As cyber threats grow more advanced and relentless, organizations urgently seek trusted guidance to protect their most valuable assets. The role of the cybersecurity advisor has never been more critical or in demand.
This comprehensive guide is designed to empower both aspiring and experienced professionals. You will discover essential skills, certifications, and career steps to thrive as a cybersecurity advisor—plus practical strategies to stand out in a rapidly changing field.
Ready to take control of your future in cybersecurity? Dive in, and chart your path to professional success. Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team. Spend a few minutes exploring more articles on the CTO Input blog at https://blog.ctoinput.com.
Understanding the Cybersecurity Advisor Role
The cybersecurity advisor is a pivotal figure in protecting organizations from digital threats. This role blends technical expertise, strategic vision, and leadership to build resilient security postures and guide teams through a rapidly changing landscape.
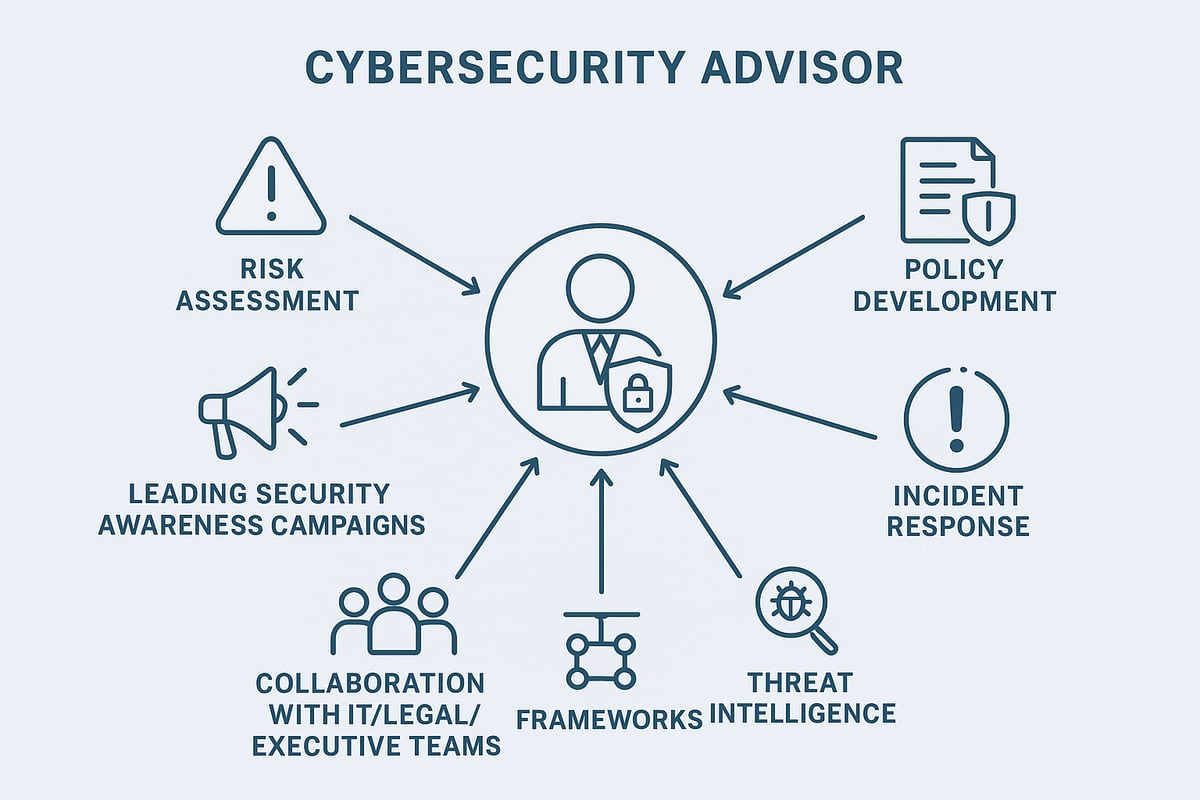
Key Responsibilities and Expectations
A cybersecurity advisor’s core duties span risk assessment, policy development, and incident response. Advisors routinely evaluate threats, create action plans, and drive the implementation of security controls that fit both business needs and compliance requirements.
Typical daily tasks include:
- Conducting risk and vulnerability assessments
- Developing and updating security policies
- Coordinating incident response and recovery efforts
- Monitoring threat intelligence sources for emerging risks
- Leading security awareness training campaigns
Advisors also play a vital role in shaping a strong security culture. They work closely with IT, legal, and executive teams to align security with business goals. For a detailed breakdown of responsibilities and career growth, see the Cybersecurity Advisor Responsibilities and Career Path guide.
A real-world example is when advisors lead company-wide security awareness campaigns, empowering employees to recognize and report phishing attempts. This proactive approach helps reduce human risk factors and fosters a culture of shared responsibility.
Required Technical and Soft Skills
A successful cybersecurity advisor possesses deep technical and interpersonal skills. Proficiency in frameworks such as NIST and ISO/IEC 27001 is essential for designing robust security programs. Advisors must also master threat modeling, vulnerability assessment, and risk management.
Key skills include:
- Analytical thinking and creative problem-solving
- Strong communication for translating technical risks to business leaders
- Leadership and the ability to influence across departments
- Stakeholder engagement and relationship building
For example, during an incident response, clear advisor communication can streamline containment efforts, reduce confusion, and minimize business impact. This blend of technical depth and soft skills sets top advisors apart in the field.
Industry Demand and Career Outlook
Demand for cybersecurity advisor roles continues to grow as organizations face more frequent and complex attacks. Reports by ISC2 and the Bureau of Labor Statistics highlight a projected surge in cybersecurity jobs, particularly in finance, healthcare, and government.
Salary ranges for advisors are competitive, reflecting the critical nature of the position and the specialized skill set required. Career advancement opportunities abound, from senior advisory roles to CISO positions. As organizations adopt cloud, IoT, and remote work models, advisory roles are evolving to address new security challenges and business needs.
Insights from leading workforce studies confirm that the cybersecurity advisor is one of the most sought-after roles in the industry, offering both job security and diverse career paths.
Common Challenges and How to Overcome Them
Cybersecurity advisors face several challenges, such as adapting to rapidly evolving threats and shifting regulatory landscapes. Organizational resistance to new security initiatives and limited budgets can also hinder progress.
Balancing deep technical knowledge with business alignment is often a hurdle. One effective strategy is to present security investments in terms of risk reduction and business value, making a compelling case to decision-makers. For example, when faced with budget constraints, advisors can prioritize high-impact projects and leverage free or open-source tools.
By remaining adaptable and solution-focused, advisors overcome obstacles and drive lasting improvements in organizational security.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Essential Skills and Certifications for Cybersecurity Advisors
Building a successful cybersecurity advisor career requires a balanced mix of technical expertise, recognized credentials, and strong interpersonal abilities. Staying current with industry trends and maintaining a commitment to ongoing development is equally important. Let us break down the essential skills and certifications every cybersecurity advisor needs to thrive.
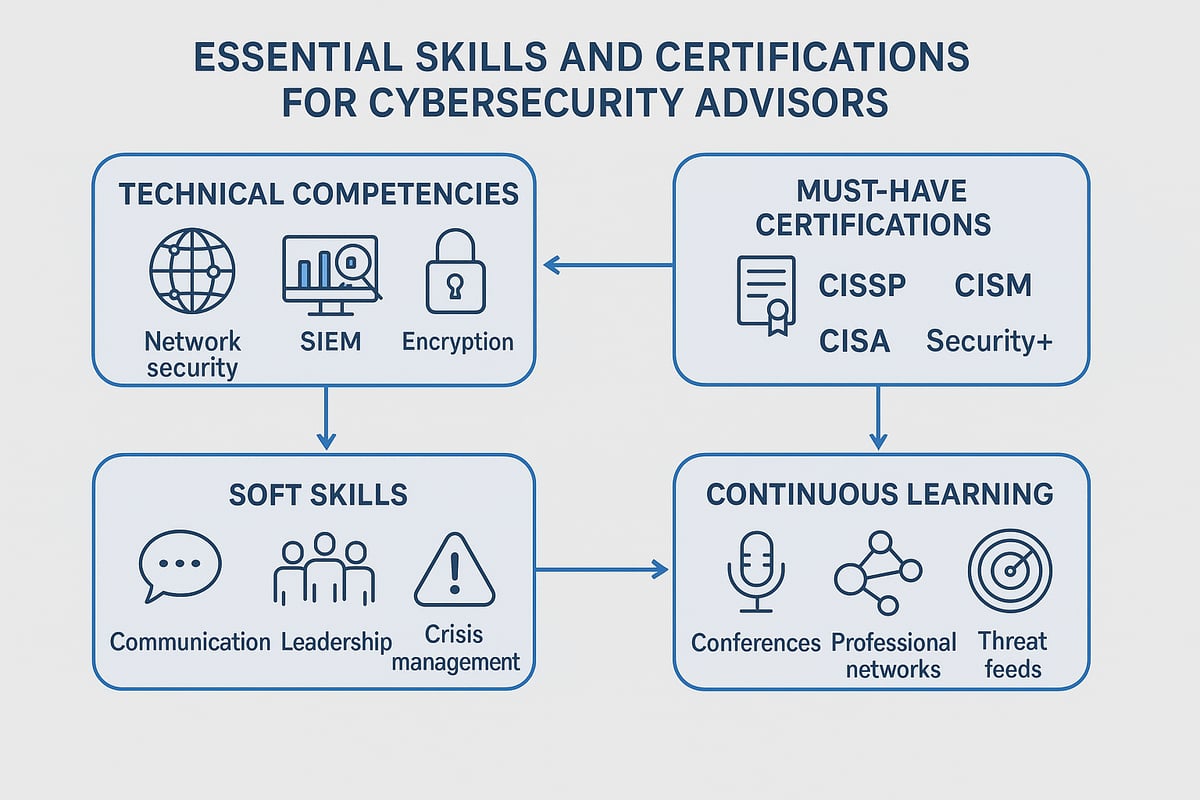
Core Technical Competencies
A cybersecurity advisor must demonstrate mastery across a range of foundational technologies. Proficiency in network security, endpoint protection, and identity management is essential. Familiarity with SIEM solutions, EDR platforms, and vulnerability scanning tools enables deep visibility into threats.
Key technical competencies include:
- Network segmentation and firewall configuration
- Endpoint protection and mobile device security
- Identity and access management protocols
- Encryption standards and secure key management
- Hands-on experience with SIEM and EDR tools
A cybersecurity advisor’s technical depth often determines how effectively they can prevent and respond to incidents. For example, an advisor who implemented robust SIEM monitoring once detected suspicious activity early, helping the organization avoid a major data breach.
Must-Have Certifications
Certifications validate a cybersecurity advisor’s expertise and signal commitment to excellence. The most respected credentials include CISSP, CISM, and CISA, each requiring a combination of experience, study, and examination. Specialized options such as CompTIA Security+, CEH, and cloud security certifications address emerging needs.
Benefits of leading certifications:
| Certification | Focus Area | Key Benefit |
|---|---|---|
| CISSP | Security leadership | Broad recognition |
| CISM | Risk management | Managerial focus |
| CISA | Auditing, compliance | Governance expertise |
| Security+ | Entry-level foundation | Accessible starting point |
Ongoing renewal and continuing education are critical, as technology and threats evolve rapidly. According to recent studies, certification holders often earn higher salaries and advance faster. For a comprehensive overview of the most valuable credentials, see the Cybersecurity Certifications Guide.
Critical Soft Skills and Leadership Abilities
Success as a cybersecurity advisor depends as much on interpersonal skills as on technical knowledge. Communicating complex risks in clear language to non-technical stakeholders is vital. Influencing executive decision-makers and building consensus across teams requires emotional intelligence and leadership.
Key soft skills to develop:
- Clear, persuasive communication
- Influencing and negotiating with executives
- Crisis management and rapid decision-making
- Analytical thinking and creative problem-solving
- Building trust and professional credibility
During a ransomware incident, one cybersecurity advisor’s calm leadership and clear updates enabled the company to recover quickly and maintain client confidence.
Keeping Skills Up to Date
Continuous learning is non-negotiable for the modern cybersecurity advisor. Attending conferences, participating in webinars, and subscribing to threat intelligence feeds help professionals stay ahead. Leveraging professional networks and joining industry groups provide access to new insights, tools, and best practices.
The cybersecurity advisor who invests in ongoing development remains relevant and effective, no matter how the threat landscape shifts.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Building Your Cybersecurity Advisor Career Roadmap
Charting a successful path as a cybersecurity advisor requires a clear strategy and ongoing commitment. By following this step-by-step roadmap, you can build expertise, credibility, and leadership in the field.
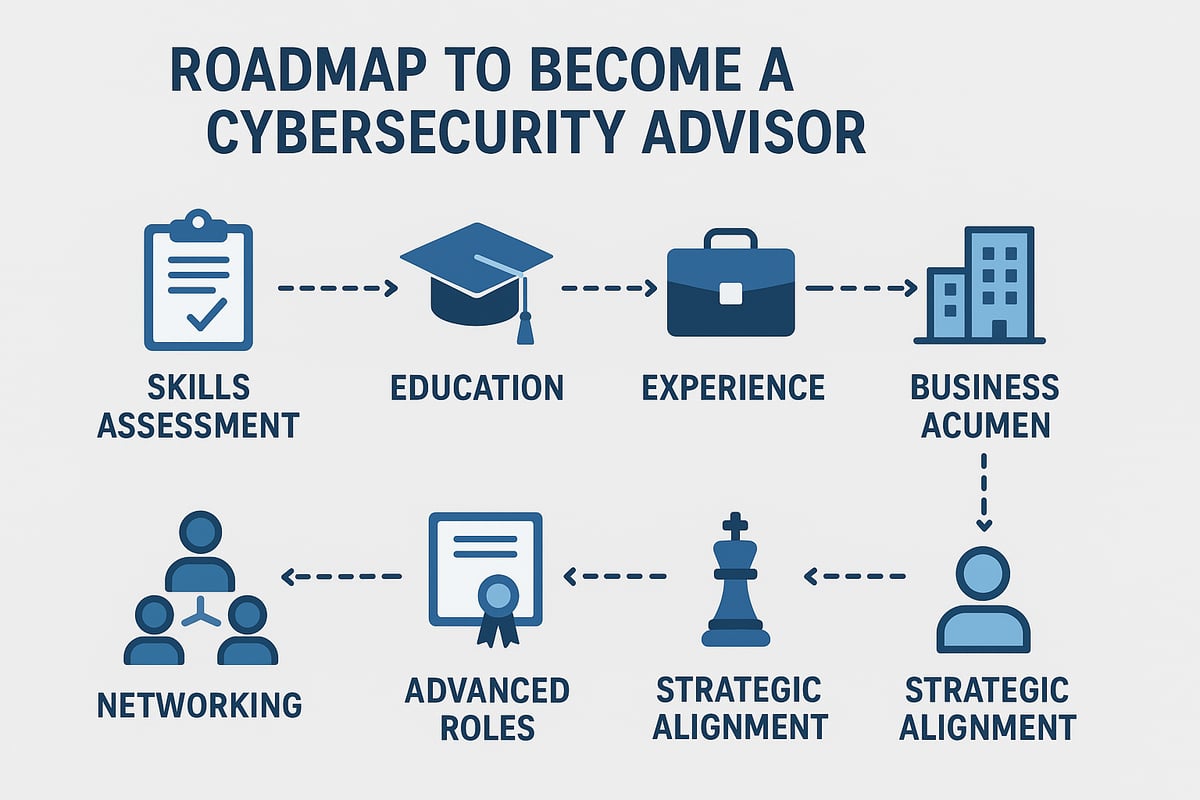
Step 1: Assess Your Current Skills and Experience
Begin your journey by honestly evaluating your technical and soft skills. List your strengths and identify areas that need improvement. Set realistic goals to bridge these gaps. This self-assessment ensures you focus your efforts where they matter most for a cybersecurity advisor.
Step 2: Obtain Relevant Education and Certifications
Decide whether a degree program or a bootcamp aligns with your learning style and career objectives. Prioritize certifications that match your desired cybersecurity advisor roles, such as CISSP or CISM. These credentials validate your expertise and signal commitment to employers.
Step 3: Gain Practical Experience
Start with entry-level positions like security analyst or IT support to build foundational knowledge. Seek internships, volunteer opportunities, or lab simulations to apply your skills in real-world settings. As you progress, create a portfolio documenting security projects and case studies. Many cybersecurity advisor professionals transition from IT support by demonstrating practical problem-solving.
Step 4: Develop Strategic and Business Acumen
Understand your organization’s risk appetite and business goals. Learn to articulate the return on investment for security initiatives, making your recommendations more persuasive. Strategic thinking helps you align security with broader business priorities.
Step 5: Build a Professional Network and Personal Brand
Engage with cybersecurity communities, both online and in person, to expand your network. Present at conferences, publish articles, or contribute to open-source projects. Building your reputation as a trusted cybersecurity advisor opens doors to new opportunities and collaborations.
Step 6: Pursue Advanced Roles and Continuous Improvement
Seek mentorship and aim for advanced certifications as you gain experience. Prepare for leadership positions such as CISO or vCISO, setting long-term career milestones. For deeper insight into evolving advisory roles, explore the Fractional CISO advisory guide.
Strategic Technology Alignment with CTO Input
For organizations and advisors seeking expert guidance in aligning technology and cybersecurity with core goals, CTO Input provides seasoned fractional CTO, CIO, and CISO leadership. CTO Input tailors technology roadmaps and security audits to your unique needs, helping the cybersecurity advisor turn security into a business advantage.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com.
Tools, Frameworks, and Best Practices for Cybersecurity Advisors
A successful cybersecurity advisor relies on a robust toolkit, proven frameworks, and practical best practices. Mastering these elements enables advisors to deliver measurable security improvements and protect organizations from evolving threats.
Essential Tools and Technologies
Every cybersecurity advisor must be proficient in industry-standard tools. Security Information and Event Management (SIEM) platforms provide centralized monitoring and analytics, helping detect threats quickly. Intrusion Detection and Prevention Systems (IDS/IPS) are vital for identifying unauthorized activity, while vulnerability scanners automate the discovery of system weaknesses.
Cloud security platforms safeguard distributed environments, and endpoint protection solutions defend against malware and ransomware. Automation and orchestration tools streamline incident response, reducing manual workloads. For example, a cybersecurity advisor using SIEM analytics can uncover insider threats by correlating access patterns and unusual behavior across the network.
Staying current with emerging tools ensures that a cybersecurity advisor can respond rapidly to new attack vectors and support business operations securely.
Security Frameworks and Standards
Advisors must ground their recommendations in recognized security frameworks. The NIST Cybersecurity Framework, ISO/IEC 27001, and CIS Controls each offer structured approaches to risk management and security governance. These frameworks help a cybersecurity advisor align security measures with organizational needs and compliance obligations.
A practical approach is mapping framework requirements to specific business processes, ensuring both regulatory alignment and operational efficiency. Many organizations adopt the NIST Cybersecurity Framework Overview to guide their security programs and demonstrate maturity during audits.
By leveraging these standards, a cybersecurity advisor can deliver consistent, repeatable, and defensible security improvements across industries.
Best Practices for Effective Advisory
Effective cybersecurity advisors take a risk-based approach to security recommendations. This means prioritizing controls based on the likelihood and impact of threats. Building security awareness and training programs helps foster a proactive security culture across all levels of the organization.
Regular security assessments and penetration testing are essential for uncovering vulnerabilities before attackers do. Documenting policies and procedures ensures accountability and consistency. For a deeper dive into strategic approaches, review cybersecurity strategy best practices which offer actionable guidance for advisors leading security transformation.
Implementing a strong governance model enables the cybersecurity advisor to manage risk, enforce compliance, and track progress effectively.
Measuring Impact and Success
A cybersecurity advisor must define clear KPIs and metrics to measure program effectiveness. Regularly reporting outcomes to stakeholders builds trust and secures ongoing support. Continual improvement cycles, including lessons learned from incidents and audits, ensure that security programs evolve alongside the threat landscape.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com
Navigating Emerging Threats and Future Trends
Staying ahead of emerging threats is essential for every cybersecurity advisor. The security landscape shifts rapidly, introducing new risks and requiring advisors to adapt quickly. To remain effective, advisors must understand evolving threats, leverage advanced technologies, address regulatory shifts, and prepare for future challenges.
Evolving Threat Landscape
The threat landscape is growing more complex each year. Cybersecurity advisor roles now require vigilance against ransomware, supply chain attacks, and insider threats. Recent data highlights significant increases in phishing and social engineering incidents, as seen in the Verizon DBIR.
Advisors must lead proactive risk assessments and swift incident response. For example, when a global supply chain attack struck a leading manufacturer, the cybersecurity advisor coordinated real-time detection, containment, and recovery. This hands-on leadership reduced downtime and financial loss, emphasizing the advisor’s critical role in modern organizations.
The Rise of AI and Automation in Cybersecurity
Artificial intelligence and automation are transforming how a cybersecurity advisor detects and responds to threats. AI-driven tools can identify zero-day exploits, analyze vast data sets, and automate repetitive security tasks.
However, selecting the right AI solutions is complex. Advisors can benefit from frameworks like the Cybersecurity AI Agent Selection Framework, which helps organizations evaluate and implement AI tools effectively. By staying informed about emerging technologies, advisors strengthen defenses and optimize security operations.
Regulatory and Compliance Changes
As regulations shift globally, a cybersecurity advisor must guide organizations through compliance with data privacy laws such as GDPR, CCPA, and HIPAA. These frameworks create new organizational responsibilities and require rigorous audit preparation.
Navigating this landscape demands up-to-date knowledge of compliance services and best practices. Resources like cybersecurity compliance services provide practical guidance for advisors managing complex regulatory requirements. Advisors who master compliance position themselves as indispensable partners to executive leadership.
Preparing for the Future
To stay resilient, every cybersecurity advisor should focus on adaptability. The rise of remote work, cloud adoption, IoT, and DevSecOps requires continuous upskilling and strategic foresight.
Building expertise in emerging technologies and maintaining strong professional networks will help advisors anticipate new risks. By embracing lifelong learning and proactive planning, advisors ensure they are ready for whatever the future holds.
Visit https://www.ctoinput.com to learn more and connect with a member of the CTO Input team.
Spend a few minutes exploring the rest of the articles on the CTO Input blog at https://blog.ctoinput.com.
As you look to chart your path as a cybersecurity advisor, remember that turning expertise into real-world impact takes more than just technical know how—it’s about building confidence, clarity, and alignment between your skills and your organization’s goals. If you’re ready to take the next step—whether you want an honest assessment of your technology health, a sounding board for your top challenges, or a clear path forward—I invite you to Schedule a call, Book a 30 minute discovery call, Get a technology health check, Talk through your top 3 challenges, Get clarity and next steps. Let’s make your technology work for you.