You are a CEO or COO on the senior leadership team who is spending more on tech and security and still not sleeping well. The board of directors asks about ransomware, AI misuse, and vendor risk. Lenders ask about controls and continuity. You nod, but inside you are asking a more basic question:
How much cyber risk can your balance sheet actually carry before it hurts growth, margins, or covenants?
In 2025, the average global breach costs about $4.44 million, and in the US it jumps to $10.22 million per incident. Ransomware events now average around $5.13 million in total cost, even before counting the ransom itself. For a company with $2 million to $250 million in revenue, that is not a “technology issue.” That is an earnings, cash, and board confidence issue.
This article gives you a clear way to define a cyber risk appetite, tied to your real financial capacity and business strategy, not fear or vendor pressure. CTO Input acts as the neutral guide that sits on your side of the table and helps you translate cyber exposure into simple business language and decisions.
Why Cyber Risk Appetite For Executives Starts With Your Balance Sheet
 At its core, “cyber risk appetite for executives” means this:
At its core, “cyber risk appetite for executives” means this:
How much cyber pain are you willing to accept and still hit your growth, profit, business objectives, and covenant targets for executive leadership?
This is not a technical metric. It is a money question.
Your balance sheet already answers part of it. You have:
- Equity
- Cash and available credit
- Debt covenants and ratios your lenders care about
- Investor expectations on earnings and growth
Imagine your company has $20 million in equity. A single breach in the US can easily cost $4 to $10 million. That is 20 to 50 percent of equity at risk in one bad year. If your annual profit is $5 million, a serious ransomware event can wipe out the entire year.
Mid-market companies sit in a tough spot. You are big enough to be a prime target, but not big enough to copy the security playbook of a global bank. You do not have a 20 person security team. You do have real compliance risk, customer promises, and thin margins.
Cyber risk appetite has to connect to:
- How much earnings volatility you can live with
- How much short term cash pain you can absorb, reflecting your financial resilience
- How much disruption your operations can take before customers leave
- How much room you have before covenants or ratings are at risk
The goal is not zero risk. The goal is to make cyber decisions with numbers, not jargon. Money, time, and impact become your language, instead of tools, acronyms, and fear.
From vague fear to clear numbers: what risk appetite really is
Most leadership teams live with a vague fear of cyber events. They hear scary stories, buy more tools, and hope they did enough.
Risk appetite is your line in the sand. It is the level of loss and disruption you are willing to accept in a normal year, helping to shape your risk culture.
Risk appetite is different from:
- cyber risk tolerance (the wiggle room around that line)
- Risk tolerance (the day to day controls and thresholds)
- cyber risk tolerance, which provides the operational buffer to manage deviations from appetite in cyber scenarios
You do not need to debate terms. You need simple risk appetite statements like:
- “We will not accept a realistic cyber event that could cost more than 5 percent of shareholder equity in any one year.”
- “We will keep our likely cyber loss in a 12 month period below one quarter of last year’s profit.”
Those statements shift the conversation. Now your cyber risk appetite is clear, and every project, policy, and vendor pitch can be measured against it.
How much cyber loss can your balance sheet actually absorb
Start with a quick mental model. No spreadsheet required.
- Look at equity and cash
How much equity do you have? How much cash and available credit could you tap in a real crunch? This defines your solvency threshold and overall risk capacity. - Think about covenants and expectations
How much could profit drop before you breach a covenant, cross the profitability threshold, or trigger a serious board conversation? - Ask what size loss forces painful moves
At what loss level, in any 12 to 24 month period, would you need layoffs, emergency funding, or delayed growth investments?
For example, consider a firm with:
- $15 million in equity
- $4 million annual profit
- $3 million available credit headroom
A single cyber event that costs $3 to $5 million in response, downtime, and lost revenue could:
- Erase an entire year of profit
- Use up most of your credit room
- Push your leverage and coverage ratios into red territory
If that feels like “too much,” then your appetite might sound like:
- “We can absorb $750,000 to $1.5 million in cyber loss over 12 to 24 months without breaking our growth plan.”
Now you have a range. Not perfection, but clarity. That range sets the stage for every later decision.
What recent attacks say about mid-market balance sheet risk
Recent attacks on brands like Marks & Spencer and Co-op in 2025 led to hundreds of millions in lost sales and profit. You are not that size, but the pattern matters.
When retailers shut down digital channels for weeks, or manufacturers halt production after a ransomware hit, the damage piles up fast: lost revenue, overtime, consultants, legal fees, brand repair. Reports show that mid-market companies often pay 13 percent more per breach than larger peers, in part because they lack internal resources.
According to global studies, ransomware costs around $5.13 million on average, and mid-sized firms under 500 employees see breach costs around $3.31 million. For many in the mid-market, that is not a bad quarter. That is a near miss on survival.
Sources like the World Economic Forum’s view on a cyber risk balance sheet and insurers tracking cyber insurance trends point to the same story. Cyber is now a balance sheet topic.
This is why risk appetite must be set before an incident, not while you are in the middle of a takedown call with your board at midnight.
A Simple Framework To Size Cyber Risk Against Your Balance Sheet
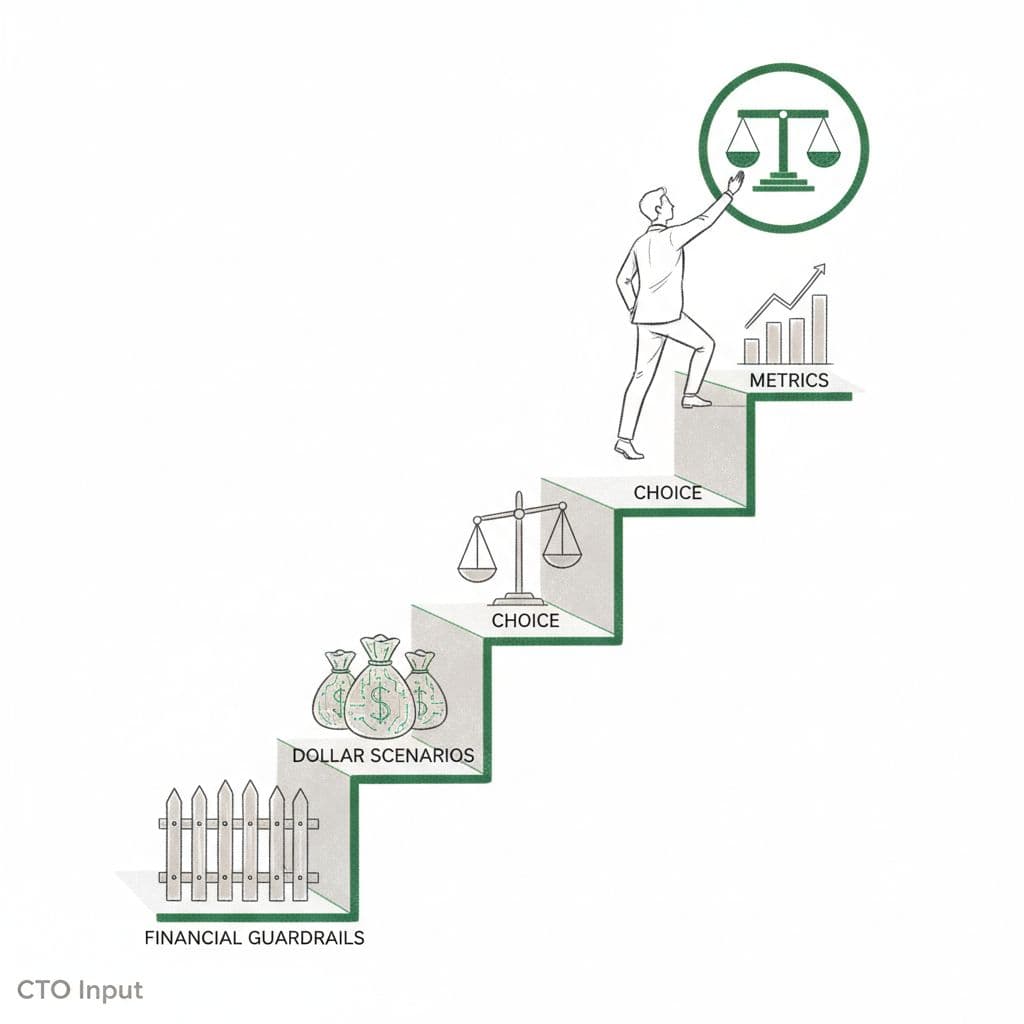
 You do not need a full time CISO to connect cyber risk exposure to financial capacity. You need a simple risk management framework at the executive level.
You do not need a full time CISO to connect cyber risk exposure to financial capacity. You need a simple risk management framework at the executive level.
Think in four moves.
Step 1: Set financial guardrails for acceptable cyber loss
First, define your guardrails or risk thresholds in plain financial terms.
Pick a maximum acceptable financial loss from:
- A single event
- All cyber events in a year, including cyber risk
Simple rules of thumb:
- “No single cyber incident should be likely to cost more than 3 percent of equity.”
- “Total cyber losses in any year should stay below 25 percent of last year’s profit.”
Use ranges, not false precision. It is enough to say, “Our guardrail or risk threshold is $1 to $2 million in a year, beyond that we accept severe pain.”
Write it down as a one paragraph risk appetite statement among your risk appetite statements you can share with your board of directors. That statement becomes your north star.
For more context on how executives connect risk appetite and tolerance, you can review this clear breakdown of risk appetite vs risk tolerance.
Step 2: Turn likely cyber events into dollar scenarios
Next, turn jargon into a short list of business scenarios using cyber risk quantification (CRQ). For most mid-market firms, four are enough:
- A ransomware shutdown for one week
- A customer data security breach with thousands of records exposed
- A vendor outage that stops billing, ordering, or production
- A business email compromise that sends money to a fraudster
For each scenario, list cost buckets:
- Lost revenue while you are offline
- Extra labor, overtime, consultants, and recovery work
- Legal, regulatory, and notification costs
- Discounts, customer churn, and brand repair
Have finance sit with IT or your external partner and put rough dollar ranges on each bucket via cyber risk quantification (CRQ). No one will be exactly right, and that is fine.
Now compare each scenario total to your Step 1 guardrails. If your “likely” ransomware hit models at $3 million and your appetite is $1 to $2 million, that gap is the real issue, not the tool list.
If you want a deeper dive into scenario based thinking, some executives find it useful to skim a framework like quantifying and operationalizing cyber risk appetite.
Step 3: Choose your cyber risk appetite and make tradeoffs
This is where leadership judgment comes in.
Look at your scenarios against the guardrails and ask:
- Are we too hungry for risk or beyond our risk tolerance? (Most scenarios sit above our limits.)
- Are we too risk averse or below our risk tolerance? (We are spending heavily, yet our scenarios still do not shrink, or we are choking growth projects.)
- Are we close to “about right,” with a few clear gaps to close?
Choosing a cyber risk appetite is about tradeoffs and quantitative appetite:
- A higher risk appetite means more free cash in the short term, but a higher chance of a shock to earnings or equity.
- A very low cyber risk appetite means heavy spend and strong controls, but can slow innovation and tie up capital through resource allocation and capital allocation.
Your written risk appetite statement among your risk appetite statements should cover:
- Maximum financial impact you will accept
- Maximum downtime for critical systems
- How much customer data exposure you will treat as acceptable risk
Keep it to one page. Your board should be able to read it in under five minutes.
Step 4: Use simple metrics and reviews, not endless dashboards
You do not need 60 security metrics. You need a handful tied to money and time for strategic decision-making.
For example:
- Number of critical cyber incidents in the last 12 months, including cyber risk
- Estimated financial exposure of your top three scenarios
- Hours of downtime for critical systems in the last year
- Exposure linked to key vendors and partners
Review these key risk indicators (KRIs) at least twice a year in executive and board meetings as part of security governance, alongside other enterprise risks.
Many mid-market firms bring in a fractional CISO (Chief Information Security Officer) to own this view, so the CEO is not stuck translating technical noise into strategy. A good advisor treats cyber like any other financial and operational risk, not a separate mystery.
If you want to see how other finance leaders now frame cyber as a balance sheet topic, this overview of cyber as a financial risk is useful background.
 ## When To Call In Help: Aligning Cyber Risk Appetite With Growth Plans
## When To Call In Help: Aligning Cyber Risk Appetite With Growth Plans
Signals your cyber risk appetite is out of sync
You do not need a breach to know your cyber risk appetite and exposure are misaligned. The signals often show up earlier:
- Board questions you cannot answer with numbers
- Cyber insurance renewals that keep getting more complex and expensive
- Vendors pushing tools you cannot tie back to real risk reduction
- Repeated outages, suspicious emails, or near misses that never quite get closed despite security measures
- Tension between finance and IT about spend and priorities
These are signs that your balance sheet might be carrying more cyber risk than you think, or that you are tying up too much capital without clear risk reduction.
External sources, like reports on cyber insurance risks and trends or overviews of expected cyber attack losses, confirm that the pressure will only grow. AI driven attacks, data privacy questions, and vendor chains add more weight each year.
How a neutral technology advisor helps protect your balance sheet
A fractional CTO, CIO, or CISO acts as your neutral translator.
For a mid-market firm, that usually means:
- Building a simple risk appetite and tolerance model in financial terms
- Turning incidents and weaknesses into clear dollar exposure
- Prioritizing a short list of fixes instead of a never ending backlog
- Sequencing investments to match your growth and cash flow
The outcome is not another dashboard. It is:
- Cleaner numbers
- Fewer surprises
- Faster decisions
- Better board and lender conversations
CTO Input focuses on exactly this space for companies between $2 million and $250 million in revenue. The work often starts with a short discovery or diagnostic that maps your current exposure against your balance sheet and growth plan.
 ### A low risk next step to right size your cyber risk appetite
### A low risk next step to right size your cyber risk appetite
You do not need a six month program to start.
A practical first move:
- Draft a one page cyber risk appetite that sets rough financial guardrails.
- Compare that page to your last annual results and current balance sheet.
- Note where your likely scenarios look bigger than your stated appetite.
If you want a sounding board, schedule a short call with CTO Input at https://www.ctoinput.com. Use that time to test your numbers, your scenarios, and your tradeoffs with a neutral expert who speaks both finance and technology.
You can also deepen your understanding by exploring more guidance on the CTO Input blog at https://blog.ctoinput.com, including topics like AI risk, vendor exposure, and practical technology roadmaps for mid-market leaders.
Conclusion
Your balance sheet already carries cyber risk. The real question is whether your cyber risk appetite matches your true risk appetite and growth plans, or if it is quietly out of line with what your board and lenders expect.
The path is straightforward. Set clear financial risk thresholds, translate likely cyber events into dollar scenarios, choose and document your risk appetite, then review it on a steady rhythm. When you do that, board meetings hold fewer surprises, technology spend lines up with strategy, and your balance sheet can absorb the financial loss you are actually willing to take.
If you want a partner in that work, visit https://www.ctoinput.com to see how fractional technology leadership can help. Then spend a few minutes with the articles on https://blog.ctoinput.com to turn cyber risk from a late night worry into a managed part of your growth story that aligns with your cyber risk appetite and executive leadership.