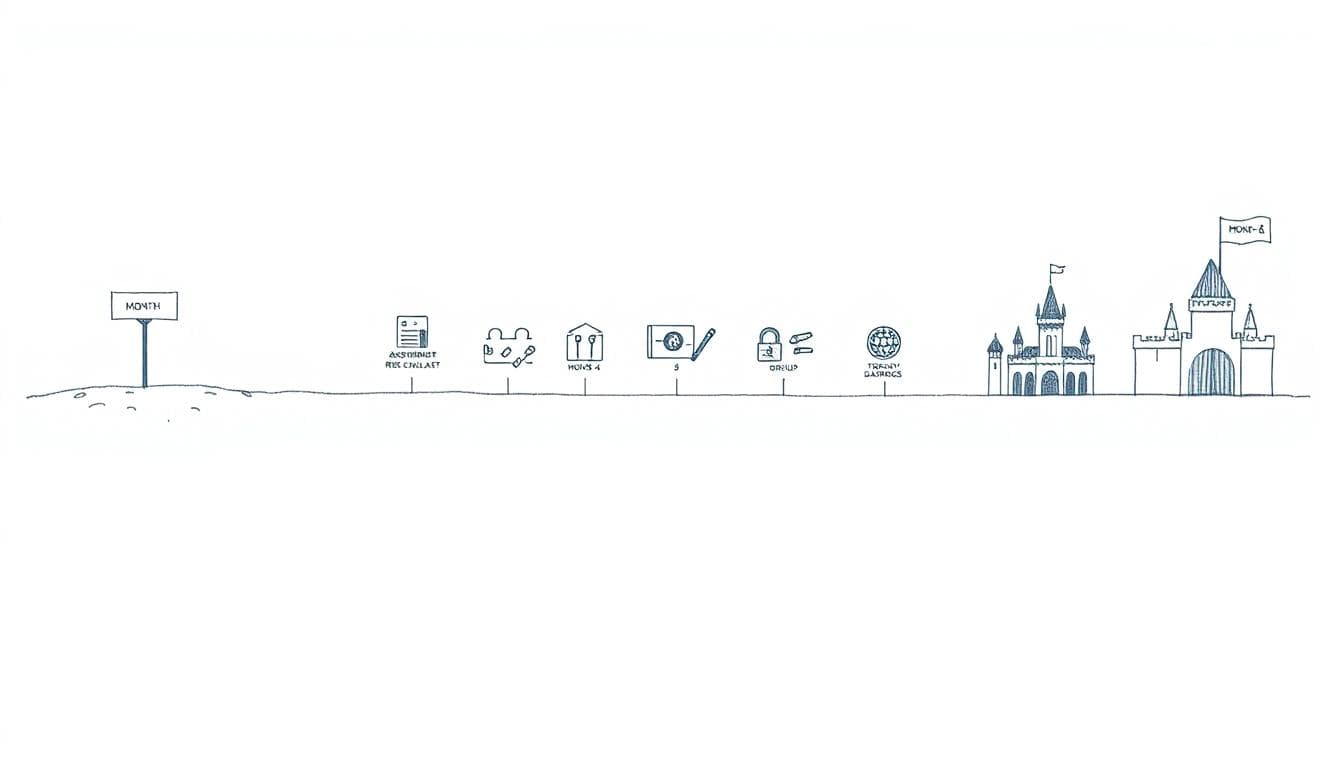
Illustration of a 6‑month journey from “Month 0” chaos to a structured, secure program, with assessment, fixes, and reporting phases along the road. Image created with AI.
In 2025, analysts expect around 40% of small and mid-market companies to use a fractional CISO. The reason is simple: they compress years of security work into a focused six-month sprint that leadership can understand.
Here is what that sprint usually looks like.
Months 1 to 2: Get the truth on your cyber risk and set the rules
The first 60 days are about truth and clarity.
Your fractional CISO spends time with:
- You and your leadership team, to understand strategy and risk tolerance.
- IT and engineering, to see what is actually in place.
- Sales, customer success, and legal, to review contracts and promises.
Behind the scenes, they map you loosely against standards like NIST CSF or SOC 2. They might use checklists and tools, but the outputs you see are very human:
- A plain-language risk picture. For example, “Ransomware could stop shipping for 5 days” or “We could lose our largest healthcare customer without HIPAA proof by Q3.”
- A short, ranked list of “must-fix” items. Not 300 tasks, but 10 to 20 moves that matter most in the next 90 days.
- A starter set of policies that people can follow. Things like how staff handle sensitive data, how access to systems is granted and removed, and who does what during an incident.
These are not 80-page binders. They are simple rules and diagrams that match how your company actually works.
Many CEOs also start looking at SOC 2 during this phase. If you are heading that way, resources like OneTrust’s 9-point framework for evaluating SOC 2 software can help your fractional CISO and IT team pick the right tools without overbuying.
Months 3 to 4: Fix the biggest gaps with smart, business-friendly controls
Once the picture is clear, the work shifts from “What is wrong?” to “What are we fixing first?”
Your fractional CISO leads a focused set of changes, often including:
- Multi-factor authentication (MFA) for staff and admins, so a stolen password alone cannot unlock key systems.
- Tighter admin access, so only a small group can make major changes and every admin account is tied to a real person.
- Better backups, stored offsite or in a separate account, so ransomware does not wipe out your ability to operate.
- Vendor and partner access cleanup, so former partners and old test users do not still have open doors into your data.
Each move has a clear business story: less chance of a shutdown, faster recovery if something breaks, easier answers during audits.
The fractional CISO does not replace your IT or engineering team. They sit beside them, help pick realistic tools, clear roadblocks, and push decisions when tradeoffs appear between cost, speed, and risk.
At this point, you start to feel the program take shape. New hires follow a consistent access process. Old accounts are removed. Your team knows who approves exceptions and why.
Months 5 to 6: Train your people, test your response, and start reporting like a pro
With the biggest technical gaps under control, the focus shifts to people and routine.
Your fractional CISO usually drives four key habits in months 5 and 6:
- Company-wide security awareness training
Short sessions that explain phishing, passwords, and safe behavior in plain language. The goal is to turn every staff member into a basic sensor, not a weak link. - Phishing simulations
Simple test emails that show who clicks and who reports. The point is not to shame people, but to measure risk and improve training. - An incident response plan that is written and tested
A clear script: who declares an incident, who talks to customers, who makes technical calls, and how decisions are logged. Often this includes a short “tabletop exercise” where leaders walk through a fake breach. - Board-ready dashboards or scorecards
A one-page view that shows top risks, recent incidents, progress on projects, and compliance status. By now, you should be able to explain cyber risk as clearly as financial risk.
At the end of six months, you do not just own new tools. You have a living security program with:
- Named owners.
- Regular reviews.
- A roadmap for the next 12 to 24 months that fits your growth plan.
What CEOs Should Expect After 6 Months With A Fractional CISO
Six months go by fast. So how do you know if the engagement worked?
You should see fewer nasty surprises and more direct answers. Security questions in board or lender meetings become shorter, because you have evidence ready. Customer deals that once stalled on security review begin to move faster.
Most mid-market CEOs also notice a shift inside the company:
- IT and engineering teams feel backed, not blamed.
- Policies exist, and people actually follow them.
- Budget talks about security become linked to clear risk reduction.
You move from “I hope we are fine” to “I know where our biggest risks sit, what we have done, and what we are choosing not to do yet.”
Clearer board answers, fewer cyber surprises, and real compliance progress
By the six-month point, a good fractional CISO engagement should give you:
- A list of key risks, along with how each one has been reduced or accepted.
- Core policies that auditors, customers, and regulators expect to see.
- Evidence packs ready for common reviews, like SOC 2 prep, vendor security questionnaires, or bank diligence.
- Faster and cleaner handling of real incidents, even if they are minor.
For example, vendor questionnaires that once took weeks now take days, because the answers are organized. Lender reviews move faster, because you can explain security posture in simple terms. Minor phishing incidents are handled in hours, not days.
A simple, believable roadmap for the next 12 to 24 months
The final product of the first six months is not just a report. It is a forward-looking roadmap tied to your strategy.
That roadmap should tell you:
- What to invest in next, and why it matters to revenue and trust.
- What can wait, with a clear statement of the risk you are accepting.
- How much ongoing fractional CISO time you need, if any, to keep the program moving.
Instead of reacting to every new threat article or vendor pitch, you and your team follow a plan. Security becomes part of how you run the business, not a side project that flares up during crises.
Conclusion
Fractional CISOs build security programs from zero in 6 months by doing three things in order: finding the real risks, fixing the biggest gaps, and then building habits through training, testing, and clear reporting. You get senior security leadership without a full-time hire and a program that matches your size, customers, and ambition.
If you want this level of clarity and control for your own company, learn how CTO Input approaches fractional CISO, CIO, and CTO leadership at https://www.ctoinput.com. Keep exploring practical, executive-ready guides on the CTO Input blog at https://blog.ctoinput.com.

