Protecting your clients’ data isn’t just a best practice; it’s a core part of your mission. For court self-help organizations, a solid data security strategy for court self help organizations is the bedrock of public trust. It’s about moving away from last-minute fixes and building a thoughtful, proactive system to guard the sensitive information you handle every day.
The panic is a familiar one. You’re scrambling to pull a funder report, trying to make sense of three different spreadsheets that don’t quite match up. A key staff member just left, and you’re realizing they were the only one who truly understood the quirks of your intake system. Every time a news story about a data breach pops up, you feel a pit in your stomach, wondering, “Could we be next?”
If you’re leading a court self-help organization, technology can feel more like a quiet source of stress than a capacity multiplier. This guide is a practical field memo from a calm, seasoned advisor. It starts with your mission, listens to how work really happens, and then helps you build a simple, believable modernization path for technology and data that you can defend to your board, funders, and community.
Key Takeaways
- Start with Quick Wins: Before building a long-term roadmap, focus on immediate, low-cost actions in the first 90 days, like enforcing Multi-Factor Authentication (MFA) and adopting a password manager, to tangibly reduce risk.
- Map Reality, Not Theory: Honestly trace how client data actually moves through your organization—including workarounds and spreadsheets—to identify your true risk points, or “chokepoints.”
- Build a Simple Playbook: Create a practical governance guide based on four pillars: access control (least privilege), vendor vetting, continuous training, and a simple one-page incident response plan.
- Plan for Long-Term Resilience: Move from reactive fixes to a proactive stance by standardizing your technology, budgeting for security as an operational cost, and weaving privacy principles into every new project from the start.

The stakes couldn’t be higher. Organizations holding sensitive personal data are prime targets. A single breach of confidential case files or immigration documents could have devastating consequences for your clients, exposing them to identity theft, domestic violence risks, or legal enforcement actions.
This guide will walk you through a disciplined process to:
- Pinpoint immediate, practical changes that reduce chaos and risk.
- Anchor your strategy in your mission and map how your team actually works.
- Create a one-to-three-year roadmap that turns your systems from a source of stress into a backbone that reliably supports advocates.
Building this confidence starts with understanding the fundamentals of comprehensive security measures. This guide provides the framework to get you on that path, turning data security from a source of anxiety into a pillar of strength for your organization.
Your First 90 Days: Quick Wins to Reduce Immediate Risk
Building a long-term data security strategy is the goal, but you can’t architect a new house while the old one is on fire. Before planning a multi-year roadmap, you must tackle the most immediate threats. The next 90 days are about stopping the bleeding with high-impact, low-cost actions that tangibly reduce your organization’s risk.
This isn’t the time for new platforms or complex projects. It’s about tightening the screws on the tools and workflows you already have. The most common chokepoints are client intake forms, referral handoffs between partners, and the scattered, disorganized storage of sensitive documents. Let’s start there.

Lock Down Your Digital Front Doors
Your core systems—email, case management, cloud storage—are the most frequent targets for attack. Securing them delivers the biggest and fastest return on your effort.
Here are three non-negotiable actions to take right now:
- Enforce Multi-Factor Authentication (MFA) Everywhere: If you only do one thing from this list, do this. Turn on MFA for all staff on your email platform (like Microsoft 365 or Google Workspace), your case management system, and any cloud storage like Dropbox. This single step makes it exponentially harder for an attacker to get in, even if they steal a password.
- Standardize a Password Manager: A sticky note with “IntakeForm2024!” is not a password strategy. It’s a liability. Adopt a simple, respected password manager (like 1Password or Bitwarden) for the entire team. This enforces strong password creation and gives staff a secure way to share login credentials without resorting to insecure spreadsheets or emails.
- Create a One-Page Incident Contact Sheet: When a laptop is stolen or a staff member clicks a phishing link, panic sets in. Who do you call first? Create a simple, printed document that lists the critical contacts: your IT support, key leadership, and your cyber insurance provider. This ensures a calm, orderly response instead of a chaotic scramble.
Shrink Your Attack Surface
A core principle of a modern data security strategy for court self help organizations is data minimization. Simply put, the less sensitive data you hold, the less there is to protect—and the lower your risk if a breach happens.
What we stop doing: Collecting data “just in case.” Take a hard look at your intake forms, both paper and digital. Are you asking for a client’s full Social Security Number when only the last four digits will do? Do you really need a detailed immigration history for a simple housing issue? Every piece of data you collect becomes a liability you are responsible for protecting.
This process isn’t just a security exercise; it’s an operational one. Challenge your team to justify every single field on every form. Eliminating unnecessary data collection immediately reduces your risk profile and makes compliance easier. This is a powerful win you can report to your board and funders, demonstrating proactive stewardship of client information. A formal review can give you a structured way to find these opportunities. To get a better sense of what that involves, take a look at our IT security assessment checklist.
These early wins build crucial momentum. They deliver measurable security improvements without a major budget request, showing stakeholders you’re serious about protecting your mission and the communities you serve. This creates the trust and confidence needed to tackle the deeper, systemic work ahead.
Mapping How Your Data Actually Moves
Before you can build a solid security strategy, you have to get brutally honest about how your organization really operates. Not the official process in a dusty policy manual, but how work actually gets done. You need to follow the data.
Your first job is to trace the complete journey of your client’s information, from the moment someone fills out a web form to the anonymized number you put in a funder report. This process, data mapping, is the bedrock of any real-world data security strategy for court self help organizations.
The point here isn’t to create a perfect diagram. It’s to find the truth. We need to uncover every shared spreadsheet, every emailed attachment, and every clever workaround your staff has invented to make their jobs easier. It’s in these unofficial “shadow IT” systems where your biggest risks are quietly hiding.
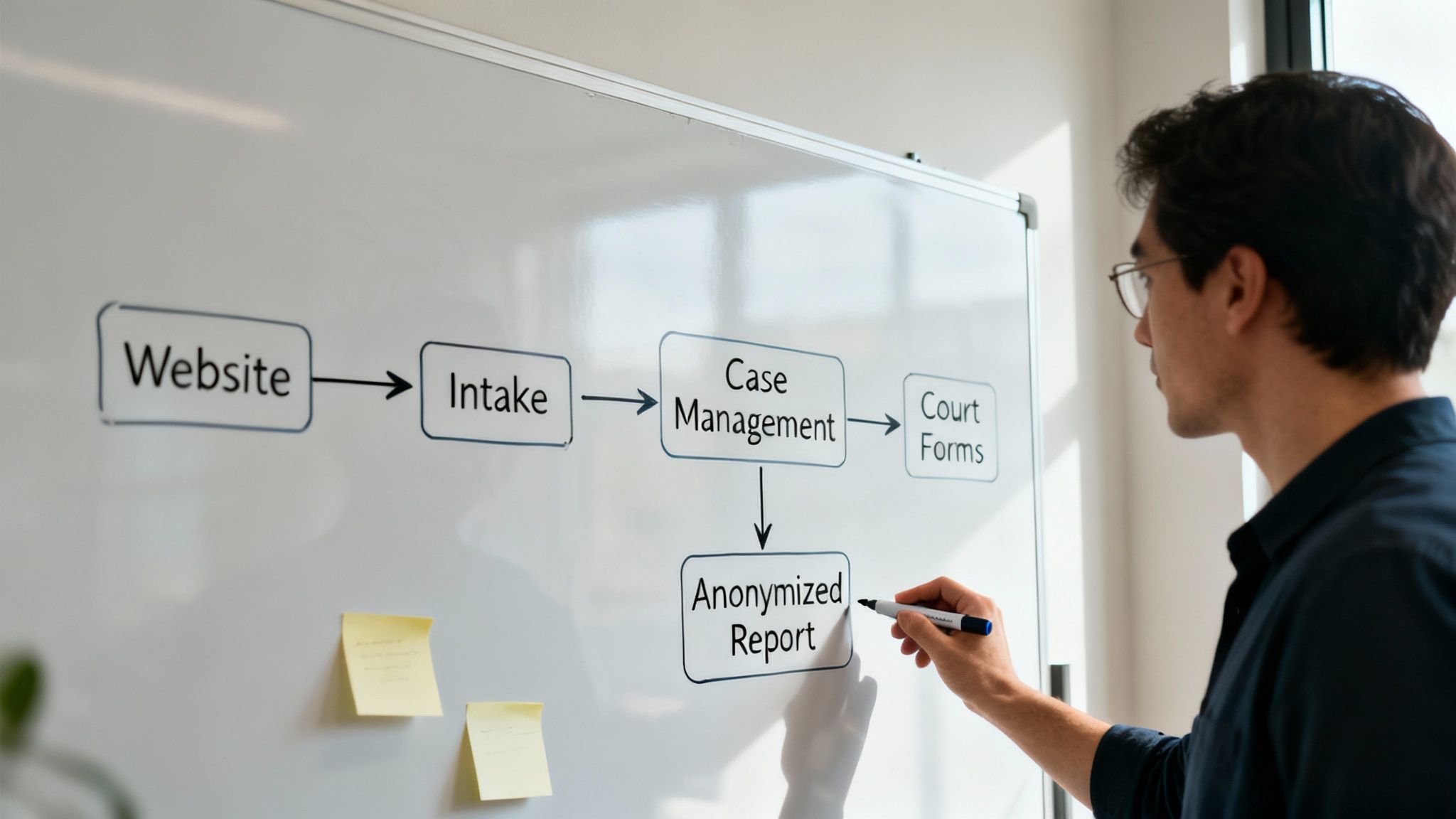
Tracing the Client Information Lifecycle
Get the right people in a room—an intake specialist, a paralegal, your operations manager—and grab a whiteboard. Your mission is to map the lifecycle of a typical client case. Forget about specific software and focus purely on the actions people take.
From my experience, the journey often looks something like this:
- Initial Contact: Someone finds you online and fills out a contact form. Where does that submission land? A shared Outlook inbox? A Google Sheet someone set up years ago?
- Intake & Eligibility: A staff member calls them back to screen for eligibility. Are they scribbling sensitive details on a legal pad to type up later, or entering it directly into a secure system?
- Case Management: The case is opened. Your team starts generating court forms and saving client documents. Where do those files live? On a central, backed-up server, or scattered across individual staff desktops and personal Dropbox accounts?
- Referrals & Handoffs: The client needs a service you don’t offer, so you refer them to a partner agency. How is that information shared? An unencrypted email with attachments? A phone call where details could be misheard?
- Reporting & Archiving: The case is closed. The data now becomes part of a report for your grantors. Who is responsible for pulling those numbers, and how do they ensure all personally identifiable information is stripped out first?
This exercise is incredibly revealing. It will show you the exact spots where your intended process breaks down and reality takes over. These are your critical chokepoints.
Identifying Your True Risk Surface
As you sketch out these workflows, your organization’s true risk surface comes into focus. It’s not just your main case management software. It’s the entire ecosystem of tools and human behaviors that touch sensitive data. This process often uncovers uncomfortable but completely fixable truths.
The reality for most justice organizations is a patchwork of systems held together by good intentions. Court-based self-help centers, in particular, are often flying blind. A national survey revealed that only 20% of these centers had a formal plan for continuing operations in a crisis, and many lacked clear data policies to protect the very people they’re designed to help. Considering the incredibly sensitive information they handle, this is a massive gap. You can explore the full national landscape of self-help center operations in the report.
By grounding your strategy in how your team actually works, you avoid creating a bunch of rules that nobody will follow. This map you’ve just built is the foundation for everything else you’re about to do.
This mapping exercise isn’t just a one-off task; it’s a vital input for a more structured review. In fact, this workflow analysis is a key component we discuss in our guide to running a privacy impact assessment for legal nonprofits.
With this clear, honest map in hand, you can finally move past vague security anxieties and start taking focused, meaningful action. You’ll know exactly which workflows need shoring up first.
Building Your Security Playbook: The Four Core Pillars
Once you have an honest map of how your data moves, you can stop playing defense and start building a proactive security playbook. A strong data security strategy for court self-help organizations isn’t a hundred-page binder that collects dust. It’s a living guide built on a few core governance pillars that give your team clear rules of the road.
This playbook creates the structure to make consistent, defensible decisions about protecting client information. The goal isn’t to become a cybersecurity expert overnight; it’s about establishing a solid baseline of control and showing your board, funders, and community that you’re a responsible steward of their trust. Let’s focus on the four pillars that deliver the most impact.

Pillar 1: Get Smart About Access Controls
The principle of least privilege is your single most powerful security tool. It’s a simple concept: people should only have access to the specific data they absolutely need to do their jobs—and nothing more. An intern helping with client intake has no business seeing sensitive case notes from three years ago.
While “role-based access control” might sound technical, it’s really an organizational exercise first.
- Think Roles, Not People: Group your staff and volunteers by their function: “Intake Specialist,” “Supervising Attorney,” or “Pro Bono Coordinator.”
- Map Data to Roles: For each role, list the exact systems and types of data they need to access. Be specific.
- Master the Offboarding Checklist: This is critical. Create a simple, mandatory process for immediately revoking all system access the moment a person leaves. This common failure point leaves a massive, gaping security hole.
What we stop doing: Granting everyone “admin” access just to make things easier. It’s a common shortcut that creates enormous risk and makes it impossible to determine who did what when something goes wrong.
Pillar 2: Actually Vet Your Technology Vendors
Your security is only as strong as your weakest vendor. All those cloud-based tools you rely on for case management, document storage, and communication are holding your most sensitive data. You must have a basic process for checking their security practices before you sign a contract.
You don’t need to conduct a deep technical audit. A simple checklist can get you 90% of the way there by helping you ask the right questions.
- Do they encrypt data both when it’s moving (in transit) and when it’s stored (at rest)?
- Is Multi-Factor Authentication (MFA) a standard feature?
- Can they show you a copy of a recent security audit, like a SOC 2 report?
- What’s their exact process for letting you know if they have a data breach?
Just asking these questions sends a strong signal to vendors that security matters to you. It also gives you crucial documentation if an incident ever occurs.
Pillar 3: Move Training From a Chore to a Culture
That annual, check-the-box security training video isn’t cutting it. Your staff and volunteers are your human firewall, but they need ongoing, practical reinforcement to spot real-world threats. Effective training must be short, relevant, and continuous.
Instead of generic slideshows, focus on common attacks.
- Run Phishing Simulations: Regularly send fake phishing emails to give your staff hands-on practice identifying suspicious requests in a safe environment.
- Talk Through Scenarios: Use five minutes in a team meeting to pose a real-world dilemma: “You get an urgent email that looks like it’s from the executive director, asking for a list of client names for a report. What do you do?”
- Drill Secure Data Handling: Constantly reinforce simple rules, like never sending unencrypted sensitive client information over email.
This approach builds a true culture of security awareness, turning passive compliance into an active defense.
Pillar 4: Draft a Simple Incident Response Plan
When a security incident happens—and it will—panic is your worst enemy. Whether it’s a lost laptop, a ransomware attack, or an accidental data leak, having a simple, one-page incident response plan gives your team a clear guide to follow in a high-stress moment.
Your plan doesn’t need to be an encyclopedia. It just needs to answer four key questions:
- Who’s in charge? Designate one person as the point person to lead the response.
- Who do we call first? List the contact info for your IT support, leadership, and legal counsel.
- What are the first three steps? For example: Isolate the affected device, notify the point person, and do not delete any data.
- How do we communicate? Outline who is responsible for talking to staff and, if necessary, the public.
For those looking to formalize these pillars into a more structured program, this comprehensive Information Security Management System (ISMS) guide is a resource our partners often find valuable. You can also see how these principles apply specifically to the justice sector in our overview of cybersecurity strategy consulting for court services organizations.
By putting these pillars in place, you transform security from an abstract worry into a set of manageable, mission-aligned practices.
Moving From Quick Fixes to Long-Term Resilience
You’ve patched the most immediate holes and things are starting to feel less chaotic. Your team feels safer, and your board can see you’re making real progress. Now it’s time to shift from frantic firefighting to building a security program that will last.
This is where a long-term roadmap comes in. It’s how you turn one-off fixes into a deliberate, sustainable strategy that grows with your organization. This isn’t just a technical to-do list; it’s a powerful tool for communicating with your board and funders. It proves you’re thinking strategically about risk and are serious about protecting your mission. It completely changes the conversation from, “What happens if we get breached?” to “How do we build a foundation that supports our growth and protects our community?”
Tame Your Technology Sprawl
One of the biggest hidden risks in any organization is “tool sprawl.” It’s that messy collection of redundant, unmanaged, and often insecure apps that people have adopted over the years. Your long-term plan must include a methodical effort to rein this in and standardize your core technology.
This means getting decisive about what you use:
- One tool per job: Pick a single, official platform for case management. One for document storage. One for team chat. No more ambiguity.
- A sunset plan for old software: Once you’ve chosen your official tools, create a clear timeline to migrate data from the old systems and then turn them off for good. This gets rid of forgotten closets full of sensitive data.
- End the “workaround” culture: When you provide reliable, well-supported tools, staff no longer have an excuse to use personal Dropbox accounts or unsecured spreadsheets to get their work done.
Budget for Security Like You Budget for Rent
For too long, security has been treated as a one-time project or an emergency line item. A truly mature organization treats it as a core operational cost, just like rent or payroll. Your one-to-three-year plan needs to build security right into your annual budget.
This is a fundamental mindset shift. Stop seeing security as a cost center and start framing it as a mission-enabler. A secure system is what allows you to serve more clients, partner with other agencies, and confidently share your impact.
Your budget should account for the recurring costs of things like password manager licenses for the whole team, ongoing security awareness training, and maybe even an annual third-party risk assessment. Making these costs predictable turns security into a sustainable practice, not a constant funding crisis.
Find a Rhythm for Regular Risk Reviews
The threats you face today won’t be the same a year from now. Your organization will change, too—new programs, new staff, and new tech all introduce new vulnerabilities. Your long-term roadmap should establish a predictable rhythm for checking in on your security posture. Maybe that’s a deep-dive security risk assessment once a year, or a lighter review every six months.
This regular check-in ensures your security playbook and incident response plans don’t get stale. It keeps security on the radar for leadership and stops you from slowly sliding back into old, reactive habits.
Weave Privacy into the Fabric of Every New Project
Finally, a truly resilient strategy is about looking ahead. As your organization develops new programs or launches new tools for clients, security and privacy can’t be an afterthought you bolt on at the end. It has to be baked in from the very beginning. This principle is often called privacy by design.
The challenges here are very real. A 2024 Department of Justice report pointed out how many legal aid groups get stuck navigating complex data security and privacy issues, especially with sensitive information from vulnerable clients. It’s a tough spot to be in: you have to collect personal data to help people, but you also have to protect them from the harm a breach could cause. You can dig deeper into these systemic challenges in legal aid data infrastructure.
For your team, this means asking some tough questions before a new project even gets off the ground:
- What is the absolute bare minimum of client data we need for this to work?
- How are we going to store and send this new data securely?
- Who on our team really needs to see this information?
By embedding these questions into your process for designing new programs, you create a culture where protecting client data is everyone’s job. That proactive mindset is the real sign of an organization that has moved beyond just fixing problems to truly building for the future.
What to Do Next Week
Reading about strategy is one thing; doing something is what makes the difference. We’ve walked through the big picture of mapping data and building a governance framework, but real change starts with a single, focused conversation. This is your tangible next step—something concrete you can do in the next 30 days to get the ball rolling.
Forget about launching a sprawling, months-long audit that drains everyone’s time and energy. Instead, start small with a high-impact exercise that builds momentum.
Book a 1-Hour Data Risk Huddle
Pull your core leadership team into a room—think Executive Director, COO, and your key program leads. The objective here isn’t to solve every single problem. It’s simply to agree on what matters most right now.
Here’s a simple, three-part agenda that works every time:
- Silent Brainstorm (15 mins): Hand out sticky notes and have each person quietly write down their top three data security worries. What specific scenarios keep them up at night? You’ll likely see things like, “Client data being emailed insecurely to a partner,” “A former employee who might still have access to our case files,” or “Our grant report numbers don’t match our intake logs, and I don’t know why.”
- Group and Theme (20 mins): Stick all the notes on a whiteboard. As a group, start clustering them into patterns. You’ll quickly see where the collective anxiety is focused—maybe it’s all about insecure referrals, messy intake data, or a completely inconsistent offboarding process.
- Vote and Prioritize (15 mins): Give everyone three dot stickers or marker votes. Ask them to place their votes on the themes they believe pose the most immediate risk or cause the most friction for staff. The results will give you a clear, team-endorsed mandate for your first quick win.
This focused huddle cuts through all the noise and analysis paralysis. It isn’t a full-blown data security strategy for court self help organizations; it’s just the starting block. But it’s powerful because it replaces vague fears with a shared, prioritized list of actual problems people want to fix.
Now, I’ll leave you with one honest question to ask your team. Answering it is the true first step from feeling overwhelmed to being in control.
If we could only fix one broken workflow that exposes client data or burns out our staff, which one would it be?
Common Questions and Practical Answers
Putting together a real-world data security strategy for court self-help organizations always brings up tough questions, especially when you’re juggling a tight budget and an overwhelming caseload. Let’s tackle some of the most common ones we hear from folks on the front lines.
How Can We Possibly Afford This on Our Budget?
Good news: your biggest security wins often have little to do with buying expensive new software. It’s more about being smart with the tools you already have and refining your internal processes.
You can make a huge impact right away with these low-cost, high-impact moves:
- Turn on Multi-Factor Authentication (MFA). Go into your existing email and case management systems and mandate it. This is almost always a free, built-in feature and it’s your single best defense against someone guessing a password and walking right in.
- Get a password manager. Instead of letting staff use weak, recycled passwords (or worse, sticky notes), standardize a free or low-cost password manager. This immediately eliminates a huge source of risk.
- Stop collecting so much data. The most secure data is the data you never had to begin with. Take a hard look at your intake forms and ask, “Do we really need this piece of information to help this person?” If not, get rid of the field.
These aren’t about a capital investment; they’re about investing a bit of time and focus where it counts most.
How Do We Train Staff and Volunteers Who Aren’t Tech-Savvy?
Forget the idea of turning everyone into a cybersecurity guru. Your goal is much simpler: build a few core, security-conscious habits. Ditch the long, once-a-year training videos that everyone forgets. Instead, focus on short, consistent reinforcement.
Try weaving quick security drills into your regular team meetings.
- “What If?” Scenarios: Spend five minutes on a real-world situation. “An email comes in from what looks like a partner agency, and they’re urgently asking for a client list for a grant report. What’s the next step?” Just talking it through builds the right instincts.
- Spot the Phish: Pull up a few examples of actual phishing emails your team has received. Point out the tell-tale signs—the weird sender address, the sense of urgency, the suspicious link. This makes the threat feel real and less abstract.
The aim is to create a culture where people feel empowered to pause and ask, “Hang on, does this feel right?” before they click.
We Don’t Have an IT Expert. How Can We Vet New Vendors?
You don’t need a technical background to ask smart questions. In fact, having a simple vendor security checklist is one of the most powerful tools you can have. It helps you do your homework and shows your board and funders that you’re taking this seriously.
Before you sign any contract for a new piece of software, ask these non-negotiable questions:
- Can you share a recent third-party security audit, like a SOC 2 report?
- Is our organization’s data encrypted both when it’s being sent (in transit) and when it’s being stored (at rest)?
- Is MFA a standard, mandatory feature for every single user account?
- If you have a data breach, what is your exact process for notifying us?
A vendor that stumbles, deflects, or can’t provide clear answers to these basic questions is waving a massive red flag. Reputable partners expect these questions and will have the answers ready for you.
Creating a practical, believable plan for your organization’s technology and data security is a journey, not a sprint. If you’re ready to trade constant worry for calm confidence, CTO Input provides the experienced, mission-aligned leadership to get you there. We specialize in building simple, defensible roadmaps that earn the trust of boards, funders, and the communities you serve.

