Recent high-profile breaches have exposed the growing complexity and risks organizations face with cybersecurity oversight. The stakes have never been higher: inadequate cybersecurity oversight can lead to devastating losses, regulatory penalties, and damaged trust.
This guide empowers leaders to approach cybersecurity oversight with robust, forward-thinking strategies that protect critical assets, ensure compliance, and build true business resilience.
You will discover the latest threat landscape, proven governance frameworks, risk management essentials, oversight best practices, technology trends, and clear steps for building a secure organization.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com.
Understanding the Modern Cybersecurity Threat Landscape
Modern organizations face a rapidly shifting threat environment. Cyberattacks have grown more frequent and sophisticated, challenging traditional defenses. Effective cybersecurity oversight is crucial for leaders who want to safeguard assets, comply with regulations, and maintain business continuity.
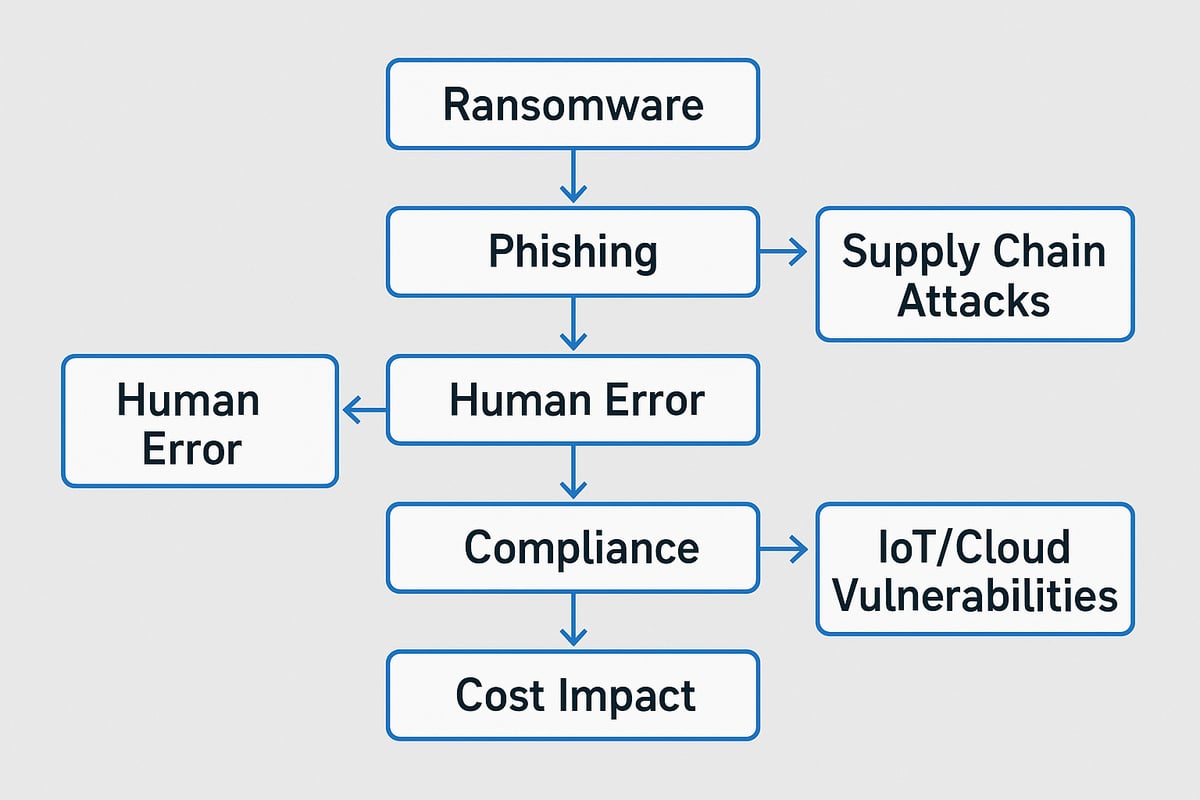
The Escalation of Cyber Threats
Cyber threats are escalating in both volume and complexity. Ransomware attacks have surged, locking down critical systems and demanding payment from victims. Phishing campaigns target employees with deceptive emails, often leading to data breaches. Supply chain attacks exploit weaknesses in trusted vendors, spreading risk across interconnected networks.
Mid-sized businesses and critical infrastructure like healthcare and municipal services have become main targets. For example, ransomware has disrupted hospital operations, putting patient safety at risk. These trends underscore the need for vigilant cybersecurity oversight at every organizational level.
The Human Factor in Cybersecurity
Human error remains a dominant risk in cybersecurity. According to industry research, 82% of breaches involve mistakes or social engineering tactics. Attackers trick users into revealing credentials or clicking malicious links.
Building a resilient defense requires ongoing security awareness programs. Training staff to recognize suspicious activity can drastically reduce incidents. Regular exercises and simulated attacks help reinforce best practices, making cybersecurity oversight more effective.
Regulatory and Compliance Drivers
The regulatory landscape is evolving quickly. New data protection laws, such as GDPR and CCPA, impose strict requirements on organizations that handle sensitive information. Failing to comply can result in significant financial penalties and damage to reputation.
Effective cybersecurity oversight ensures compliance with these regulations and reduces legal exposure. For a deeper look at how oversight and compliance intersect, see the insights in Compliance and cybersecurity essentials.
Evolving Attack Vectors
Attackers constantly search for new entry points. The growth of IoT devices, cloud computing, and remote work has expanded the attack surface. Misconfigured cloud environments can expose sensitive data to the public.
Organizations must assess these evolving risks as part of their cybersecurity oversight strategy. Regularly reviewing network architecture and monitoring for vulnerabilities is essential to stay ahead of emerging threats.
The Cost of Cyber Incidents
The financial impact of a cyber incident can be devastating. The average cost of a single data breach now exceeds millions of dollars. Expenses include downtime, legal fees, and recovery efforts.
Beyond monetary loss, organizations face erosion of customer trust. Quick, transparent responses and robust cybersecurity oversight are necessary to minimize damage and restore confidence.
The Need for Proactive Oversight
Reactive security measures are no longer sufficient. Threats evolve too quickly for organizations to wait until after an incident occurs. Continuous, proactive cybersecurity oversight is now a business imperative.
By anticipating risks and adapting strategies, leaders can reduce exposure and foster resilience. This proactive approach ensures that cybersecurity oversight aligns with organizational goals and supports long-term success.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com
Core Principles of Effective Cybersecurity Oversight
Strong cybersecurity oversight begins with a clear vision and dedicated leadership. Organizations today face complex threats, making it critical to establish foundational principles that guide every aspect of risk management and protection.
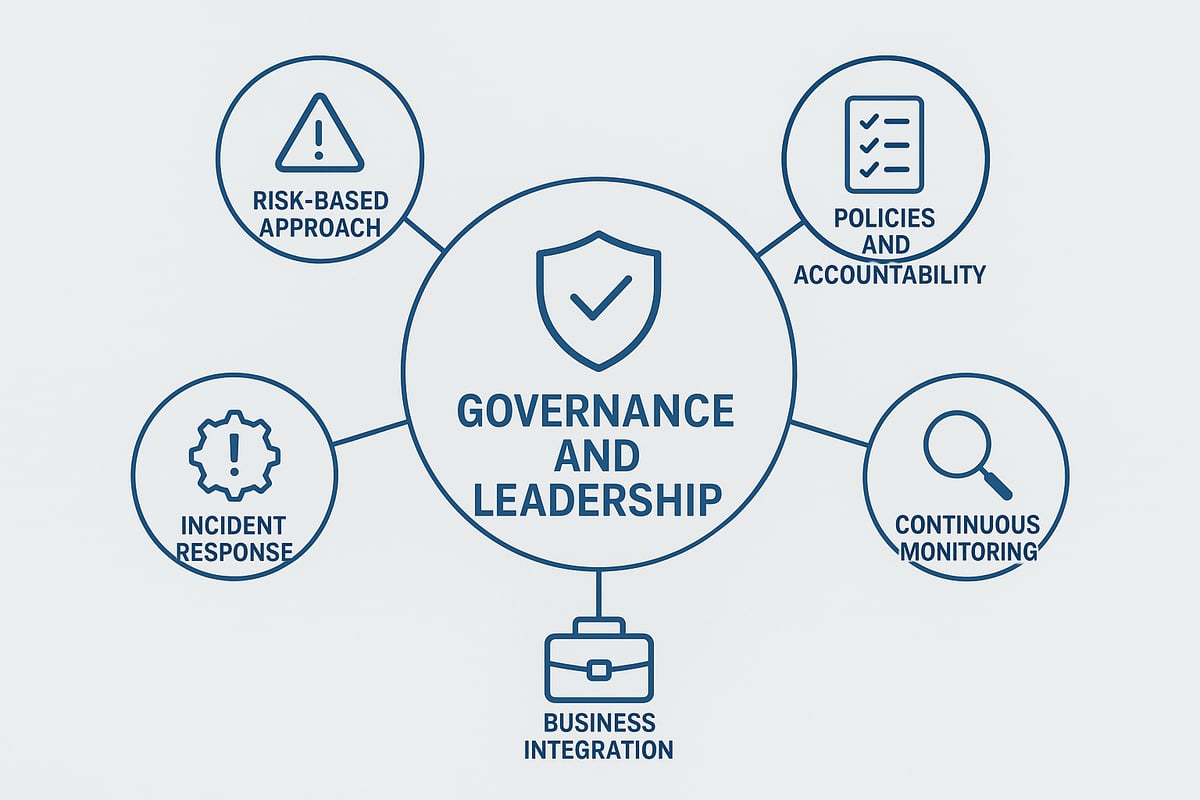
Governance and Leadership Commitment
Effective cybersecurity oversight starts at the top. Boards and executives must champion security priorities and set the tone for the entire organization.
Establishing a governance framework ensures clear decision-making and accountability. Leaders should reference best practices, such as those found in Cybersecurity Governance by CISA, to design oversight structures that match business needs. This commitment drives a culture where security is integral to daily operations.
Risk-Based Approach
A risk-based approach is central to cybersecurity oversight. Organizations must identify and prioritize risks based on their potential impact to business objectives.
Regular risk assessments guide investment decisions and help allocate resources where they are needed most. By focusing on business-critical assets, leaders ensure that cybersecurity oversight supports both protection and operational efficiency.
Clear Policies and Accountability
Documented policies form the backbone of cybersecurity oversight. These policies define roles, responsibilities, and acceptable behaviors across the organization.
- Assign specific ownership for key processes
- Outline escalation procedures for incidents
- Set clear expectations for compliance
Accountability at all levels ensures that everyone understands their part in securing the organization. This clarity strengthens the effectiveness of cybersecurity oversight.
Continuous Monitoring and Assessment
Continuous monitoring is essential for adaptive cybersecurity oversight. Regular audits, penetration tests, and vulnerability scans reveal weaknesses before they become incidents.
Utilizing threat intelligence helps organizations stay ahead of emerging risks. Ongoing assessments keep oversight aligned with the evolving threat landscape and regulatory requirements, making it possible to respond quickly to changes.
Incident Response Readiness
Incident response planning is a vital component of cybersecurity oversight. A well-documented and tested plan allows organizations to react swiftly and minimize the impact of breaches.
Learning from recent incidents and conducting regular exercises strengthens response capabilities. Proactive preparation ensures that cybersecurity oversight extends beyond prevention to include rapid recovery.
Integration with Business Strategy
Aligning cybersecurity oversight with business strategy empowers organizations to innovate securely. Security goals should support and enhance broader objectives, not hinder them.
By integrating oversight into strategic planning, leaders enable growth while managing risk. This holistic approach ensures cybersecurity oversight remains relevant and effective as the business evolves.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com
Building a Resilient Cybersecurity Oversight Framework
Creating a resilient cybersecurity oversight framework requires a structured, adaptable approach that brings together leadership, technology, and culture. The following steps guide organizations in establishing a proactive, business-aligned posture.
Step 1: Establish Oversight Structures
Begin by forming dedicated cybersecurity oversight committees or working groups. These bodies ensure that responsibilities are clear and that decision-making is informed by diverse expertise. Cross-functional collaboration is crucial, connecting IT, legal, HR, and leadership to address the full spectrum of risks. This structure enables organizations to respond quickly and align cybersecurity oversight with broader business objectives.
Step 2: Define Metrics and KPIs
Effective cybersecurity oversight depends on measurable outcomes. Identify key metrics such as incident response times, patch management rates, and completion of user training. Tracking these indicators helps highlight blind spots and guides investment decisions. For instance, reducing the mean time to detect and respond to threats is a powerful signal of oversight maturity. Regular reporting ensures everyone is accountable and progress is transparent.
Step 3: Implement Layered Security Controls
A defense-in-depth strategy is foundational for robust cybersecurity oversight. This includes integrating physical, technical, and administrative controls to reduce attack surfaces. Adopting a zero trust architecture limits lateral movement and enforces strict access controls. For forward-thinking organizations, aligning these controls with a cybersecurity strategy for 2026 ensures adaptability to emerging threats and technological shifts.
Step 4: Foster a Security-First Culture
Sustaining cybersecurity oversight requires a culture where security is everyone’s responsibility. Launch ongoing awareness campaigns and ensure executive buy-in is visible. Recognize and reward secure behavior to reinforce positive habits. When employees at all levels understand their role in protecting assets, the organization becomes more resilient to both internal and external threats.
Step 5: Regular Review and Continuous Improvement
Continuous improvement is at the heart of effective cybersecurity oversight. Conduct regular reviews, leveraging feedback from audits and incident reports to refine policies and controls. Adapt your framework to address new threats and technologies, ensuring oversight remains aligned with evolving business needs. Lessons learned must inform future strategies for true resilience.
CTO Input: Strategic Oversight Partnership
Partnering with CTO Input provides organizations with fractional executive leadership to align cybersecurity oversight with business strategy. Real-world examples show how proactive, strategic oversight can transform risk management and drive measurable results. Benefits include improved cost efficiency, clearer governance, and reduced risk exposure. To explore tailored guidance and executive partnership, connect with CTO Input for a confidential conversation.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com
Advanced Oversight Strategies and Emerging Technologies
Staying ahead of threats requires modern organizations to embrace advanced technologies and innovative strategies for cybersecurity oversight. As attack methods grow more sophisticated, leaders must integrate automation, AI, and robust frameworks to ensure protection and resilience.
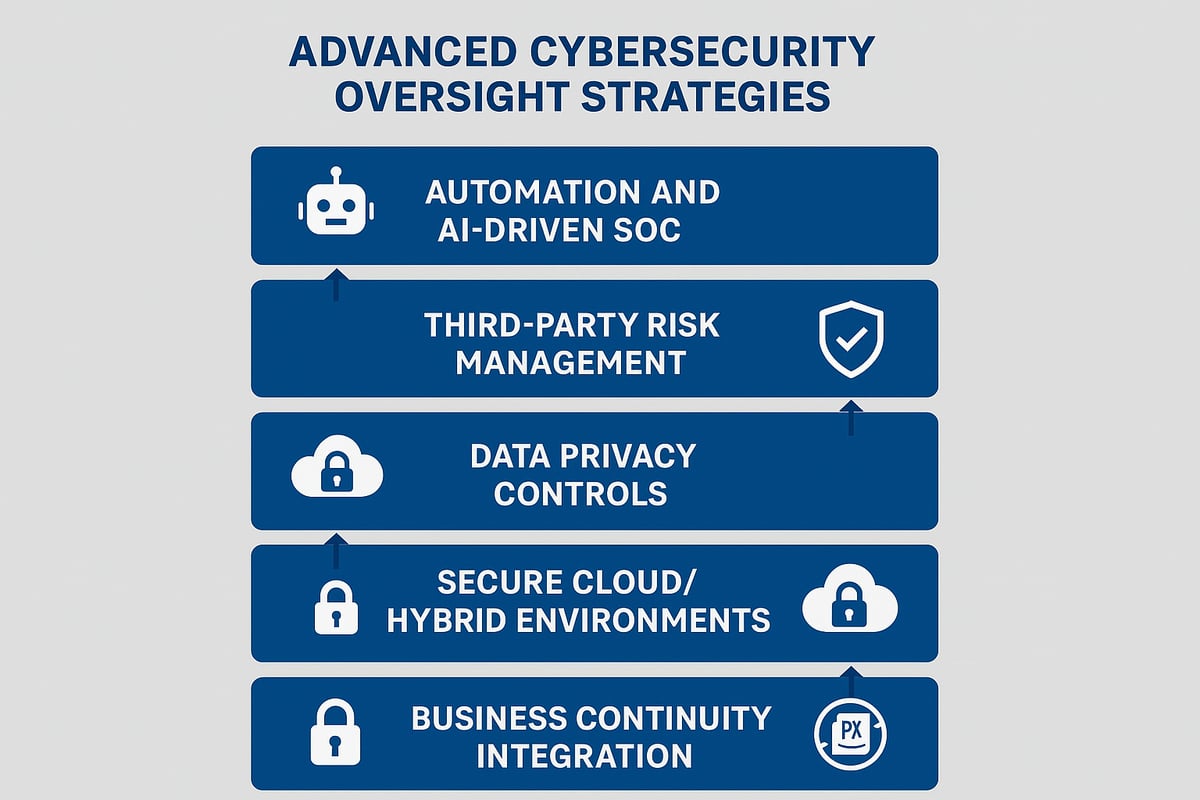
Automation and AI in Oversight
Automation and AI are transforming cybersecurity oversight by enabling rapid threat detection and streamlined response. Security operations centers (SOCs) now leverage AI-driven analytics to identify anomalies, prioritize incidents, and automate repetitive tasks.
- AI reduces response times
- Automation enhances compliance monitoring
- Machine learning improves threat hunting
These capabilities ensure oversight adapts to evolving risks, empowering teams to focus on strategic security objectives.
Third-Party and Supply Chain Risk Management
Third-party vendors introduce significant risks, making continuous oversight essential. Organizations should vet suppliers rigorously and monitor for vulnerabilities throughout the supply chain lifecycle.
Recent reports, such as the 2025 OPSWAT Threat Landscape Report, highlight a surge in multi-stage malware attacks targeting third-party providers. Proactive cybersecurity oversight in these relationships helps prevent cascading breaches and protects core assets.
Data Privacy and Protection Enhancements
Effective cybersecurity oversight demands robust data privacy measures. Advanced encryption, tokenization, and data loss prevention tools safeguard sensitive information against theft and accidental exposure.
Compliance with evolving privacy regulations is vital. Regular audits and policy reviews ensure that data handling practices align with legal requirements and industry standards, reducing the risk of costly penalties and reputational damage.
Secure Cloud and Hybrid Environments
Oversight of cloud and hybrid environments requires specialized controls. Security teams must continuously assess cloud configurations, enforce strict access management, and deploy cloud security posture management (CSPM) tools.
Insights from the 2025 ENISA Threat Landscape Report underscore the importance of addressing misconfigurations and shared responsibility models. Strong cybersecurity oversight in these domains mitigates the risk of data leaks and unauthorized access.
Identity and Access Management (IAM) Evolution
Modern IAM strategies are central to cybersecurity oversight. Zero trust access models, multi-factor authentication, and privileged access management restrict unauthorized entry and limit lateral movement within networks.
Regular monitoring and auditing of user activities further strengthen security. These measures help organizations maintain visibility and accountability, ensuring only the right individuals access critical resources.
Integration of Oversight with Business Continuity
Integrating cybersecurity oversight into business continuity planning is essential for resilience. Disaster recovery strategies must include robust incident response protocols that enable rapid recovery from ransomware or other disruptions.
Frequent testing and cross-functional exercises ensure that plans remain effective. This holistic approach minimizes downtime, protects reputation, and supports long-term organizational stability.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com
Practical Steps for Leaders to Enhance Cybersecurity Oversight
Taking decisive action on cybersecurity oversight is essential for leaders aiming to protect their organizations from evolving threats. By following these practical steps, you can elevate your oversight maturity, align security with business goals, and foster a culture of resilience.
Assess Current Oversight Maturity
Begin by evaluating your current cybersecurity oversight maturity. Use frameworks like NIST or ISO 27001 to conduct gap analyses and benchmark against industry standards. Identify where your policies, controls, and processes are strong and where vulnerabilities exist. This structured approach ensures you understand your organization’s strengths and weaknesses. Regular self-assessment is the foundation for continuous improvement in cybersecurity oversight.
Set Oversight Priorities and Roadmap
With a clear understanding of your baseline, define oversight priorities that directly address your highest risks. Develop a roadmap outlining short-term wins and long-term objectives. Align budgets and resources to these priorities, ensuring leadership buy-in. For more on aligning board-level strategy, see Cyber risk clarity for boards. A well-structured roadmap drives focused, measurable progress in cybersecurity oversight.
Invest in Talent and Training
Effective cybersecurity oversight depends on skilled teams and informed leadership. Upskill internal staff through regular training and certifications. Engage external experts for specialized roles or executive guidance when needed. Board and executive cyber education is vital for strategic alignment. By prioritizing development, you foster a knowledgeable workforce, improve incident response, and enhance your overall cybersecurity oversight capabilities.
Foster Transparent Reporting and Communication
Transparency is essential for strong cybersecurity oversight. Establish clear reporting lines to leadership and boards. Use dashboards and real-time metrics to communicate risk, incidents, and progress. Regular updates build trust and support informed decision-making. For best practices, review Board reporting on cybersecurity. Open communication ensures everyone understands their role in managing cyber risk.
Collaborate Across the Organization
Break down silos between IT, risk, compliance, and business units to strengthen cybersecurity oversight. Foster cross-functional collaboration through joint incident response drills and shared objectives. Regular meetings and joint planning sessions ensure alignment and rapid response to emerging threats. This team approach improves resilience and supports a unified security posture.
Leverage External Partnerships
Engage with cybersecurity advisors, managed service providers, and peer networks to stay ahead of threats. External partners offer fresh perspectives, threat intelligence, and best practices. Participate in industry forums and information-sharing groups to enhance your cybersecurity oversight. By leveraging outside expertise, you gain access to advanced tools and collective knowledge, strengthening your organization’s security posture.
To learn more about transforming your organization’s cybersecurity oversight and to connect with a member of the CTO Input team, visit https://www.ctoinput.com.
Spend a few minutes exploring additional articles and insights on the CTO Input blog at https://blog.ctoinput.com
As you’ve seen, effective cybersecurity oversight is all about aligning strategy, people, and technology to protect your business and set the stage for growth. If you’re ready to take the next step and want guidance tailored to your organization’s specific needs, let’s connect. Our team at CTO Input specializes in helping leaders like you move from reactive fixes to a proactive, strategic approach that reduces risk and builds confidence. Curious how we can help you turn cybersecurity into a true business advantage Schedule A Strategy Call today and let’s get started on building a safer, stronger future together.

