A vendor risk management assessment is the process of identifying, evaluating, and reducing the risks your third-party suppliers and partners introduce. For any organization, this is a critical discipline. But for justice-focused organizations serving vulnerable communities, it's a non-negotiable responsibility. You must ensure a vendor's security, operational, and compliance practices don't create vulnerabilities for your mission, your data, or the people you serve. This means going beyond simple checklists to actively protect incredibly sensitive information related to immigration, incarceration, or youth advocacy.
Key Takeaways:
- Start with Your Mission: Vendor risk isn't an IT problem; it's a mission continuity problem. A data breach or service outage from a key vendor can directly harm clients and erode community trust.
- Focus on the Highest Risk First: You can't assess every vendor with the same intensity. Create a simple tiering system (High, Medium, Low) based on data access and operational criticality to focus your limited resources where they matter most.
- Demand Proof, Not Promises: Move beyond simple questionnaires for high-risk vendors. Request and review evidence like SOC 2 reports, data encryption policies, and business continuity plans to verify their security claims.
- Turn Findings into Action: An assessment is useless without follow-through. Create clear, time-bound remediation plans for identified risks and formally document any risks you must accept, ensuring leadership sign-off.
- Stop the Fire Drills: The goal is a sustainable, repeatable process, not a one-time project. Establish a predictable rhythm for monitoring high-risk vendors to ensure their security posture doesn't degrade over time.
From Vendor Chaos to Strategic Control
If you're a leader in a justice organization, you know the feeling. The sudden panic when a funder's security questionnaire lands on your desk, asking for details you don't have. Or the dread that follows a critical software vendor's data breach announcement, realizing sensitive client data from an immigration case is sitting in a tool you barely vetted. This feeling of exposure is a direct result of rapid growth on top of fragile systems.

The explosion of software for case management, fundraising, and client intake has created a silent crisis. You've embraced technology to scale your mission, but now you're tethered to dozens—if not hundreds—of third parties. Every one of them represents a potential point of failure.
- Data Breaches: A breach could expose the highly sensitive information of vulnerable individuals involved in immigration, incarceration, or youth justice cases, creating real-world harm.
- Operational Failure: An outage at a key vendor could halt your intake process, disrupt referral handoffs, or prevent staff from accessing critical case files during a crisis.
- Reputational Harm: A security incident traced back to a vendor you didn't properly vet can instantly erode the trust you’ve worked so hard to build with funders, partners, and the communities you exist to support.
Shifting from IT Problem to Mission Continuity
This isn't an "IT problem." It's a mission continuity problem. The reality is that many justice organizations have grown fast, and vendor oversight simply hasn't kept pace. You might have a systems manager or a de facto "tech person," but you likely lack a trusted senior leader who can connect vendor relationships to strategic risk and your mission.
The core challenge is that you cannot delegate your responsibility to protect client data, even if you delegate the processing of that data to a vendor. The obligation to your community, funders, and regulators remains squarely with your organization.
This guide provides a calm, practical framework for a vendor risk management assessment that fits your reality. We'll move beyond compliance checklists to build a repeatable process that protects vulnerable communities, reduces staff chaos, and helps you make smarter technology decisions. The goal is to build a program your board and funders will trust as a sign of mature, responsible leadership. We’ll walk through what to do first, what to measure, and how to turn vendor management from a source of anxiety into a backbone of support for your critical work.
A Practical Framework for Vendor Risk Management
For most leaders, a vendor risk management assessment sounds like a painful, technical chore. It's better to think of it as a core governance function—one that's essential for protecting your mission, your reputation, and the communities you serve. This isn't about adding red tape; it’s about building a repeatable, common-sense process to get ahead of the chaos and prove to funders and your board that you are a responsible steward of their trust.
Before we get into the nuts and bolts, let's look at the big picture.
The Four Phases of a Practical Vendor Risk Management Lifecycle
The process can be broken down into four key stages. This table shows how a practical vendor risk management program works, moving your organization from a reactive, fire-fighting mode to a proactive, strategic one.
| Phase | Key Action | Primary Goal for Justice Orgs |
|---|---|---|
| Discovery & Tiering | Create a complete inventory of all vendors and categorize them by risk level (high, medium, low) based on data access and operational criticality. | To focus limited time and resources on the vendors that pose the greatest potential harm to clients and the mission if compromised. |
| Assessment | Conduct due diligence on high and medium-risk vendors using targeted questionnaires and evidence requests (e.g., security policies, SOC 2 reports). | To verify a vendor's security and privacy controls are strong enough to handle sensitive data related to immigration, youth, or incarceration. |
| Remediation & Acceptance | Work with vendors to fix identified security gaps or, if a risk cannot be fixed, formally document and accept the risk with leadership approval. | To create a defensible and auditable trail of due diligence, demonstrating responsible oversight to funders and your board of directors. |
| Ongoing Monitoring | Continuously monitor high-risk vendors for new threats, conduct periodic reassessments, and prepare for potential security incidents. | To ensure that a vendor's security posture doesn't degrade over time and that your organization is prepared to respond if an incident occurs. |
Following a structured lifecycle like this is what makes your process defensible. To bring it all together and manage vendor compliance more efficiently, you might eventually look into dedicated third-party risk management software. But for now, the most important thing to stop doing is treating every vendor relationship as an informal, one-off agreement. Making the switch from constant fire drills to a structured program is the first real step.
Mapping Your Vendor Universe to Find Hidden Risks
You can't manage risks you don't know you have. For most justice-focused organizations, the true number of vendors is a shock, often hiding in accounting records and program budgets. A proper vendor risk management assessment must start with a complete inventory—not just of software, but of every third party that touches your data or operations.
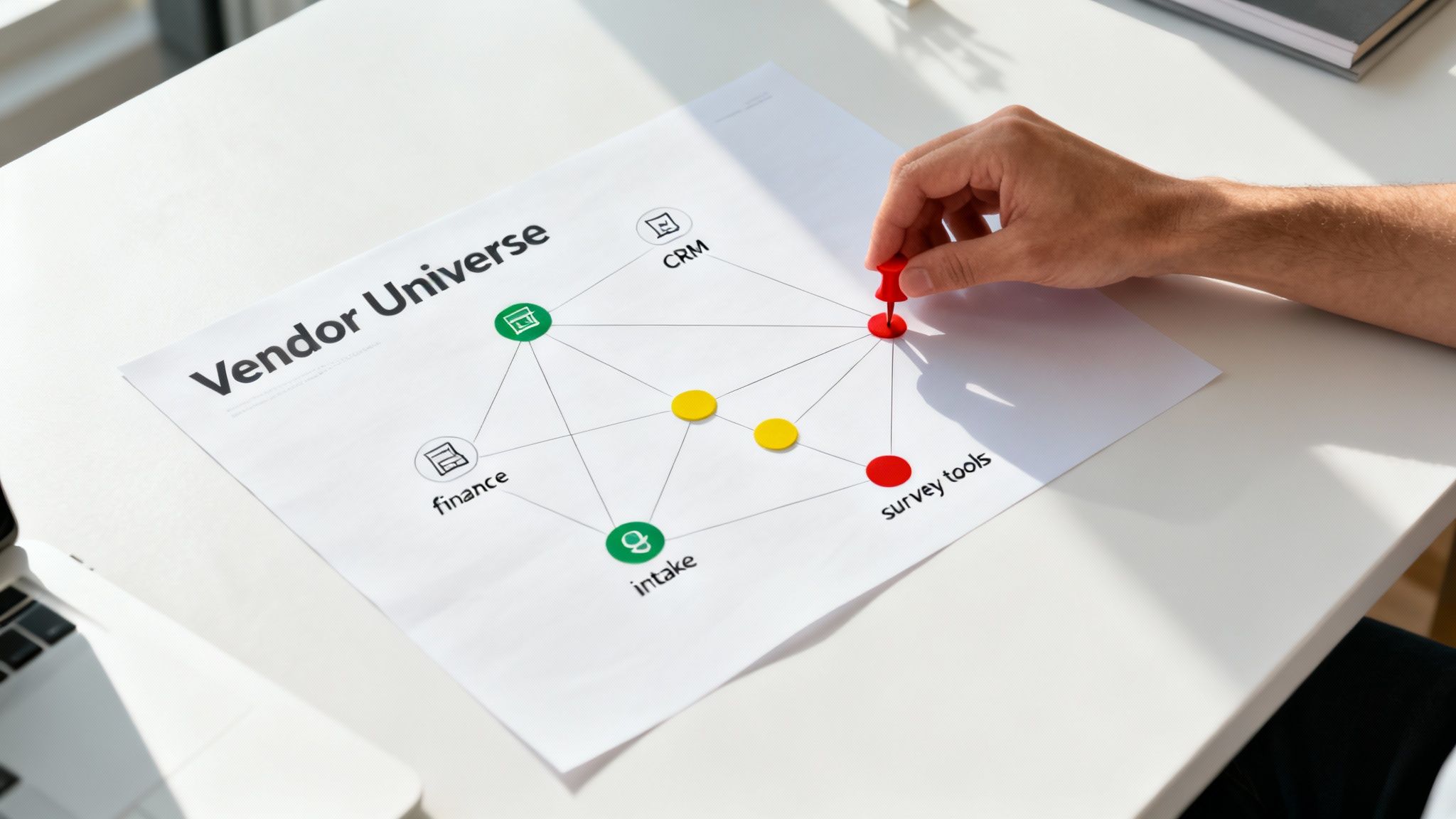
The idea is to map your entire "vendor universe." This includes your case management system, but also the tools that fly under the radar: the survey tool for community feedback, the transcription service for client interviews, the cloud storage where grant proposals live. Every single one is a potential weak point.
Start with the Money Trail
The quickest way to get a handle on this is to follow the money. Your finance team is your best first stop.
Ask for a complete dump of all vendor payments from the last 12-18 months. This financial data provides an unfiltered, objective look at who you’re actually paying. And don't just think about software. Include professional services, consultants, and any recurring payment that signals an ongoing relationship. This raw data is the factual starting point that stops the guesswork. For a great way to structure this discovery, our guide on creating a nonprofit systems inventory has a practical template you can adapt.
Enrich the Data with Human Intelligence
A list of payments only tells you part of the story. The next step is to figure out what these vendors actually do and what data they access. That means talking to your program and operations staff on the front lines.
Set up brief conversations with department heads to walk through the vendor list. Ask a few simple but critical questions:
- What is this for? What specific job does this vendor do for your team?
- What data do they touch? Do they see sensitive client info, donor details, or just operational data?
- How much do we need them? What would happen if this vendor went offline tomorrow during a critical deadline?
This is where your flat list becomes a rich map of dependencies and risks. You’ll almost certainly uncover "shadow IT"—tools that teams have adopted on their own—and get a clearer picture of your operational reality.
Tiering Your Vendors to Focus Your Efforts
Once you have a solid inventory, it’s time to prioritize. You cannot scrutinize every vendor with the same intensity. This is where tiering saves you from burnout. Tiering is a straightforward way of grouping vendors by their risk level so you can focus your limited time where it matters most. For most organizations, a simple three-tier system works perfectly.
| Vendor Tier | Description | Examples |
|---|---|---|
| Tier 1 High Risk | Mission-critical vendors handling sensitive, regulated, or personally identifiable information (PII). A breach or outage would cause severe harm. | Case management platform, cloud hosting provider (AWS/Azure), payroll processor, primary fundraising CRM. |
| Tier 2 Medium Risk | Vendors important for operations but with limited access to sensitive data. An outage would be disruptive, but not catastrophic. | Project management tools, website hosting, survey software, bulk email provider. |
| Tier 3 Low Risk | Vendors with no access to sensitive data and not critical for daily work. | Office supply company, graphic design freelancers, subscription to a news publication. |
This sorting process is crucial. It stops you from falling into the one-size-fits-all trap where you spend as much time vetting your office supply company as your case management system. By flagging your Tier 1 vendors, you know exactly where to aim your most rigorous assessment efforts, ensuring your most vulnerable data and essential operations are protected first.
Conducting Assessments That Actually Protect You
You've tiered your vendors. Now comes the real work: moving from a map to focused, practical due diligence. A generic questionnaire isn't going to cut it, especially when the stakes are this high. When you're dealing with a high-risk vendor—one handling sensitive data about immigration, incarceration, or youth—a simple checklist is dangerously insufficient. This is about demanding evidence, not just accepting answers.

The point of a vendor risk management assessment is to verify that a partner's security and privacy practices are strong enough to make them a trusted steward of your community’s data. To do that, you must methodically dig into the core areas that determine their resilience and reliability.
The Four Risk Domains You Must Evaluate
For any high-risk vendor, your assessment needs to zero in on four critical areas. Think of these as the legs of a table—if one is weak, the whole thing comes crashing down.
- Cybersecurity Posture: This is the most technical, but you don't need to be an expert. You need to understand how they defend against attacks. This includes encryption (for data on their servers and moving across the internet), access controls (who can see what, and why), and vulnerability management (how they find and fix security holes).
- Data Privacy Practices: How a vendor handles personal information is as important as how they secure it. Look for evidence of data minimization—are they only collecting what’s necessary? What are their policies for retaining and deleting data? And most importantly, how do they ensure they're complying with regulations that apply to your work?
- Operational Resilience: This is about the "what if" scenarios. What happens if their service goes down? You need to understand their business continuity and disaster recovery plans. For a justice organization, a vendor outage can mean a missed court deadline or a dropped referral handoff. The impact is real.
- Financial & Reputational Stability: Is this vendor a viable partner for the long haul? A company on shaky financial ground might cut corners on security or go out of business entirely, leaving you scrambling. A quick look into their business history can reveal red flags.
From Asking Questions to Seeing Proof
A questionnaire is a starting point, not the finish line. The real value comes from reviewing the evidence that backs up a vendor’s claims. You don't have to be a cybersecurity guru, but you do need to know what to ask for.
Statistics show that a staggering 77% of organizations hit by data breaches traced the cause to a compromised vendor. What’s more, over 25% of organizations don’t even tier their vendors by risk, even as their vendor ecosystems grow by 21% annually. For justice leaders, this is a flashing red light.
The most important mindset shift is moving from “Did you answer the question?” to “Can you show me the proof?” A vendor’s willingness to provide documentation is a direct indicator of their security maturity.
So, what should you be asking for? Here’s a quick-start guide to the key domains and the proof you should request.
Key Risk Domains for Vendor Assessment
This table breaks down the critical areas to investigate when assessing a vendor that handles your organization's sensitive data.
| Risk Domain | What to Ask | Evidence to Request |
|---|---|---|
| Cybersecurity | Do you encrypt all sensitive data, both at rest and in transit? How do you manage employee access to our data? | SOC 2 Type II report, recent penetration test results (summary), data encryption policy. |
| Data Privacy | What is your policy for data retention and deletion? How do you ensure only necessary data is collected and processed? | Privacy policy, data retention schedule, sample Data Processing Agreement (DPA). |
| Operational Resilience | What is your guaranteed uptime (SLA)? Can you share the summary of your last disaster recovery test? | Service Level Agreement (SLA), summary of Business Continuity/Disaster Recovery (BC/DR) plan. |
| Financial Stability | How long has your company been in business? Are you willing to provide professional references? | Public financial statements (if applicable), client references from similar organizations. |
Looking at these documents for the first time can be intimidating. Just start with the basics. A SOC 2 report is an independent audit of a company’s security controls. Simply confirming they have one is a huge step. For a deeper dive, this practical guide to vendor risk assessment offers step-by-step instructions. And to get a head start, our cybersecurity risk assessment template can be adapted for vendor-specific inquiries. The goal isn’t to become a certified auditor; it’s to perform enough due diligence to make an informed, defensible decision.
Turning Your Assessment Findings into Action
An assessment that just sits in a folder is a waste of time. The point of a rigorous vendor risk management assessment is to drive real change that protects your organization. Once you have the questionnaires back and have reviewed the evidence, you will inevitably have a list of gaps. Don't panic. The next step is disciplined prioritization.
Not all findings carry the same weight. A vendor missing a formal data retention policy is a problem, but it’s not the same five-alarm fire as a vendor storing client data without encryption. Your first job is to sort the truly critical issues from the important-but-not-urgent ones. This is how you avoid getting overwhelmed and focus your team's energy.
Prioritizing Risks with a Simple Framework
An effective way to prioritize is to use a simple risk matrix. Plot the likelihood of something bad happening against its potential impact on your mission.
- High-Priority Risks: These are your non-negotiables. They have a high chance of occurring and would cause severe damage—a data breach exposing sensitive client information, a major service outage, or a compliance failure. These demand immediate attention.
- Medium-Priority Risks: These are significant but less immediate. The impact might be more moderate, or the likelihood lower. Address these within a reasonable timeframe, like the next quarter.
- Low-Priority Risks: These are minor issues with minimal potential fallout. Log them and track them, but don't let them pull focus from more serious vulnerabilities.
This simple sorting exercise transforms a messy list into a clear, actionable roadmap. It also gives you a defensible reason for tackling certain issues first—incredibly helpful when explaining the plan to your leadership and board.
The Remediation Playbook
For any high-priority finding, you must engage the vendor directly to map out a remediation plan. Frame it as a partnership aimed at protecting your shared interests. Be firm and clear about your requirements without being accusatory. Document all communication, including:
- The Specific Finding: State exactly what you found. "Our assessment found that multi-factor authentication is not enforced for administrative accounts."
- The Required Action: Define what "fixed" looks like. "We require MFA to be implemented for all users with access to our data."
- A Reasonable Timeline: Propose a clear deadline. "Please provide a plan for implementation within 15 days and complete the rollout within 45 days."
How a vendor responds is incredibly telling. A mature partner will understand and work with you. A resistant one is a massive red flag about their security culture.
The Crucial Step of Formal Risk Acceptance
Sometimes a risk cannot be eliminated. You might have a critical vendor who can't meet a specific security control. When this happens, you have two choices: find another vendor or formally accept the risk. Risk acceptance isn't ignoring the problem; it’s a conscious, documented decision by leadership to move forward despite a known vulnerability.
This process is your proof of due diligence. It shows auditors, regulators, and your board that you didn't just sweep a problem under the rug. You identified it, evaluated it, and made an informed, strategic decision.
A formal risk acceptance memo should include:
- A clear description of the risk.
- The business justification for continuing with the vendor.
- Any compensating controls your team will implement to lessen the risk (e.g., "Since the vendor does not support MFA, we will restrict access to their platform to a single, secured device within our firewalled network.").
- Sign-off from the appropriate leader (e.g., COO, Executive Director).
This documentation is critical input for bigger strategic decisions. For example, understanding vendor security posture is essential when building out your own incident response capabilities. Our guide on creating a vendor incident response plan walks through how these pieces fit together.
Building a Sustainable Risk Monitoring Program
A vendor risk assessment is not a one-and-done project. Without solid monitoring, that assessment you just completed becomes obsolete quickly. Vendors change, new threats emerge, and your own needs evolve. The goal is to move from putting out fires to a proactive, predictable rhythm of oversight. This is how you keep your vendor relationships as a source of strength, not hidden weakness. One critical thing to stop doing is assuming a vendor's security posture is static.

Establishing a Cadence for Ongoing Reviews
Your monitoring effort must match the risk level. Use the same risk tiers you established earlier to create a realistic review schedule.
- Annual Reassessments for High-Risk Vendors: For your Tier 1 partners—like your case management system or cloud host—a full reassessment every 12 months is non-negotiable. This means a fresh questionnaire and updated proof, like their latest SOC 2 report.
- Biennial Check-ins for Medium-Risk Vendors: For Tier 2 vendors, a lighter check-in every 18-24 months is usually sufficient to confirm nothing major has changed.
- Event-Driven Reviews for All Tiers: This is your early warning system. Certain events should automatically trigger a review, regardless of tier, such as a public data breach at the vendor, a change in ownership, or a significant platform update.
Translating Risk for Leadership and Boards
Your executive director and board members don’t need a lecture on encryption protocols. They need to understand the big picture, fast. What's our overall exposure, and what's the plan? A simple, visual dashboard is your best friend.
Your dashboard should tell a story in under five minutes. It translates technical findings into mission-centric language, focusing on metrics that directly impact your organization's ability to operate safely and effectively.
A simple vendor risk dashboard for your leadership could track just a few key metrics:
| Metric | Why It Matters to Leadership | Sample Status |
|---|---|---|
| # of High-Risk Vendors | Shows the overall concentration of mission-critical dependency. | 12 (Stable) |
| Remediation Plan Status | Measures progress in closing critical security gaps with partners. | 3 Open / 1 Overdue |
| Overdue Reassessments | Highlights potential blind spots in your monitoring program. | 1 (Vendor X) |
| New Risks Identified | Informs leadership of emerging threats that may need attention. | 2 (New Vendor, Breach) |
Making Monitoring a Strategic Advantage
When you build this sustainable cycle, you're doing more than just reducing risk. You're changing how you approach technology partnerships. It helps you get ahead of problems, make smarter purchasing decisions, and prove to funders that you’re a responsible steward of their investment.
Our reliance on third parties is only growing. The global vendor risk management market is on track to more than double by 2030, powered by the same cloud services justice-focused organizations depend on. Yet, with 77% of recent data breaches traced back to a compromised vendor, failing to monitor them is a recipe for disaster. To dig deeper, you can explore the full market analysis from Grandview Research. A disciplined monitoring program is your best defense against becoming a statistic.
Got Questions? We've Got Answers
Even with a framework, putting a vendor risk management assessment process into action can feel daunting, especially for mission-driven organizations where every dollar and minute of staff time is precious. Let’s tackle common questions we hear from leaders in the justice sector.
"We're a Small Nonprofit on a Shoestring Budget. How Can We Possibly Do This?"
You don't need a huge budget or fancy software to get started. The key is to start small and focus on what matters most.
First, identify your top 5-10 most critical vendors. Who handles sensitive client data—like information related to immigration cases or incarceration records—or provides services you simply can't operate without? A simple spreadsheet is all you need to track them. The goal is progress, not perfection. When you can show your board and funders that you have a deliberate, risk-based plan for vendor oversight, it proves you're a responsible steward of the community's data.
"What Do We Do When Vendors Push Back on Our Security Questions?"
This happens, and it's a big red flag. Frame the conversation as a partnership. Explain that as an organization working with highly sensitive information, you have a non-negotiable duty to protect it. Any mature, security-conscious company should understand and have standard documentation, like a SOC 2 report, ready to share (usually under an NDA).
If a vendor gets defensive or refuses to provide any security assurances, you must pause. Is their service so unique that it’s worth the risk of a potential data breach that could harm the people you serve? More often than not, that resistance is a clear signal that they aren't the right partner for your sensitive work.
"How Often Do We Need to Reassess Our Vendors?"
There’s no magic number; your reassessment schedule should be based entirely on risk. A one-size-fits-all approach is a waste of time.
Here's a good rule of thumb:
- High-Risk Vendors: Plan on a deep-dive reassessment annually.
- Medium-Risk Vendors: A lighter review every 18-24 months should be sufficient.
- Low-Risk Vendors: You probably don't need to formally reassess them unless their services change significantly.
More importantly, have triggers for an immediate review. If a vendor has a public data breach, gets acquired, or makes a major change to their service, it's time to take another look right away.
Managing vendor risk is a core leadership responsibility, not just an IT checklist. If you need an experienced partner to help build a process that protects your mission and lets your team focus on their real work, CTO Input offers fractional technology and security leadership designed specifically for the justice ecosystem. Let's build a more resilient and secure future for your organization. Learn more at https://www.ctoinput.com.

