Switching the team that runs your company’s IT is a little like changing the tires on a moving car. It’s possible. It’s common. It can also go sideways fast when nobody owns the plan.
If you’re switching MSPs, your real goal isn’t “a better provider.” Your goal is business continuity, clean accountability, and a handover you can defend in front of a board, lender, or customer.
This checklist is written for leaders who need the change to happen quietly: no downtime, no data loss, no messy vendor drama.
Why MSP transitions fail (and why it turns into finger-pointing)
Most failed MSP transitions share the same root cause: the handoff wasn’t treated like a controlled operational change. It was treated like vendor replacement.
That creates three predictable problems:
1) No single source of truth. Asset lists don’t match reality. Password vaults are incomplete. “We thought you had that” becomes the theme.
2) No decision rights. Who approves changes during the transition, the outgoing MSP, the incoming MSP, or your internal IT lead? If that’s unclear, every incident becomes a debate.
3) No proof. Backups exist, but nobody has recently proven restore works. Monitoring exists, but alerts route to the wrong team. The business runs on hope.
You can prevent all three by making the transition a short program with clear governance, measurable gates, and written signoffs.
The governance layer: the contract and the rules of the road
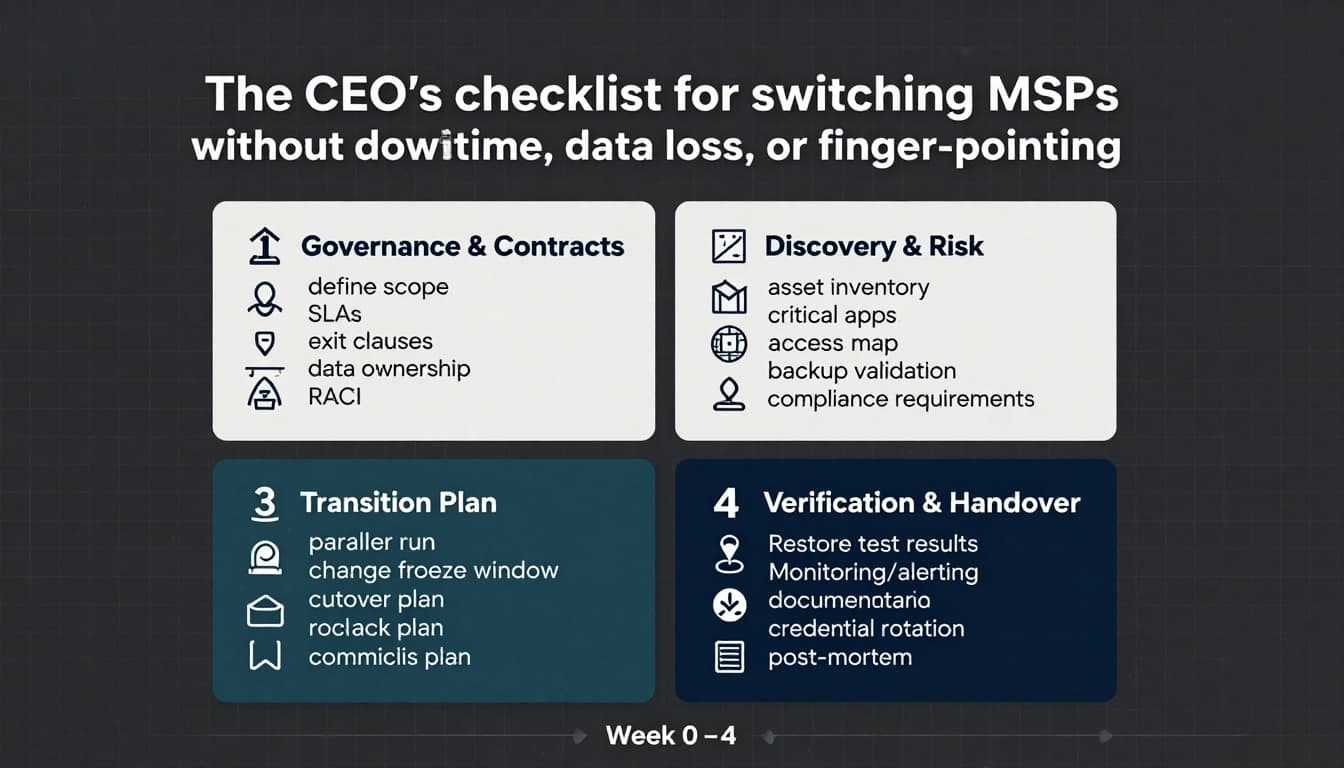
Before anyone touches a firewall rule or admin account, lock down the “how we’ll work” details. This is the part that keeps disagreements from becoming outages.
Focus on four governance items:
- Scope and service boundaries: What’s included (endpoints, M365, network, cloud, backups, security tooling), what’s not, and what counts as a project.
- Exit and transition help: Require reasonable cooperation from the outgoing MSP, including documentation handoff, exports, and a defined access transfer window.
- Data ownership and access rights: Your company owns configs, logs, documentation, and data. That sounds obvious until you need it.
- RACI, in writing: Who is Responsible, Accountable, Consulted, Informed for each area (identity, endpoints, networking, backups, security alerts, line-of-business apps).
A simple way to keep this executive-friendly is to name owners for the few decisions that tend to create chaos:
| Decision that must be explicit | Why it matters | Who should own it |
|---|---|---|
| Final cutover date and freeze window | Prevents last-minute changes that break the plan | CEO/COO (with IT lead) |
| “Stop the line” authority | Someone must be able to pause changes if risk spikes | CEO/COO delegate |
| What “done” means | Avoids an endless transition with fuzzy goals | CEO/COO + IT lead |
| Incident ownership during overlap | Stops blame loops when an alert hits at 2 a.m. | IT lead |
Governance doesn’t slow the project down. It stops rework and arguments.
Discovery and risk: inventory, access, backups, and compliance
The fastest way to create downtime during switching MSPs is to skip discovery because “we’re small” or “it’s all in Microsoft 365.” Your environment may be smaller than an enterprise, but it’s still interconnected.
At minimum, insist on four discovery outputs:
Asset inventory that’s reconciled, not guessed. Endpoints, servers, network gear, SaaS apps, cloud accounts, warranties, and who uses what.
A map of critical business flows. What must stay up for you to make money this week? ERP. POS. EDI. Customer portal. Accounting close. Not every system is equal.
An access map. Where are the admin accounts, shared mailboxes, service accounts, API keys, SSO connections, and break-glass accounts? Which ones are tied to a vendor’s email address?
Backup validation. Not “we have backups,” but “we restored a sample and it worked.” If you want a practical set of checks to compare against, Spin.AI’s overview of data backup and disaster recovery best practices is a useful reference point for what to verify.
Also capture compliance requirements early (SOC 2 expectations, HIPAA, PCI DSS, state privacy laws, contract-driven controls). If you’re not sure what applies, write down who is asking the questions: customers, auditors, banks, or your board. That’s enough to set the bar.
The transition plan: parallel run, cutover, rollback, and comms
A clean MSP change feels boring. That’s the point. It should look like a flight plan: taxi, takeoff, and a clear abort option.
Build the plan around four controls:
Parallel run (overlap) with a ticket boundary. For a short window, both MSPs may have access, but only one team should be the “hands on keyboard” for most changes. Decide which tickets go where. Put it in writing.
A change freeze window. You don’t need to freeze everything for weeks. You do need a short period where non-essential changes stop, so you can stabilize and cut over safely.
Cutover with a rollback plan. The CEO version should fit on one page: what changes, when it changes, who is watching, and exactly what triggers rollback. If your transition includes cloud moves or major re-platforming, a structured checklist like DigitalOcean’s pre- and post-migration guide can help you think in “before, during, after” controls rather than heroics.
A comms plan that respects operations. Tell employees what might change (support emails, help desk portal, MFA prompts), when it changes, and how to get help. Tell leadership what “normal” looks like during the first two weeks (response times, escalations, daily check-ins).
If you want one extra safeguard, schedule a daily 15-minute standup during the cutover week. One page of notes. Actions with owners. No speeches.
Verification and handover: prove the environment is safe to run
The end of an MSP transition is not “the new provider is live.” It’s “we can prove we’re stable, and the old provider can’t accidentally or intentionally touch anything.”
Verification should include:
Restore test results you can show. At least one real restore test for each critical data set (file shares, key SaaS, one server image if applicable). Evidence matters.
Monitoring and alert routing. Confirm alerts go to the right on-call team, not a retired distribution list. Confirm severity definitions. Confirm escalation paths.
Documentation handover that’s usable. Network diagrams, vendor lists, renewal dates, admin portals, configs, and where the weird stuff lives (custom scripts, ancient scanners, line-of-business app dependencies).
Credential rotation. Rotate admin passwords, API keys, service account secrets, backup credentials, and any shared keys. Remove old MSP accounts. Close remote access paths. This is where many “post-transition surprises” come from.
Post-mortem with decisions. What broke. What was confusing. What should be standard next time. Write it down while it’s fresh.
For a business-focused view of how to reduce disruption while changing providers, CXC Global’s piece on switching MSPs without disrupting business operations is a helpful reminder that the people side (comms and expectations) is as real as the technical side.
The CEO’s checklist for switching MSPs (a condensed version)
Use this as your executive “gates” list. If an item can’t be checked, you’re not ready to cut over.
- Named accountable owner for the transition (one person, not a group)
- Written scope and service boundaries for the new MSP
- Exit cooperation requirements confirmed with the outgoing MSP
- RACI agreed for identity, endpoints, network, backups, security alerts
- Reconciled asset inventory completed
- Critical apps list ranked by business impact
- Access map completed (admin accounts, service accounts, vendor access)
- Backup restore test evidence captured for critical data
- Parallel run plan and ticket boundary agreed
- Freeze window scheduled and communicated
- Cutover and rollback plan approved by leadership
- Credential rotation and old access removal completed after cutover
Conclusion: make the switch quiet, controlled, and defensible
If switching MSPs feels stressful, that’s rational. You’re changing the team that holds the keys to revenue, trust, and daily operations. The antidote is simple: clear ownership, written gates, and proof at each step.
When the process is tight, the result is boring in the best way. The business keeps running, your risk drops, and the story stays clean.
If you want an executive partner to pressure-test your plan and keep the transition accountable, visit https://www.ctoinput.com. For more practical guidance on cost, risk, and tech leadership in mid-market companies, explore https://blog.ctoinput.com.
