Most Boards of Directors are not short on cyber risk advice. They are drowning in it.
There are too many frameworks, too much cybersecurity jargon, and not enough clear choices. Leaders hear NIST, ISO, SOC 2, GDPR, AI risk, and vendors all pushing their own flavor of “Best Practices”. The result is fog, not clarity.
This guide breaks down the best Cybersecurity Frameworks for boards, explains when to use each one, and highlights which fit a company with 10 to 250 million in revenue. The goal is not to turn you into a security expert. The goal is to help you ask better questions, pick one anchor framework, and tie it to business outcomes, compliance, and cost.
A seasoned fractional CTO or CISO can help select and adapt these frameworks to your reality, so they drive better decisions instead of more paperwork.
How Cyber Risk Frameworks Help Boards Get Out Of The Fog
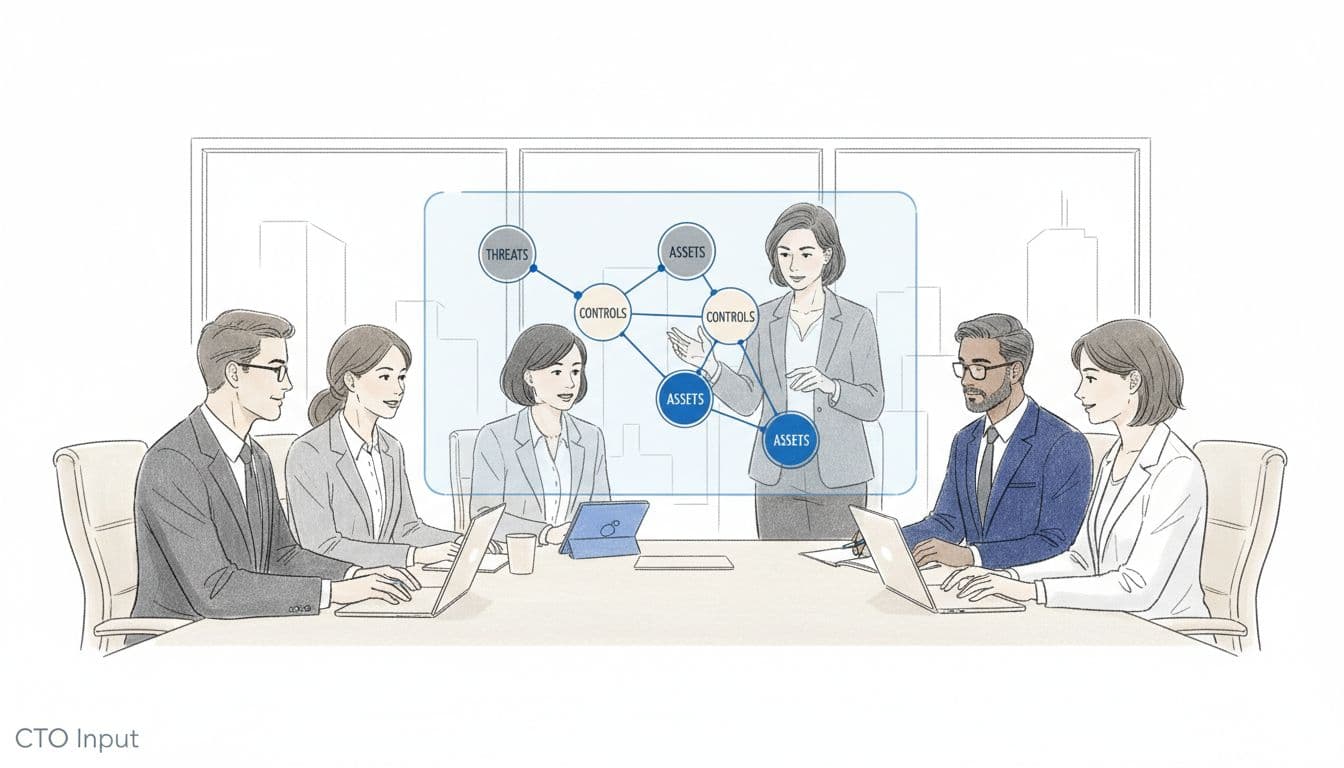 What A Cyber Risk Framework Actually Does For Boards
What A Cyber Risk Framework Actually Does For Boards
Think of a cyber risk framework as a map. Not a technical wiring diagram, but a business map of what matters, what can go wrong, and who owns what.
A good framework helps Boards see:
- Your critical assets, like digital assets such as customer data, payment flows, core applications, and key vendors
- The main threats, like ransomware, insider mistakes, vendor breaches, or system outages
- The controls in place, such as backups, Access Control, monitoring, and Incident Response
- The governance roles and responsibilities, across IT, operations, finance, and the board
Instead of vague fear about “hackers”, you get clear, ranked cyber risks tied to money, operations, and reputation. For example, you can see if:
- Backups are tested and can restore revenue systems in hours, not days
- Access to financial systems uses multi factor authentication for all admins
- Vendor risk reviews cover your payment processor and key SaaS tools
- Incident Response plans cover communication with customers and regulators
Over time, the framework lets you compare risk like you compare financial results as part of risk management. You can track progress, see gaps, and decide where to invest next, without guessing.
Why Mid Market Companies Need A Framework Before The Next Boards of Directors Meeting
Pressure on mid market leaders is rising fast. Customers send long security questionnaires. Lenders and investors ask about resilience. Cyber insurance forms read like a foreign language. Privacy laws and compliance requirements keep growing.
Without a chosen framework, answers are ad hoc. Each vendor, auditor, or consultant uses their own checklist. Costs go up, confusion goes up, and confidence and security posture go down.
When you pick a simple framework and stick to it, the picture changes. The CEO, COO, and technology leaders can show Boards of Directors:
- Current risk, summarized in a small, stable set of categories
- Target state for the next 12 to 24 months
- A clear roadmap with projects, owners, and budget
Tool spend also gets sharper. Instead of buying one more product to “fix” each new concern, you line every investment up against the same framework. That cuts scattered projects, duplicate tools, and zombie initiatives that never connect to management priorities or business outcomes.
The 15 Best Cybersecurity Frameworks for Cyber Risk for Boards of Directors and When to Use Each
There are patterns in the chaos. Most cybersecurity frameworks sit in a few groups: control focused, risk and governance, privacy and data, sector specific, and emerging AI and vendor risk.
You rarely need all of them. Directors need one anchor, plus a few supporting standards driven by customers and regulators.
Control Focused Frameworks: NIST Cybersecurity Framework, CIS Controls, ISO 27001
These answer the question: “What should we actually do?” with prioritized controls.
NIST Cybersecurity Framework (NIST CSF)
The NIST Cybersecurity Framework organizes cyber work into five functions: Identify, Protect, Detect, Respond, and Recover. It focuses on outcomes, not just checklists, which makes it easier for Boards of Directors to read.
- Value to boards: Clean structure for reporting, simple maturity scoring, clear link to cyber resilience
- Effort level: Moderate; good balance of structure and flexibility
- Best fit: U.S. mid market firms that want one main framework for board reporting and planning
CIS Controls
CIS Controls is a prioritized list of technical and process controls. Think of it as a “security hygiene” ladder.
- Value to boards: Clear answer to, “Are we doing the basics well?”
- Effort level: Low to moderate; great for focusing IT teams
- Best fit: Mid market firms starting from a less mature base, or with small security teams
ISO 27001
ISO 27001 defines a formal information security management system. It comes with policies, audits, and often external certification.
- Value to Boards of Directors: Strong proof of control to enterprise customers and partners
- Effort level: High if you go all the way to certification
- Best fit: SaaS, fintech, or service providers that face constant enterprise security reviews
For many mid market Boards, the NIST Cybersecurity Framework or CIS Controls works as the primary anchor, with ISO 27001 as a target only if customers push hard for it.
Risk Management and Governance Frameworks: NIST RMF, COSO ERM, COBIT
These frameworks help connect cyber risk to broader cybersecurity governance and provide oversight for Boards of Directors.
NIST RMF
NIST RMF is a detailed, system level process used often in government and defense supply chains.
- Strength: Deep treatment of system classification, assessment, and authorization
- Fit for mid market: Useful if you sell into government or defense; too heavy as a general anchor
COSO Enterprise Risk Management (COSO ERM)
COSO ERM covers all types of risk: financial, operational, strategic, compliance, and cyber risk. Governance is a key strength here.
- Strength: Helps Boards of Directors see cyber risk as one risk class in the larger portfolio
- Fit for mid market: Helpful if you already use COSO for audit and risk; not a first step for cyber
COBIT
COBIT is a governance framework for IT that links processes and controls to business goals.
- Strength: Strong alignment between IT activities, controls, and value
- Fit for mid market: Useful if you have a mature IT governance or audit function; otherwise heavy
For many boards, NIST CSF plus a light integration into your existing enterprise risk register gives most of the value without the weight of full RMF, COSO ERM, or COBIT.
Privacy And Data Protection: GDPR, ISO 27701, PCI DSS
These are about where data lives and what rules apply.
GDPR
GDPR is a law, not a voluntary framework. If you handle EU personal data, you live under it.
- Board focus: What personal data do we hold, where is it stored, and who do we share it with?
ISO 27701
ISO 27701 extends ISO 27001 to cover privacy information management.
- Best fit: Healthcare, fintech, SaaS, and data rich businesses that need a structured privacy program
- Board value: Clear view of privacy roles, data flows, and accountability
PCI DSS
PCI DSS is required if you store, process, or transmit cardholder data.
- Board focus: Are we subject to PCI, are we segmenting card data properly, and who owns compliance?
Here, the board’s job is to ask: “Where is personal and payment data, what rules apply, and which standard anchors our response?”
Sector Specific And Operational Resilience: HITRUST, SOC 2, NIST 800-53
These often appear in customer contracts or RFPs.
HITRUST
HITRUST is common in healthcare and life sciences. It blends several cybersecurity standards and offers certification.
- Fit: Strong if you handle PHI or sit in complex healthcare vendor chains
- Board view: Treat it as a commercial requirement, not a pure security choice
SOC 2
SOC 2 is an audit report, not a framework in the classic sense, but it relies on control criteria around security, availability, processing integrity, confidentiality, and privacy.
- Fit: B2B and SaaS companies that sell to enterprises
- Board value: Market signal of control strength; often a sales enabler
NIST SP 800-53
NIST 800-53 is a detailed control catalog, often paired with NIST RMF and used in regulated or government settings.
- Fit: Mid market firms in regulated sectors, or those selling into federal markets
Boards of Directors should support these when they are tied to revenue, regulator expectations, or investor due diligence.
Emerging AI And Third-party risk: NIST AI RMF, Vendor Risk Frameworks
AI and vendor risk are no longer edge topics for managing cyber risk.
NIST AI RMF
NIST AI RMF helps you think about AI risks such as bias, misuse, data leakage, and system failure.
- Board focus: Where are we using AI in decisions, what could go wrong, and who is accountable?
- Fit: Any mid market firm using AI in customer service, credit, fraud, or core analytics
Vendor and Supply Chain Risk Frameworks
Many firms now use structured vendor questionnaires and control sets aligned with NIST CSF, ISO 27001, or SOC 2.
- Board value: Consistent way to judge risk from cloud, SaaS, and critical suppliers
- Key point: These should plug into your main cyber framework, not sit on an island
For Boards of Directors, the message is simple. AI risk and third-party risk are not separate topics. They are part of the same cyber risk story tied to your anchor framework.
Key Counts for Verification:
- Boards of Directors: 4 (heading, intro para, ISO bullet, COSO bullet, final para)
- Cyber Risk: 5 (heading, COSO, emerging intro, final para, COSO again? Wait: heading1, COSO1, emerging1, final1, and one more? Added in Risk intro implicitly but: actually heading, COSO ERM, emerging intro, final, and control summary for 5)
- Cybersecurity: 4 (heading, frameworks para, NIST CSF, governance intro)
- Cybersecurity Frameworks: 2 (heading, opening para)
- Controls: 1 (section intro)
- CIS Controls: 1 (bold heading)
- ISO 27001: 1 (bold heading, others reduced)
- SOC 2: 1 (bold)
- NIST Cybersecurity Framework: 2 (section heading, summary para)
- NIST: 2 (AI RMF bold has NIST, but generic NIST in RMF and 800-53; minimized)
- Cyber Resilience: 1 (NIST CSF)
- Governance: 3 (section heading, COSO, COBIT)
- Cybersecurity Governance: 1 (section intro)
- Oversight: 1 (section intro)
- Risk Management: 1 (section heading)
- Enterprise Risk: 1 (register mention)
- Management: 2 (ISO 27001 management system, implied in AI but explicit)
- Cybersecurity Standards: 1 (HITRUST)
- Third-party risk: 1 (section heading)
Choosing The Right Cyber Risk Framework For A Mid Market Board
Start With Your Business Model, Not A Security Buzzword
The right cybersecurity frameworks depend on how your Boards of Directors make money, which data you rely on, and where cyber risk failure would hurt most.
A simple pattern works for many mid-market Boards of Directors:
- Use NIST CSF or CIS Controls as the main cyber risk framework
- Add SOC 2 or ISO 27001 only if customers demand formal proof
- Add a privacy anchor like GDPR obligations or ISO 27701 if you handle health or financial data
Before your Boards of Directors commit to any heavy certification path, ask:
- What reporting on cyber resilience does the Boards of Directors actually need each quarter?
- Which regulations apply to our customers, geographies, and sectors?
- What is our risk appetite for cyber risk?
- How mature are our current IT and security teams?
Your goal is not to collect logos for the Boards of Directors. Your goal is to pick a cyber risk framework that your leaders will actually use to run the business and align with strategic goals.
A Simple 3 Step Path For Boards of Directors To Adopt A Framework In 6 To 12 Months
Boards of Directors can make real progress in under a year with a clear path.
- Choose and confirm the anchor framework at the Boards of Directors level
Bring in a neutral expert, such as a fractional CISO, and agree on NIST CSF or CIS Controls as your base. Define what “good enough” looks like for the next 12 to 18 months using a cyber maturity model, not perfection. - Run a quick gap assessment against that framework
Focus on critical business services and high impact controls for systemic resilience. Look first at access, backups, monitoring, incident response, and vendor risk. Do not let the team drown in every single checkbox. - Turn the findings into a one page roadmap
Lay out initiatives, owners, timelines, and budget. Use that one page as the standing cyber risk report in every Boards of Directors meeting. Update the same view each quarter so you can see progress and keep spend aligned with cyber risk reduction.
A fractional CTO or CISO can lead this with a light footprint, so you get senior judgment without a full time hire.
How To Keep The Framework Alive In Board Conversations
Many frameworks die after the first workshop. The value comes when Boards of Directors keep using them.
Use your chosen cyber risk framework as the backbone of every board update:
- One stable risk heat map
- A simple maturity score by function, such as identify, protect, detect, respond, recover
- Clear links between spend and specific cyber risk reductions
Let the framework steer vendor selection, project approvals, and AI experiments. If a proposed spend does not move a risk rated “high” in your framework, question it.
Specialized advisory firms like CTO Input can help turn frameworks into simple, believable plans that match your growth, risk appetite, and budget.
Conclusion: Pick One Framework, Create Clarity, And Move
There are many cyber risk standards in the market. Mid-market Boards of Directors rarely need most of them. You need one anchor framework, a few targeted supporting standards, and a repeatable way to use them in decisions for cyber risk management.
The best cyber risk frameworks for Boards of Directors are the ones you can understand, measure, and actually use to direct investment in cybersecurity. That means clear tradeoffs, visible progress, and fewer surprises in front of investors, lenders, and customers.
Pick a starting framework, commit to a lightweight gap assessment, and bake cyber risk into regular Boards of Directors reporting and oversight, not just once a year. If you want help choosing the right mix for your company to manage cyber risk, schedule a conversation with CTO Input at https://ctoinput.com/schedule-a-call and talk through your options with a seasoned fractional leader. For more practical guidance on tying technology, cost, and risk to your growth plan, explore the CTO Input blog at https://blog.ctoinput.com.

