It’s 10 PM on a Thursday. A critical grant report is due, and you're stuck manually stitching together client data from three different spreadsheets, none of which quite match up. If that scenario feels painfully familiar, you're not just dealing with a technology headache; you're living with the consequences of a governance gap.
For the national networks, law school clinics, and capacity-building nonprofits that arm frontline legal advocates, this kind of operational chaos is the quiet tax on your mission. Information governance is the disciplined framework for how you collect, manage, and protect your data to drive better justice outcomes. Done right, it turns your information from a source of constant stress into a reliable asset, protecting vulnerable communities and giving funders and boards clear evidence of your impact.
Key Takeaways
- Start with Your Scoreboard: Good governance isn't an IT project; it's a leadership discipline focused on solving mission-critical problems like reporting fire drills, security risks, and staff burnout.
- Target a Chokepoint First: Don't try to boil the ocean. Focus on a tangible pain point like client intake, referral handoffs, or grant reporting to demonstrate immediate value.
- Stop Doing What's Broken: The most powerful governance move is to formally retire a harmful workaround, like a sprawling spreadsheet or insecure email chain, and replace it with a clear, reliable process.
- Build a Practical 90-Day Plan: Achieve quick wins by mapping one critical data workflow, deploying multi-factor authentication, defining 3-5 core metrics, and drafting a simple data classification policy.
- Focus on People, Not Platforms: The goal is to reduce confusion and wasted effort for your staff so they can better support advocates. A tool is only useful if it supports a well-defined, people-centered workflow.
The Real Cost of Information Chaos
The late-night scramble for a grant report is more than just an annoyance. It’s a symptom of a deeper operational fragility. For the organizations that support frontline advocates, this recurring chaos grinds your most important work to a halt.

The Hidden Price of Disorder
The obvious costs are easy to spot: hours of staff time burned on manual workarounds and blown deadlines. But the hidden costs are what truly undermine your mission. When your team is constantly wrestling with data, they have less time and energy to support advocates. Funder trust erodes when your numbers feel shaky.
Worse yet, the security risks tied to scattered, sensitive data—think immigration statuses or confidential case notes involving youth—become a constant, looming threat.
This struggle is incredibly common. A recent OECD report found that fragmented governance stalls digital progress. Their research showed that a staggering 60-70% of justice data is stuck in silos, making it useless for creating people-centered outcomes. The systems were built to track agency metrics, not the real journey of a person navigating the legal system. You can learn more about these insights on justice data from the OECD.
Information governance isn't a bureaucratic hurdle. It’s the essential foundation for stability and scale. It’s about creating a calm, reliable backbone for your operations so your team can focus on their real jobs.
This guide treats information governance for justice organizations as a practical field memo. The goal is to map out a simple, believable modernization path that you can defend to your board, funders, and the communities you serve.
It’s about making deliberate choices that deliver:
- Less chaos for your staff by eliminating soul-crushing manual tasks.
- Safer handling of sensitive information with clear, easy-to-follow rules.
- Clearer evidence of your impact with data you can finally trust.
- More capacity for frontline partners who rely on your support.
This isn't about another platform pitch. As we've seen before, tool sprawl is a governance problem at its core. It’s about building the data discipline, privacy-by-design, and change capacity to reliably support the advocates who stand with vulnerable people.
Your Roadmap from Chaos to Clarity: A Practical Three-Phase Plan
The term "information governance" can sound like a daunting, expensive undertaking. But it doesn't have to be. This is not about buying a magic piece of software; it's about making smart, disciplined choices that reduce risk and empower your mission.
Think of this as a practical roadmap, breaking a complex challenge into a series of clear, manageable phases. It’s designed for leaders who need to deliver quick, practical wins that reduce risk in the first few months, followed by a one- to two-year path that turns your systems into a source of strength.
Here are the key milestones on our path to building a solid information governance strategy for your justice organization:
Phase 1: The Foundation (Your First 90 Days)
This is about triage and stability. The goal is to get a handle on what you have, where your biggest risks are, and score immediate wins. We will map a critical data flow, implement foundational security controls like MFA, and designate a "single source of truth" for your most important metrics. This stops the bleeding.
Phase 2: Building Reliable Systems (The 1-Year Plan)
With the chaos contained, we build the systems that make good governance a habit. This is where we define role-based access controls to lock down sensitive data, establish a practical data retention schedule to reduce your risk profile, and formalize a simple vendor vetting process. This creates consistency.
Phase 3: Achieving Strategic Impact (The 2-Year Vision)
With a solid foundation in place, your systems become a strategic asset. This phase focuses on scaling impact through secure data-sharing agreements for coalition work, establishing routine audit processes that build funder confidence, and defining clear KPIs to prove your effectiveness. This enables growth.
This roadmap is a field guide, not a theoretical paper. Every step is designed to produce measurable outcomes that reduce staff burnout, secure sensitive information, and ultimately, free up more time and resources for the people you serve.
Laying the Governance Foundation in Your First 90 Days
Let's be realistic—your team is already stretched thin. A smart information governance plan for your justice organization isn’t about boiling the ocean. It’s about stopping the bleeding, scoring practical wins, and building momentum you can feel. The first 90 days are about triage and stability, focusing on high-impact actions that reduce immediate risk and free up staff time.
Instead of chasing a perfect system, we'll start by getting an honest look at the system you actually have. This means mapping how work really moves through your organization—from the first client intake call to the final numbers you pull for a grant report. The chaos you feel is usually rooted in undocumented, inconsistent, or broken workflows.

Launch a Data Discovery Sprint
The first concrete step is a quick "data discovery" sprint. This isn't a deep technical audit. It’s a series of guided conversations with your team to answer a few crucial questions about one high-risk workflow (e.g., handling immigration data):
- Where does our most sensitive information live? Is it in your case management system? Or is it scattered across a shared server, email inboxes, and a dozen spreadsheets?
- Who has access to it? Map out not just who should have access, but who actually does. The results are often eye-opening.
- How does this data move? Follow a single client file's journey. How many times is it copied, downloaded, or emailed? Every handoff is a potential point of failure.
This process shines a light on your biggest vulnerabilities without getting bogged down in tech. The goal is a simple, visual map of your data reality.
Establish a Single Source of Truth
I've seen countless hours wasted arguing about which spreadsheet has the correct numbers. This discrepancy doesn't just waste time; it erodes funder trust and makes sound decision-making impossible.
Within 90 days, your mission is to identify three to five critical metrics—the numbers you absolutely need for grant reports and board updates. Then, designate one system as the definitive "single source of truth" for those numbers. Period. This simple act of designation ends the recurring fire drills.
This isn't about getting every data point perfect overnight. It's about declaring which data matters most and building a repeatable process for generating it. That clarity alone is a massive win.
Implement Foundational Security Controls
While mapping your data, you can simultaneously roll out foundational security controls that provide immediate risk reduction. Think of them as basic digital hygiene.
Here’s where to focus:
- Multi-Factor Authentication (MFA): Make MFA mandatory on all critical systems, especially email. This is one of the single most effective security measures you can take.
- A Simple Data Classification Policy: Create a one-page document defining data in three tiers—Public, Internal, and Confidential/Sensitive. This helps staff understand what information needs extra care.
- Reviewing User Access: Using what you learned in your data discovery, do a quick audit of who has access to what. Remove access for former employees and adjust permissions for current staff to match their roles.
As you build this foundation, understanding and implementing essential Document Management Best Practices becomes critical, especially for the unique types of records justice organizations handle.
Your 90-Day Quick Win Checklist
To make this tangible, here is a checklist of actions that deliver immediate value. These are steps you can confidently present to your board as a low-cost investment in stability. For a deeper dive, our article on creating a data retention policy for legal aid client records is a great next step.
| Action Item | Why It Matters | What Success Looks Like |
|---|---|---|
| Map One Critical Workflow | It gets you beyond assumptions to see the real sources of friction and risk. | A one-page flowchart showing how client data moves from intake to case closure, with bottlenecks circled. |
| Deploy MFA Everywhere | It immediately shuts down the risk of unauthorized access from stolen passwords. | 100% of staff are using MFA for email and core systems within 60 days. |
| Define 5 Core Metrics | It ends the "battle of the spreadsheets" and creates a single, trusted data source. | The board and program leads agree on the five metrics and exactly where the official numbers will live. |
| Draft a Simple Data Policy | It gives staff clear, simple rules for handling sensitive info, reducing mistakes. | A one-page policy is shared with all staff, defining what is considered confidential data. |
By focusing on these high-impact tasks, you're not just improving governance; you're building a more resilient and effective organization.
Building Reliable Systems and Processes
The immediate chaos is under control. You've moved from triage to stability. Now it's time to build the durable systems that will support your mission for the long haul. This phase is about creating reliable workflows and clear rules so the chaos doesn't creep back in. This is where a thoughtful information governance for justice organizations plan starts to pay for itself, turning your systems from a source of stress into a source of strength.
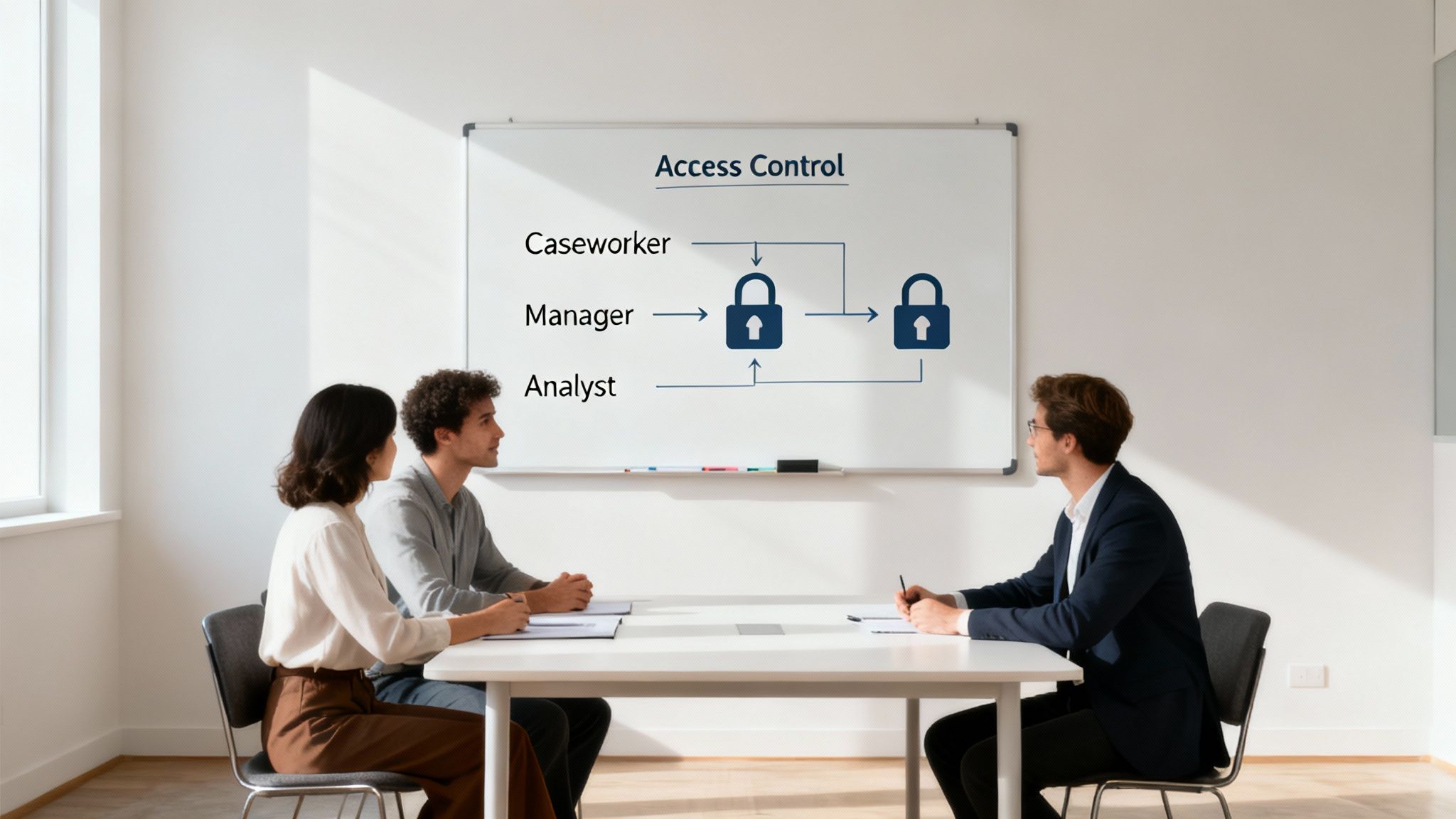
Defining Who Sees What with Role-Based Access
One of the biggest risks for any justice organization is sensitive data ending up in the wrong hands. Your most powerful tool against this is the principle of "least privilege." It simply means people should only have access to the specific information they need to do their jobs. Nothing more.
This is about creating access based on roles, not individuals:
- Intake Specialist: Needs to create new client records but should not be able to browse historical case notes from other programs.
- Program Manager: Can see aggregated reports for their team but has no business looking at financial records.
- Finance Team: Needs to see grant budgets but should be firewalled from confidential client case files.
This isn't about distrusting your team; it's about building structural safeguards. If your organization handles data related to immigration, incarceration, or youth services, this control is non-negotiable. It protects your clients, your staff, and your reputation.
Creating a Practical Data Retention Schedule
Hoarding data is a massive, hidden liability. Every old client file and archived email you keep beyond its useful life increases your risk profile in a breach.
A data retention schedule is a simple policy that answers two questions:
- What information are we legally or contractually required to keep, and for how long?
- What information can—and should—we securely get rid of?
Start by mapping your obligations. Grant agreements and state laws will set minimum retention periods. Once you've met those minimums, the default action should be secure deletion. Getting rid of data you don't need is one of the cheapest and most effective risk-reduction strategies available.
A data retention schedule is what we stop doing. We stop keeping everything forever 'just in case.' This intentional act of disposal is a core discipline of mature information governance.
Establishing Simple Vendor Governance
Your data is only as secure as the weakest link in your technology chain, and that is often a third-party vendor. Before you sign another software contract, you need a simple, repeatable process for vetting that tool and its provider.
Your vendor governance checklist only needs to answer a few key questions:
- Does the vendor meet basic security standards (like encryption and MFA)?
- Who owns the data once it's in their system?
- What's their process for notifying you of a data breach?
- How do you get your data back if you leave their platform?
This process prevents the spread of "shadow IT"—the unsanctioned tools staff use on their own—and ensures any new technology aligns with your security and privacy commitments.
Forming a Lean Data Governance Committee
Rules are useless without accountability. A "data governance committee" sounds formal, but it can be a small, cross-functional team that meets quarterly to make decisions. This team isn't the "data police"; they are stewards of your information.
A good committee includes:
- A program leader who understands the frontline work.
- Someone from finance or operations who manages reporting.
- Your de-facto "tech person" or systems manager.
Their mandate is to review data policies, resolve ownership disputes, and ensure the rules are being followed. This small group provides the clarity needed to keep your governance efforts on track.
The impact of these structured processes isn't just theoretical. A landmark study by the World Justice Project found that poor information governance is a primary barrier to justice, with an estimated 1.4 billion people globally unable to meet their legal needs due to things like inadequate data access. When governance frameworks were piloted, however, they showed a direct correlation with improved case resolution rates. You can read the full findings on global access to justice. This proves that building reliable systems isn't just an internal efficiency project; it’s a direct contributor to your mission's success.
Scaling Your Impact and Ensuring Compliance
Once you have solid systems in place, your information governance program transforms from a defensive measure into a strategic asset. For networks and coalitions, this is when you can multiply your collective impact. Instead of each organization managing its own data silo, you can establish clear, secure standards that allow everyone to share information safely. This moves you beyond anecdotes to hard, compelling evidence of your shared work.

With a long-term vision, your systems stop being a source of stress and become the backbone for growth, compliance, and deeper mission fulfillment.
Crafting Secure Data-Sharing Agreements
For any network, the ability to share data is a massive force multiplier. It helps spot trends, coordinate responses, and build a compelling case for funders. But without proper governance, it’s also a huge risk.
A secure data-sharing agreement is the essential legal and operational framework for this collaboration. A strong agreement clearly defines:
- The "Why": What specific questions will this shared data answer? Keep the purpose mission-driven and tightly defined.
- The "What": Which specific, anonymized data points will be shared? Only include the absolute minimum necessary.
- The "How": What are the non-negotiable technical requirements for participation (e.g., encryption standards, access controls)?
- The "Who": How can the aggregated data be used, and who is authorized to see it? This section must be ironclad.
This isn’t just legal boilerplate. It’s about building a system of trust that protects every organization and the communities you serve.
Adopting Interoperability Standards to Speak the Same Language
To make data sharing practical, your data needs a common language. That’s what interoperability standards provide. Instead of forcing everyone onto a single platform, you can use established models to help different systems talk to each other.
A real-world example is the National Information Exchange Model (NIEM). It provides a standardized vocabulary for justice data, allowing different agencies to exchange information seamlessly. Its success shows that governance is what unlocks progress. Since its adoption in 2005, NIEM has facilitated over 1.5 billion transactions across federal and state systems.
Adopting a similar standard within your network can turn a chaotic data landscape into an ordered one, making large-scale analysis powerful.
Moving From Fire Drills to Routine Audits
Remember those panicked reporting sessions? With mature governance, they become a thing of the past. Funder reporting should be a routine, data-driven activity, not a recurring crisis. This is the stage where you establish regular, predictable audit and compliance processes.
The goal of an audit isn't to catch people making mistakes. It's to validate that your systems are working as designed. A good audit process builds confidence, both internally and with your funders.
This could look like:
- Quarterly Access Reviews: A simple check to ensure user permissions align with current job roles.
- Annual Policy Reviews: A quick look at your data policies to see if they need updates.
- Automated Reporting: Setting up dashboards that pull your key metrics automatically, so the numbers are always ready.
As you scale, robust information security is non-negotiable. For a deep dive, this ultimate guide to cyber security is an excellent resource.
Measuring What Actually Matters
How do you know if this work is paying off? You need Key Performance Indicators (KPIs) that connect directly to the problems you set out to solve. Don’t get lost in technical jargon. Measure the impact on your people and your mission.
| KPI | What It Measures | Why It Matters |
|---|---|---|
| Reduction in Reporting Time | Hours your staff spends preparing grant and board reports | Frees up valuable staff time for direct mission work. |
| Decrease in Security Incidents | Number of reported access violations or data mishaps | Proves your security controls are effective and reducing risk. |
| Improved Data Quality Score | Percentage of records that are complete and accurate | Shows your data is becoming more trustworthy and reliable. |
| Time to Fulfill a Data Request | How long it takes to pull a specific dataset for a partner | Demonstrates increased system efficiency and responsiveness. |
These metrics provide concrete evidence to your board and funders that your investment in information governance for justice organizations is delivering real, measurable returns. For more guidance, our article on information security compliance can provide additional context.
The Most Important Next Step: What Will You Stop Doing?
A roadmap is just a piece of paper until you commit to the journey. The most critical part of any real information governance plan isn’t about what you start doing. It’s about what you finally have the courage to stop doing.
Genuine change isn’t about piling new policies on top of old habits. It’s about actively dismantling the chaotic, makeshift processes that burn out your staff and put your organization at risk.
Target One Broken Workflow
Think about the daily workarounds your team accepts as normal. Is it that color-coded "master" spreadsheet that everyone despises but no one truly owns? Or the insecure email chain used to pass around sensitive client information? For many, it's the monthly fire drill to pull numbers from three different systems for a single board report.
Pick one of those recurring headaches.
Your mission for the next 30 days is to formally retire that single workaround. This isn't a tech project; it's a leadership decision. You’re changing how work gets done, sending a powerful message that you’re serious about easing your team's burden.
The fastest way to build momentum is to solve a problem everyone can see. Killing off a single, painful workaround delivers an immediate, visible win that makes the case for broader change more effectively than any slide deck ever could.
Lead the Change, Explain the Why
Once you've zeroed in on your target, lead the transition. Communicate clearly and honestly with everyone involved. Frame this not as taking something away, but as an investment in sanity and focus.
- For your staff: "We are getting rid of this process because it wastes your time and creates unnecessary risk. Here is the simpler, more secure way we'll be working from now on."
- For your board: "We are closing a key operational vulnerability. This action directly reduces our risk profile and is the first concrete step in our plan to build more resilient systems."
The final action is to schedule a single, 60-minute diagnostic session with your team. The only goal is to map out the broken workflow you've chosen and agree on its replacement.
So, the honest question you must answer is this: What source of chaos are you finally willing to shut down?
Common Questions and Straight Answers
Even with a solid plan, leaders in the justice space have practical questions about getting started. Let's tackle some of the most common ones.
Is This Going to Be Too Expensive for Our Nonprofit?
Not at all. The secret is to start small and focus on your biggest risks first. Information governance isn’t about buying some massive, expensive software suite right out of the gate.
It actually starts with simple, practical steps: creating a basic data inventory, turning on multi-factor authentication (which is often free with the tools you already use), and agreeing on a few key metrics for your reports.
Think about it this way: the cost of a data breach, losing a grant because of shaky numbers, or your team burning out from wrestling with chaotic systems is always going to be higher than the focused effort it takes to get organized. This entire roadmap is built for organizations with real-world budget constraints, zeroing in on quick wins that build momentum without needing a huge upfront check.
How Can We Do This Without Overwhelming Our Team?
This is probably the most important question, and my answer is always the same: good governance should reduce work, not create more of it. The whole point is to get rid of the 'shadow work'—the endless manual data entry, the last-minute scramble to pull reports, and the constant digital firefighting that drains your team's energy.
Yes, the initial setup takes focused effort. But it's an investment that pays you back in freed-up staff time, often within just a few months. The best way to get started is to ask your team where the biggest headaches are. They know exactly which processes are broken.
When you start by fixing their most frustrating bottlenecks, you get immediate buy-in and prove that this isn't just another top-down initiative. It's about making their work more meaningful and less frustrating.
Information governance truly clicks for justice organizations when it's seen as the solution to staff burnout. By removing the friction from their daily tasks, you give your best people the space to focus on the mission they're so passionate about.
How Does This Actually Protect Our Sensitive Client Data?
If your organization handles information on immigration cases, incarcerated individuals, or vulnerable youth, then governance isn't just a best practice—it's a core ethical duty. It gives you the concrete, enforceable rules you need to protect real people.
Specifically, this means putting things in place like:
- Airtight access controls so only authorized staff can ever view sensitive files.
- Data minimization policies that require you to securely delete data you no longer have a legal reason to keep.
- A clear vendor security checklist to make sure any tool that touches client information is properly vetted.
Without a formal governance plan, you're essentially relying on individual habits and good intentions to protect your data. That's a huge, unnecessary risk. A structured approach turns that gamble into a reliable, documented, and defensible system for safeguarding the communities you serve.
At CTO Input, we help justice organizations trade chaotic systems for a calm, reliable digital backbone that powers their mission. If you’re ready to build a realistic modernization plan that cuts risk and empowers your team, let's talk. Find out how we can help at https://www.ctoinput.com.