They thought their house was locked. Doors, windows, alarms. Then they found out the spare key had been sitting in a third party’s desk drawer the whole time.
That is what the OpenAI–Mixpanel incident felt like for many leaders watching from the outside. OpenAI’s own core systems were not breached. Instead, attackers hit Mixpanel, an analytics vendor, and pulled data about OpenAI API users from there. The data lived in a tool that most executives would list as “harmless” or “low risk”.
For growth-minded CEOs, COOs, and founders, the message is blunt: your data is not just where you put it. It is where it flows, where it is copied, and where your vendors send it. In this article, we will unpack Lessons from the OpenAI–Mixpanel Incident in plain language and turn them into concrete moves you can apply in your own company.
What Really Happened in the OpenAI–Mixpanel Incident (In Plain English)
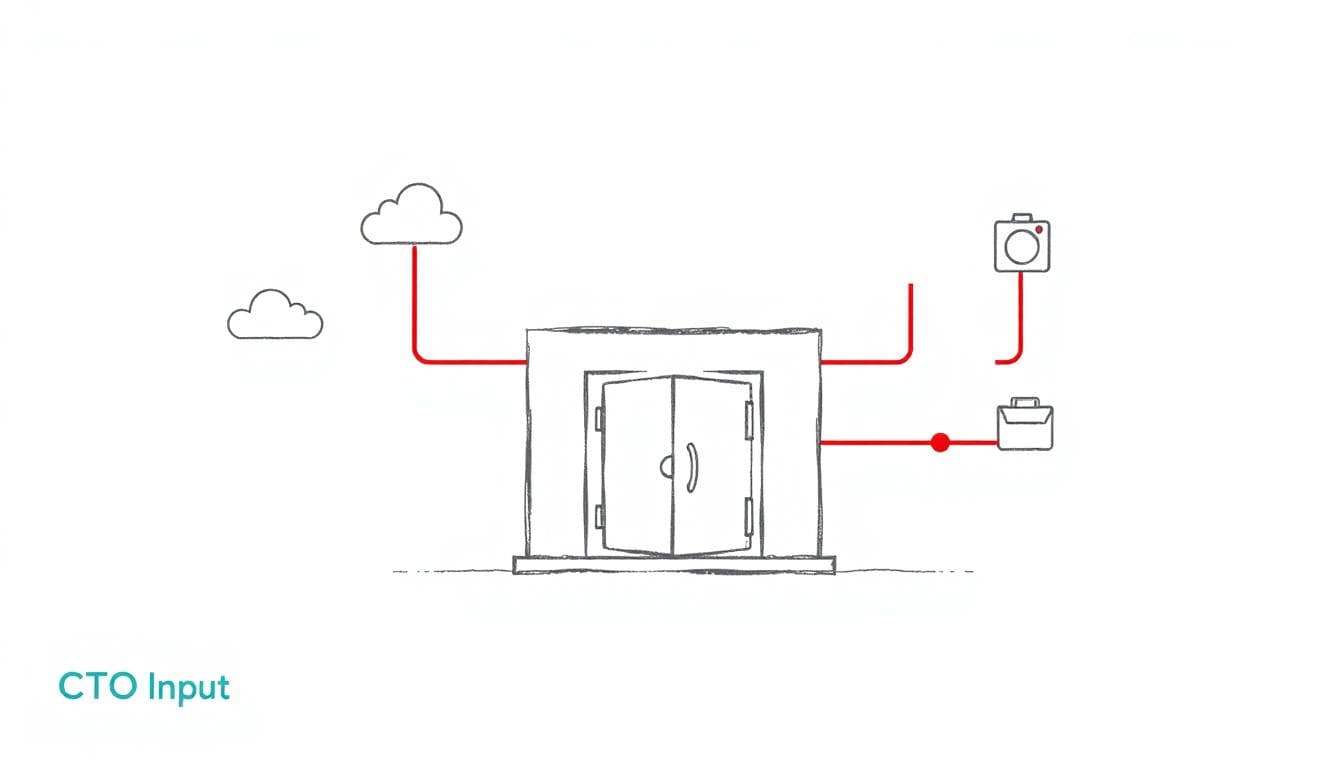
Image created with AI, showing how company data flows into multiple external tools.
A quick recap: how a vendor breach hit OpenAI’s users
OpenAI uses Mixpanel, a popular analytics service, to understand how people use its API products. Think of it as a dashboard that tracks which features get used, which pages people visit, and basic technical details.
In early November 2025, attackers tricked Mixpanel employees with fake text messages. This type of attack is called “smishing”, phishing by SMS. The attackers used those messages to get into parts of Mixpanel’s systems and export a dataset that included some OpenAI API analytics.
According to OpenAI’s own incident summary, the stolen data included:
- Names of API users
- Email addresses
- Rough location, like city or country
- Browser and operating system details
- Referring websites
- Organization and user IDs
What did they not get? No passwords, no API keys, no payment data, no chat content, and no government IDs. Regular ChatGPT users were not in this dataset. Only API users were in scope.
The key point for you: OpenAI’s core systems were not breached. The damage came through a vendor that held “only analytics”.
Why this should worry CEOs even if the data sounded “low risk”
At first read, you might shrug. Names, emails, locations, device info. Boring. No credit cards, no secrets.
That is the trap.
This type of “basic” data is perfect fuel for targeted attacks:
- A fake invoice emailed to your finance lead that uses the correct vendor name, title, and region.
- A “security notice about your OpenAI API usage” sent to your engineers, complete with their real organization name.
- A follow-up SMS to your product team that looks just like the real vendor texts they get every week.
With enough names, emails, and context, attackers can sound like they already work with you. That breaks down skepticism and gets people to click, share, or pay.
For you, the risk is not only fraud. It is board questions, investor anxiety, and customer trust. A small batch of leaked metadata can turn into:
- Social engineering against your staff
- Fake messages that damage your brand
- Public stories that mix your name into “breach” headlines
As this breakdown of the OpenAI Mixpanel security incident notes, metadata leaks can be just as powerful as direct content leaks for attackers.
Lessons from the OpenAI–Mixpanel Incident for Your Own Data and Vendors
This incident is not just about OpenAI or Mixpanel. It is a case study of how most mid-market companies now operate: core systems locked down, third-party tools everywhere, and a lot of trust placed in “just analytics”.
Here is how to turn it into action.
Lesson 1: Map where your data really lives, not just where you think it lives
In most companies, data does not sit in one place. It flows through:
- CRMs
- Analytics tools
- Payment processors
- Marketing platforms
- Logging and monitoring tools
- Customer support systems
If you asked your team today, “Where does our customer email list live?”, they might list your CRM and marketing tool. In practice, it might also sit inside three analytics platforms, two sales tools, and a forgotten trial account.
Ask your team for a one-page data map. It should show, for each major data type (customer, employee, product, finance):
- Which vendors receive it
- What fields they get
- Why they get it
The OpenAI–Mixpanel incident showed that “only analytics” tools often still hold names, emails, and IDs. Treat this as a 30-day project. You do not need perfection. You need a clear enough map to talk credibly with your board and to spot surprises.
Lesson 2: Treat third-party vendors as part of your security surface
If a vendor holds your data, they are part of your attack surface, plain and simple.
You do not need a large security department to raise the bar. For your top 10 to 20 vendors that touch customer or employee data, ask for:
- Confirmation that they use multi-factor authentication for staff
- Proof of phishing and smishing training
- Basic audit logs of who accessed your data and when
- A clear contact for security incidents
Then look at contracts. For upcoming renewals, push for:
- Timely breach notification terms
- Clarity on what data they store and for how long
- A right to ask for deletion or reduction of data you send
“Everyone uses this vendor” is not a control. They must earn trust, just like your own teams.
Lesson 3: Limit what you share with vendors to the smallest useful set
If Mixpanel did not need names or emails, those fields should never have been there. The same is true across your stack.
Data minimization is simple in concept: send only what a vendor truly needs to deliver value. Some easy moves:
- Replace email addresses with random user IDs in analytics tools
- Aggregate data before you send it, for example daily counts instead of raw events
- Turn off unneeded tracking of device or referral data
Ask your teams, “If this vendor was breached tomorrow, what data do we wish they did not have?” Then work backward.
This mindset does not stop breaches. It shrinks the blast radius when a breach occurs.
Lesson 4: Train people for modern attacks like smishing and vendor-themed phishing
The Mixpanel breach started with smishing. That pattern is spreading. Attackers now blend real vendor names, recent incidents, and bits of leaked data to craft messages that feel legitimate.
Good training for a mid-market company does not need to be long or fancy. Focus on:
- Short, regular sessions, 15 to 20 minutes, tied to real stories
- A simple playbook like “stop, check, verify” for any text or email that asks for logins, codes, or urgent action
- Clear rules that staff never share MFA codes or passwords over text or chat
Use this incident as a case study in your next session. Show how an attacker might pretend to be “your analytics vendor” or “OpenAI security” with real details about tools you use.
This is not just IT’s problem. It is culture.
Lesson 5: Have a simple, written plan for when a vendor is breached
When Mixpanel reported the issue, OpenAI quickly removed them from its systems, investigated the impact, and notified affected users. That sequence is your template.
You need a light, written playbook for vendor incidents. One page is enough if it is clear. It should answer:
- Who owns the response, by role and name
- How to quickly disable data flows or integrations to the vendor
- How you will assess what data was at risk
- How and when you will inform your board, customers, and staff
- How you will decide whether to keep or replace the vendor
In a crisis, the absence of a plan costs you days. A simple plan, agreed in calm times, buys you speed and confidence when you need it most. As this broader perspective on third-party vendor risk points out, speed and clarity often matter more than the size of the breach itself.
Turning these lessons into a practical roadmap for your company
You might be thinking, “This all makes sense, but my plate is already full.” That is normal. The goal is not perfection. The goal is steady, visible progress that you can explain to your board.
A 90-day action plan to reduce third-party and analytics risk
Here is a realistic 90-day sequence that does not require a full-time CISO:
- Identify your top data-carrying vendors and tools, including analytics and marketing platforms.
- Map what data each receives, focusing on customer and employee fields.
- Cut or reduce unnecessary data flows, using masking or aggregation where possible.
- Add basic vendor security checks for that top tier and tighten contract terms on renewal.
- Run one focused training cycle on phishing and smishing, using the OpenAI–Mixpanel story as the example.
You will come out of this with fewer surprises, less wasted spend on tools you do not need, and a better story for your board about how you treat data and vendor risk.
How a fractional CTO/CISO partner can help you stay ahead of the next incident
Many mid-market leaders know this work matters, but they do not have a trusted senior technology or security leader to own it.
A strong fractional CTO or CISO partner sits on your side of the table. They help you:
- Clarify your data map and vendor list
- Structure vendor reviews so they are fast and repeatable
- Prioritize a small set of controls that reduce the most risk
- Translate tradeoffs into clear, business-focused language for your board
That is the type of outcome-focused support CTO Input provides: reduced vendor sprawl, tighter alignment of technology with growth, and clearer reporting on cyber and AI risk so you are not guessing in front of investors.
Conclusion: Your data lives wherever it is copied
Your data does not live only in your core systems. It lives wherever it is copied, tracked, or analyzed, from “harmless” analytics tools to forgotten integrations. The Lessons from the OpenAI–Mixpanel Incident are simple but sharp: treat vendors and analytics platforms as part of your security and your strategy, not as a side note.
The question is not “Are we secure?”. The better question is “Where does our data really go, and how do we limit the blast radius when something goes wrong?”.
If you want help turning those questions into a clear plan, visit CTO Input at https://www.ctoinput.com to see how fractional CTO, CIO, and CISO leadership can give you an honest roadmap for vendor and data risk. To go deeper on related topics, explore more insights on the CTO Input blog at https://blog.ctoinput.com.