A single cyber attack can bring even the most established companies to a standstill, as recent high-profile breaches have shown. The stakes for business leaders have never been higher, with digital threats growing in sophistication and frequency.
This guide to cyber security for business is designed to give you the insight and strategies needed to protect your organization, maintain trust, and turn security into a true competitive advantage.
You will discover the current threat landscape, essential protection strategies, a step-by-step roadmap to secure operations, compliance best practices, future trends, and expert guidance. Real-world examples and actionable solutions will help you strengthen your defenses and stay ahead.
Ready to protect your business and seize new opportunities? Read on to build a resilient foundation for success.
Understanding the Modern Cyber Threat Landscape
The digital world is evolving, and so are the risks. Cyber security for business is no longer just about defending against basic malware. Today’s organizations face a sophisticated mix of threats, each capable of disrupting operations and damaging reputation.
Types of Cyber Threats Facing Businesses
Modern cyber security for business involves navigating a complex threat landscape. Common attack types include:
- Phishing: Deceptive emails or messages tricking employees into revealing credentials.
- Ransomware: Malicious software encrypting files and demanding payment for release.
- Malware: Viruses and trojans that compromise systems or steal data.
- Insider threats: Employees or contractors misusing access, either accidentally or intentionally.
- Supply chain attacks: Adversaries targeting third-party vendors to gain entry.
The numbers are staggering. Ransomware attacks have surged by more than 150% in recent years, while credential theft incidents have jumped dramatically. No sector is immune—retailers, healthcare providers, and manufacturers all face unique risks.
High-profile breaches have resulted in millions lost, regulatory scrutiny, and brand reputation crises. Emerging threats like AI-driven attacks, deepfakes, and vulnerabilities in IoT devices add new layers of complexity. The shift to remote and hybrid work has further expanded the attack surface, making continuous vigilance essential.
For a closer look at how these threats impact real companies, see The three cyber incidents most likely to hit mid-market companies.
The Cost of Cyber Attacks
The financial and operational toll of cyber incidents is significant. Direct costs include system downtime, emergency remediation, and potential legal penalties. Indirect costs, such as loss of customer trust and damage to reputation, often linger much longer.
On average, the cost of a data breach now exceeds $4 million globally. Recovery is rarely straightforward—businesses must rebuild systems, restore lost data, and re-earn client confidence. The burden is especially heavy for smaller organizations, which may lack the resources for rapid recovery.
Cyber security for business is not just a technical issue—it is a fundamental component of resilience and long-term success. Companies must invest in both prevention and rapid response to minimize disruption and mitigate lasting damage.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Building a Cyber Security Foundation for Your Business
Establishing a robust foundation is the cornerstone of effective cyber security for business. Without a strong base, even advanced technologies and tools can fall short. This section explores how leadership, people, processes, and technical controls come together to form a resilient security posture.

Establishing a Security-First Culture
Every successful cyber security for business initiative begins with a culture that prioritizes security at every level. Leadership must champion this mindset, setting clear expectations for all staff. When executives model secure behaviors, employees are more likely to follow suit.
Ongoing employee training is essential. Effective programs use real-world examples, simulated phishing exercises, and regular updates to keep everyone alert. Studies show that over 90% of breaches involve human error or social engineering, highlighting the human factor as the weakest link.
Some companies implement monthly awareness sessions, while others use gamified platforms to make learning engaging. No matter the method, consistent training reduces risk and reinforces the importance of cyber security for business.
Implementing Core Security Controls
Technical controls are the backbone of cyber security for business. Start by deploying multi-factor authentication (MFA) and enforcing strong password policies. This is critical, especially as credential theft surges 160%, making robust authentication a business necessity.
Keep all software and systems updated with the latest patches to close known vulnerabilities. Network segmentation helps contain threats, while endpoint protection shields devices from malware and unauthorized access.
Encrypt sensitive data at rest and in transit. Apply role-based access controls and follow the principle of least privilege, ensuring employees only access what they need. These steps collectively strengthen your defenses and lower the risk of compromise.
Security Policies and Documentation
Clear, comprehensive policies are vital for guiding daily operations and incident response. Develop policies for acceptable use, remote work, and security incident handling. Make these documents accessible and review them regularly to adapt to new threats.
A mid-sized business once suffered a breach due to outdated remote access policies. Regular reviews would have identified and closed the gap before attackers exploited it. Documented procedures also streamline audits and support rapid response when incidents occur.
Building and maintaining strong policies ensures your cyber security for business efforts stay effective and compliant as your organization grows.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com.
Step-by-Step Roadmap: Protecting Your Business from Cyber Threats
Protecting your business from evolving cyber threats requires a structured, step-by-step approach. By following a proven roadmap, organizations can strengthen their defenses, minimize risk, and ensure resilience. This roadmap for cyber security for business provides practical actions for each stage of your journey.
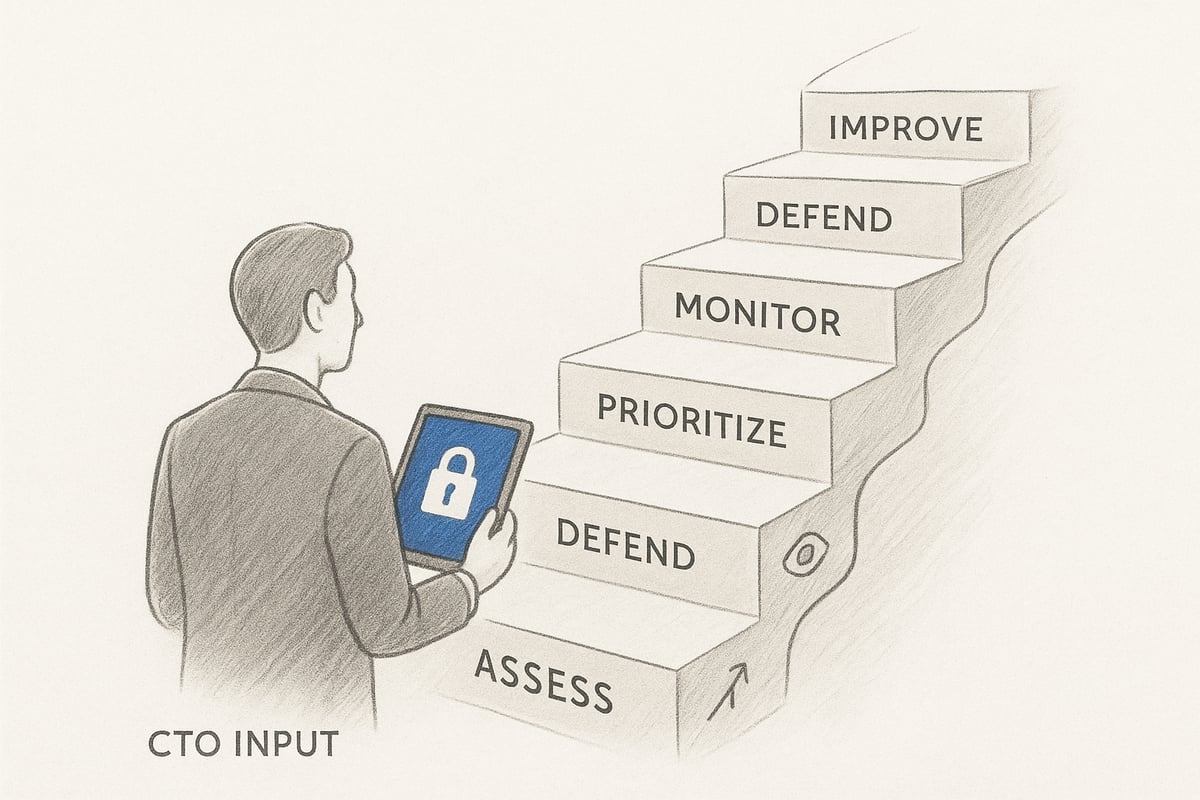
Step 1: Assess Current Security Posture
Begin with a comprehensive assessment of your current environment. Conduct risk assessments to identify vulnerabilities within your systems, applications, and networks. Map out critical assets, sensitive data, and their flows throughout your organization.
- Perform vulnerability scans regularly.
- Inventory all devices and software.
- Document data storage and transfer paths.
This initial step is the foundation for effective cyber security for business, as it reveals where your greatest risks lie and where to allocate resources.
Step 2: Prioritize and Remediate Risks
After assessment, rank identified risks based on their potential business impact and likelihood. Focus first on remediating high-priority vulnerabilities that threaten your most valuable assets.
- Use a risk matrix to visualize priorities.
- Assign clear responsibility for remediation tasks.
- Track progress with documented timelines.
By prioritizing, you ensure that your cyber security for business efforts address the most pressing threats and support operational continuity.
Step 3: Strengthen Defenses
With priorities set, implement robust technical controls to defend against threats. Deploy firewalls and antivirus solutions, configure secure cloud environments, and manage mobile devices safely.
- Enable multi-factor authentication across accounts.
- Update and patch systems promptly.
- Segment networks to isolate sensitive data.
For a forward-thinking approach, explore the Cybersecurity strategy for 2026 resource, which outlines emerging best practices and tools to future-proof your cyber security for business.
Step 4: Monitor and Respond
Continuous monitoring is essential for detecting suspicious activity early. Set up real-time alerts and logs to capture anomalies. Develop and routinely test your incident response plan.
- Establish a response team with clear roles.
- Simulate incidents to practice rapid containment.
- Review lessons learned after each event.
For example, a business that responded immediately to a ransomware alert was able to isolate affected systems and prevent data loss, underscoring the value of a proactive approach to cyber security for business.
Step 5: Review and Improve
Cyber risks are constantly changing, so regular review is critical. Schedule periodic security audits and penetration testing to uncover new vulnerabilities. Use insights from incidents and audits to refine your policies, controls, and training.
- Update documentation with each review.
- Adjust strategies based on new threats.
- Foster a culture of continuous improvement.
By making these reviews routine, you ensure your cyber security for business adapts to the evolving threat landscape.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Navigating Compliance and Regulatory Requirements
Staying compliant is a critical component of cyber security for business. Regulations are evolving, and non-compliance can result in steep penalties and reputational setbacks. Understanding what applies to your organization is the first step to building a secure and resilient operation.

Key Regulations Impacting Businesses
Several major regulations shape the landscape of cyber security for business. The General Data Protection Regulation (GDPR) governs data privacy for organizations handling information of EU residents. The California Consumer Privacy Act (CCPA) affects any business managing personal data of California consumers. PCI DSS is essential for companies processing payment card information, while HIPAA regulates healthcare data protection.
Non-compliance with these laws can lead to significant fines, legal battles, and a loss of customer confidence. For example, failing to meet GDPR requirements has cost global companies millions and forced public apologies. Each industry may also face additional mandates, making it vital to understand your sector's requirements.
Steps to Achieve and Maintain Compliance
Achieving compliance starts with mapping your data flows and identifying gaps in your current controls. Regular assessments can highlight areas of risk and help prioritize improvements. Implementing technical and organizational safeguards, such as encryption and access controls, is essential.
Maintaining audit trails and up-to-date documentation streamlines audits and supports ongoing compliance. For many, leveraging expert resources like Managing compliance and cybersecurity can simplify this process and ensure that your cyber security for business strategy aligns with regulatory demands.
A retail company, for example, reduced risk and improved efficiency by automating compliance checks and staff training. Clear roles and responsibilities help everyone know what is expected.
The Role of Third-Party Vendors
Vendors and service providers are increasingly integrated into business operations, making their security practices a direct concern. Assessing and managing vendor risks is a core part of cyber security for business. This includes conducting due diligence before onboarding new partners and requiring clear security obligations in contracts.
Ongoing monitoring of third-party compliance helps identify changes that could introduce risk. Many breaches have occurred due to overlooked vendor vulnerabilities, highlighting the importance of regular reviews. By making vendor management a routine part of your compliance strategy, you protect both your data and your reputation.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Leveraging Expert Guidance and Strategic Partnerships
Navigating cyber security for business has become a complex, high-stakes challenge. As threats evolve and resources are stretched thin, many organizations realize that experience and external expertise are critical for building resilience.
When to Seek Outside Expertise
Recognizing when your business needs external support is key. Rapid growth, complex IT environments, or limited in-house resources are clear indicators. If your team struggles to keep up with the latest threats, or if incidents have exposed gaps, it is time to consider expert help.
The financial impact of security breaches cannot be overstated. For example, the FBI reports $262 million lost to account takeover scams, underscoring the urgent need for robust cyber security for business. The cost of failing to act can mean lost revenue, reputational harm, and legal consequences.
The Strategic Advantage of Fractional Leadership
Fractional CTO, CIO, and CISO services offer a powerful solution for mid-sized organizations. These experts provide executive-level insights without the overhead of full-time hires. They help align technology, security, and business goals, ensuring your cyber security for business strategy is proactive and scalable.
Key benefits include:
- Access to deep expertise on demand
- Objective assessments and tailored strategies
- Guidance through compliance, audits, and incident response
- Ongoing advisory and training for staff
CTO Input: Business-First Cyber Security Partnerships
CTO Input transforms technology and cyber security for business into a strategic advantage. Their approach is business-first, focusing on your unique needs. Services include fractional executive leadership, security strategy, compliance support, and continuous advisory.
Clients see measurable results:
- Reduced risk and downtime
- Cost savings through efficient solutions
- Accelerated growth and innovation
Engaging with CTO Input is straightforward: start with a complimentary discovery call to assess your needs and outline a partnership path.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com.
Preparing for the Future: Emerging Trends in Business Cyber Security
Businesses must continuously adapt to a rapidly changing digital landscape. As cyber security for business evolves, emerging technologies and sophisticated threats demand new strategies. Staying ahead requires not only robust defenses but also a proactive mindset.
The Rise of AI and Automation in Cyber Security
AI is transforming cyber security for business on both sides of the battlefield. Attackers now use artificial intelligence to create highly targeted phishing campaigns, automate malware deployment, and bypass traditional defenses. According to Microsoft’s 2025 Digital Threats Report on AI-driven cyberattacks, nation-states are leveraging AI to escalate attacks, making them harder to detect and stop.
Defenders, however, are fighting back with AI-powered threat detection, automated incident response, and machine learning-driven analysis. Automation streamlines compliance and reduces human error. For business leaders, investing in AI-enabled tools is becoming essential to keep up with evolving risks in cyber security for business.
Zero Trust Architecture and Beyond
Traditional perimeter-based security is no longer sufficient for cyber security for business. Zero trust architecture assumes that no user or device should be trusted by default, even if they are inside the network. Key principles include verifying identities, enforcing least privilege access, and continuously monitoring user behavior.
Adopting zero trust requires a shift in mindset and practical steps like segmenting networks, implementing multi-factor authentication, and regularly reviewing permissions. As remote and hybrid work expands, zero trust helps organizations reduce exposure and strengthen their overall cyber security for business posture.
Evolving Threats and Security Strategies
The threat landscape continues to shift as new technologies emerge. Quantum computing, deepfakes, and supply chain attacks are becoming real concerns for cyber security for business. For instance, Neuromorphic Mimicry Attacks: Exploiting brain-inspired computing highlights risks associated with advanced computing models.
Building resilience means staying adaptable, investing in ongoing employee training, and proactively updating defenses. Businesses that prioritize continuous learning and anticipate new attack vectors are better positioned to navigate the future of cyber security for business.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com.
You’ve just explored how the right cyber security strategy can turn technology from a source of stress into a real business advantage. Whether you’re facing complex threats, compliance headaches, or just want your teams to move faster and safer, taking the next step is crucial. At CTO Input, we help leaders like you align technology with your business goals—no guesswork, just measurable results. If you’re ready to see where your organization stands and get clear, actionable guidance, let’s talk. Schedule a time for us to dive into your specific challenges and opportunities with a Strategy Call.

